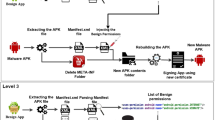
Abstract
In this paper obfuscation techniques used by novel malwares presented and compared. IAT smashing, string encryption and dynamic programing are explained in static methods and hooking at user and kernel level of OS with DLL injection, modifying of SSDT and IDT table addresses, filter IRPs, and possessor emulation are techniques in dynamic methods. This paper suggest Approach for passing through malware obfuscation techniques. In order that it can analyze malware behaviors. Our methods in proposed approach are detection presence time of a malware at user and kernel level of OS, dumping of malware executable memory at correct time and precise hook installing. Main purpose of this paper is establishment of an efficient platform to analyze behavior and detect novel malwares that by use of metamorphic engine, packer and protector tools take action for obfuscation and metamorphosis of themself. At final, this paper use a dataset embeds different kind of obfuscated and metamorphic malwares in order to prove usefulness of its methods experiments. Show that proposed methods can confront most malware obfuscation techniques. It evaluated success rate to unpacking, obfuscated malwares and it shows 85% success rate to recognize kernel level malwares.








Similar content being viewed by others
Notes
Dalvik Execution.
Portable Executable.
Import Address Table.
Export Address Table.
Common Language Runtime.
System Service Descriptor Table.
I/O Request Packet.
Interrupt Descriptor Table.
Kernel Path Protection.
Callback Functions.
Callout Functions.
Windows Filtering Platform.
References
AV-Test - Malware statics and trends report, https://www.av-test.org/en/statistics/malware. Accessed 2016.
Gandotra, E., Bansal, D., & Sofat, S. (2014). Malware analysis and classification: A survey. Journal of Information Security, 5, 56–64.
Jung, J. H., Kim, J. Y., Lee, H. C., & Yi, J. H. (2013). Repackaging attack on android banking applications and its countermeasures. Journal of Wireless Personal Communication, 73(4), 1421–1437.
Lu, H., Zhao, B., Sue, J., & Xie, P. (2013). Generating lightweight behavioral signature for malware detection in people-centric sensing. Journal of Wireless Personal Communication, 75(3), 1591–1609.
Gupta, S., & Kumar, P. (2014). An immediate system call sequence based approach for detecting malicious program executions in cloud environment. Journal of Wireless Personal Communication, 81(1), 405–425.
Bayer, U., Kruegel, C., & Kirda, E. (2006). TTAnalyze: A Tool for Analyzing Malware, M.Sc. Thesis, University of Vienna.
Schultz, M., Eskin, E., Zadok, F., & Stolfo, S. (2001). Data mining methods for detection of new malicious executables. In Proceedings of 2001 IEEE symposium on security and privacy (pp. 38–49). Oakland.
Siddiqui, M., Wang, M. C., & Lee, J. (2009). Detecting internet worms using data mining techniques. Journal of Systemics, Cybernetics and Informatics, 6, 48–53.
Gao, D., Yin, G., Dong, Y., & Kou, L. (2013). A research on the heuristic signature virus detection based on the PE structured. In Proceedings of international conference on electric and electronics (EEIC).
Javaheri, D., & Parsa, S. (2014). A malware detection method based on static analysis of PE structure. Journal of Advanced Defense Science and Technology, Imam Hossein University, 2(3), 187–201.
Sikorski, M., & Honig, A. (2012). Practical malware analysis (pp. 21–26). William Pollock Publisher.
Ilsun, Y., & Kangbin, Y. (2010). Malware obfuscation techniques: A brief survey. In Proceedings of international conference on broadband, wireless computing, communication and applications (pp. 297–300). Fukuoka, Japan.
Xie, X., Lu, B., Gong, D., Luo, X., & Liu, F. (2016). Random table and hash coding-based binary code obfuscation against stack trace analysis. Journal of IET Information Security, 10, 18–27.
