Abstract
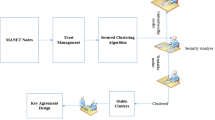
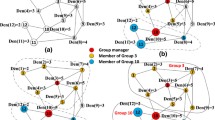
This research presents an improved hierarchical key management scheme (IHKMS) with three phase technique for secure group communications in Mobile Ad-hoc Networks (MANETs). It extends two previously proposed models named enhanced hierarchical key agreement scheme (EHKMS) and EHKMS with three phase technique which suffer from two main problems. The first one which exists in both models is that, the main subgroup controller (L1-head) is heavily loaded and has a lot of responsibilities which may lead to its failure. The second problem that exists only in EHKMS is intrusion attacks which may appear in two aspects; frank intrusion and selfish attack. This problem is a fatal one which threatens the security of the system. The proposed IHKMS with three phase technique solves the above mentioned problems. First, it decreases the memory load on the main subgroup header to save its memory resources by distributing a major part of subgroup keys storage into the second level of subgroups headers. Second, it immunizes the IHKMS against intrusions by employing the three phase technique. Applying the three phase technique integrates a certification authentication system in addition to the hierarchal key system used in the IHKMS. The proposed IHKMS with three phase technique enhances EHKMS and EHKMS with three phase technique. It improves the system’s reliability in EHKMS, and EHKMS with three phase technique by minimizing the subgroup header’s load. Also, it overcomes the intrusion problem that exists only in EHKMS. On the other hand, the complexity of the proposed IHKMS with three phase technique is higher than that of EHKMS. This is anticipated result as the proposed model integrates the three phase technique with the IHKMS.









Similar content being viewed by others
References
Elaskily, M. A., Kelash, H. M., & Faragallah, O. S. (2012). An enhanced hierarchical key management scheme for MANETs. Wireless Personal Communication, 72, 1783–1800. doi:10.1007/s11277-012-0910-1.
Cheng, Y., Huang, C., & Shi, W. (2007). Trusted dynamic source routing protocol. In Proceedings of IEEE international conference on wireless communications, networking and mobile computing (pp. 1632–1636).
Marti, S., Giuli, T. J., Lai, K., & Baker, M. (2000) Mitigating routing mis-behavior in mobile ad hoc networks. In Proceedings of 6th annual international conference on mobile computing and networking (pp. 255–265).
Buchegger, S., & Le Boudec, J. Y. (2002) Performance analysis of the CONFIDANT protocol (Cooperation Of Nodes: Fairness In Dynamic Adhoc NeTwork). In Proceedings of international IEEE conference on mobile ad hoc networking and computing.
Miranda, H., & Rodrigues, L. (2005). Preventing selfishness in open mobile ad hoc networks. In Proceedings of international IEEE conference on wireless communication and networking
Madhavi, S., & Kim, T. H. (2008). An intrusion detection system in mobile adhoc networks. In Proceedings of international journal of security and its applications (vol. 2, no. 3).
Balakrishnan, K., Deng, J., & Pramod, V. K. (2005). TWOACK: Preventing selfishness in mobile ad hoc networks. In Proceedings of international IEEE conference on wireless communication and networking.
Al-Roubaiey, A., Sheltami, T., Mahmoud, A., Shakshuki, E. & Mouftah, H. (2010) AACK: Adaptive acknowledgment intrusion detection for MANET with node detection enhancement. In Proceedings of 24th international IEEE conference on advanced information networking and applications.
Arya, K. V., Vashistha, P. & Gupta, V. Three phase technique for intrusion detection in mobile ad hoc network. In Proceedings of Wireless Personal Communication (pp. 675–684).
Huang, D. & Medhi, D. (2007). A secure key management scheme for hierarchical mobile ad hoc networks. Elsevier’s Ad Hoc Networks, 6(4), 560–577.
Mobile Ad hoc Network. http://en.wikipedia.org/wiki/Mobile_ad_hoc_network.
Mobile Ad Hoc Networking (MANET). http://cs.itd.nrl.navy.mil/work/manet/index.php.
Dynamic Source Routing Protocol. http://en.wikipedia.org/wiki/DynamicSourceRouting.
Xenakis, C., Panos, C., & Stavrakakis, I. (2011). A comparative evaluation of intrusion detection architectures for mobile ad hoc networks. Computers & Security, 30, 63–80.
Soliman, H. H., Hikal, N. A., & Sakr, N. A. (2012). A comparative performance evaluation of intrusion detection techniques for hierarchical wireless sensor networks. Egyptian Informatics Journal, 13, 225–238.
Sen, J., Ukil, A., Bera, D., & Arpan Pal. A distributed intrusion detection system for wireless ad hoc networks. In Proceeding og 16th IEEE international conference on networks (ICON 2008), New Delhi, 12–14 Dec (pp. 1–6).
Mitchell, R., & Chen, I.-R. (2014). A survey of intrusion detection in wireless network applications. Computer Communications, 42, 1–23.
Di Pietro, R., Guarino, S., Verde, N. V., & Domingo-Ferrer, J. (2014). Security in wireless ad-hoc networks—A survey. Computer Communications, 51, 1–20.