Pang, S., Komosny, D., Zhu, L. Zhang, R., Sharrafzadeh, A., Ban, T., & Inoue, D. (2016). Malicious events grouping via behavior based Darknet traffic flow analysis. Journal of Wireless Personal Communication, 1–19. doi:10.1007/s11277-016-3744-4.
Jung, H. M., Lee, H. G., & Choi, J. W. (2017). Efficient malicious packet capture through advanced DNS sinkhole. Journal of Wireless Personal Communication, 93(1), 21–34. doi:10.1007/s11277-016-3443-1.
Ghiasi, M., Sami, A., Salehi, Z. (2012). Dynamic malware detection using registers values set analysis. In Proceedings of 9th international ISC conference on information security and cryptology (ISCISC) (pp. 54–59).
Zolkipli, M. F., & Jantan, A. (2011). An approach for malware behavior identification and classification. In Proceedings of 3rd international conference on computer research and development (pp. 191–194). Shanghai, China.
Rieck, K., Trinius, P., Willems, C., & Holz, T. (2011). Automatic Analysis of Malware Behavior Using Machine Learning. Journal of Computer Security, 19, 639–668.
Tian, R., Islam, M. R., Batten, L., & Versteeg, S. (2010). Differentiating malware from clean wares using behavioral analysis. In Proceedings of 5th international conference on malicious and unwanted software (malware) (pp. 23–30). Nancy, France.
Huda, S., Abawajy, J., Alazab, M., Abdollalihian, M., Islam, R., & Yearwood, J. (2016). Hybrids of support vector machine wrapper and filter based framework for malware detection. Journal of Future Generation Computer Systems, 55, 376–390.
Russinovich, M., Solomon, D., & Ionescu, A. (2012). Windows internals part 1 (6th ed., pp. 133–138). Microsoft Press.
Hoglund, G., & Butler, J. (2005). Rootkits: Subverting the windows kernel (pp. 82–83, 270–274). Addison Wesley Professional.
Priyadarshi, S. (2011). Metamorphic detection via emulation, M.Sc. Thesis, Jose State University.
Mohammadzadeh Lajevardi, A. (2013). Design and implementation of a behavior-based method for malware detection, M.Sc. Thesis, Iran University of Science and Technology, Tehran, Iran.
Gooran Ourimi, A. (2014). Propose an optimal and transparent framework for automatic malware analysis, M.Sc. Thesis, Iran University of Science and Technology, Tehran, Iran.
Ball, T., Bounimova, E., Cook, B., Levin, V., Lichtenberg, J., McGarvey, C., Ondrusek, B., Rajamani, S., & Ustuner, A. (2006). Thorough static analysis of device drivers, ‘ACM SIGOPS operating systems review’. In Proceedings of ACM SIGOPS/EuroSys European conference on computer systems (Vol. 40, Issue No. 4, pp. 73–85). New York, USA.
Virus Sign Malware Data Base, http://www.virussign.com. Accessed 2014.
Adminus Malware Database, http://www.adminus.net. Accessed 2015.
Virus Share Malware Database, http://www.virusshare.com. Accessed 2015.
Reeves, R. D. (2010). Windows 7 Device Driver (pp. 106–110). Addison-Wesley Publisher.
Song, D., Heng Yin, D., Caballero, J., Jager, I., Kang, M. G., Liang, Z., et al. (2008). BitBlaze: A new approach to computer security via binary analysis. Journal of Information Systems Security, Springer, 5352, 1–25.
Blunden, B. (2012). The Rootkit Arsenal: Escape and evasion in the dark corners of the system (2nd ed., pp. 240–245). Jones and Bartlett Publishers.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Javaheri, D., Hosseinzadeh, M. A Framework for Recognition and Confronting of Obfuscated Malwares Based on Memory Dumping and Filter Drivers. Wireless Pers Commun 98, 119–137 (2018). https://doi.org/10.1007/s11277-017-4859-y
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-017-4859-y