Nadeem, A., & Howarth, M. P. (2014). An intrusion detection & adaptive response mechanism for MANETs. Ad Hoc Networks, 13, 368–380.
Sen, S., & Clark, J. A. (2011). Evolutionary computation techniques for intrusion detection in mobile ad hoc networks. Computer Networks, 55, 3441–3457.
Mishra, A., Nadkarni, K., & Patcha, A. (2004). Intrusion detection in wireless ad hoc networks. IEEE Wireless Communications, 11(1), 48–60.
Sen, S., & Clark, J. A. (2009). Intrusion detection in mobile ad hoc networks, Chapter 17 (pp. 427–454). Heidelberg: Springer.
Sun, B., Osborne, L., Xiao, Y., & Guizani, S. (2007). Intrusion detection techniques in mobile ad hoc and wireless sensor networks. IEEE Wireless Communications, 14(5), 56–63.
Komninos, N., & Douligeris, C. (2009). LIDF: Layered intrusion detection framework for ad-hoc networks. Journal of Ad Hoc Networks, 7, 171–182.
Cho, J.-H., & Chen, I.-R. (2011). Performance analysis of hierarchical group key management integrated with adaptive intrusion detection in mobile ad hoc networks. Journal of Performance Evaluation, 68, 58–75.
El-Zoghdy, S. F., & Asem, Y. M. (2011). Secure group re-keying using key inverses. Journal of High Speed Networks, 18(1), 47–68.
Mitrokotsa, A., Komninos, N., & Douligeris, C. (2007). Intrusion detection & response in ad-hoc networks. In Advances in Ad Hoc Network Security, International Journal on Computer Research (vol. 15, pp. 23–55). Nova Science Publishing Inc.
Cao, J., Liao, L., & Wang, G. (2006). Scalable key management for secure multicast communication in the mobile environment. Pervasive and Mobile Computing, 2(2), 187–203.
Jun, Z., Yo, Z., Fanyuan, M., Dawu, G., & Yingcai, B. (2006). An extension of secure group communication using key graph. Elsevier’s Information Sciences, 176, 3060–3078.
Ng, W. H. D., Howarth, M., Sun, Z., & Cruickshank, H. (2007) Dynamic balanced key tree management for secure multicast communications. IEEE Computers Transactions, 56(5), 590–605.
Peyravian, M., Matyas, S. M., & Zunic, N. (1999). Decentralized group key management for secure multicast communications. Elsevier’s Computer Communications, 22, 1183–1187.
Rafaeli, S., & Hutchinson, D. (2003). A survey of key management for secure group communication. ACM Computing Surveys, 35(3), 309–329.
Chan, X., Ma, B. N. W., & Yang, C. (2007). M-CLIQUES: Modified CLIQUES key agreement for secure multicast. Elsevier’s Computers and Security, 26, 138245.
Jacoby, G. A., & Davis, N. J. (2007). Mobile host-based intrusion detection and attack identification. IEEE Wireless Communications, 14(4), 53–60.
Lauf, A., Peters, R. A., & Robinson, W. H. (2010). A distributed intrusion detection system for resource-constrained devices in ad hoc networks. Ad Hoc Networks, 8(3), 253–266.
Alrajeh, N. A., Khan, S., & Shams, B. (2013). Intrusion detection systems in wireless sensor networks: A review. International Journal of Distributed Sensor Networks,. doi:10.1155/2013/167575.
Wang, W., Man, H., & Liu, Y. (2009). A framework for intrusion detection systems by social network analysis methods in ad hoc networks. Wiley Security and Communication Networks, 2(6), 669–685.
Razak, S. A., Furnell, S. M., Clarke, N. L., & Brooke, P. J. (2008). Friend-assisted intrusion detection and response mechanisms for mobile ad hoc networks. Ad Hoc Networks, 6(7), 1151–1167.
Ma, C., & Fang, Z. (2009). A novel intrusion detection architecture based on adaptive selection event triggering for mobile ad-hoc networks. In Proceedings of IEEE 2nd international symposium on intelligent information technology and security informatics (pp. 198–201), January 2009.
Elboukhari, M., Azizi, M., & Azizi, A. (2015). Intrusion detection systems in mobile ad hoc networks: state of the art. International Journal on Computational Sciences & Applications (IJCSA), 5(2), 27–36.
Wang, N., & Fang, S. (2007). A hierarchical key management scheme for secure group communications in mobile ad hoc networks. Journal of Systems and Software, 80(10), 1667–1677.
Pieprzyk, J., & Li, C.-H. (2000). Multiparty key agreement protocols. IEE Proceedings Computers and Digital Techniques, 147(4), 229–236.
Elaskily, M. A. (2013). Investigation of security techniques for mobile ad hoc networks. MSc Thesis, Department of Computer Science and Engineering, Faculty of Electronic Engineering, Menoufia University.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Faragallah, O.S., El-Zoghdy, S.F. Improved Hierarchical Key Management Scheme (IHKMS) with Three Phase Technique for Ad-Hoc Networks. Wireless Pers Commun 91, 1297–1319 (2016). https://doi.org/10.1007/s11277-016-3529-9
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-016-3529-9