Abstract
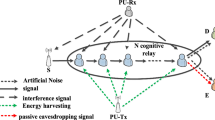
This paper investigates the physical layer security of an underlay cognitive radio network with relay selection scheme under threats of an eavesdropper. We consider a set of intermediate relays working in decode and forward mode. The relays harvest energy from radio frequency signal transmission of secondary user (SU) using a time switching relaying. We evaluate the secrecy outage probability (SOP) of secondary relay network assuming that the channel state information (CSI) of the interfering links from both the SU and relay transmitter to primary user (PU) receiver are imperfect. The transmit power of the SU as well as relay is controlled by the maximum tolerable interference at PU because of underlay environment and outage constraint of PU as demanded by quality of service of PU. The impact of several network parameters such as maximum tolerable interference threshold, number of relays, time for energy harvesting, imperfection in CSI and primary outage constraint on the secrecy outage of the SU network is indicated. The influence of relay selection scheme on SOP with energy harvesting and imperfect CSI is indicated.








Similar content being viewed by others
References
Mitola, J. (2000). Cognitive radio: An integrated agent architecture for software dened radio. Ph.D. Thesis, Stockholm.
Haykin, S. (2005). Cognitive radio: Brain-empowered wireless communications. IEEE Journal on Selected Areas in Communications, 23(2), 201–220.
Krikidis, I., Timotheou, S., & Sasaki, S. (2012). RF energy transfer for cooperative networks: Data relaying or energy harvesting? IEEE Communications Letters, 16(11), 1772–1775.
Zhang, Q., Jia, J., & Zhang, J. (2009). Cooperative relay to improve diversity in cognitive radio networks. IEEE Communications Magazine, 47(2), 111–117.
Varshney, L. R. (2008). Transporting information and energy simultaneously. In IEEE International symposium on information theory (Toronto). pp. 1612–1616.
Grover, P., & Sahai, A. (2010). Shannon meets Tesla: Wireless information and power transfer. In ISIT
Zhou, L., & Chao, H. C. (2011). Multimedia trafc security architecture for internet of things. IEEE Network, 25(3), 29–34.
Khisti, A., & Wornell, G. W. (2010). Secure transmission with multiple antennas Part I: The MISOME wiretap channel. IEEE Transactions on Information Theory, 56(7), 3088–3104.
Wyner, A. D. (1975). The wire-tap channel. Bell System Technical Journal, 54, 1355–1387.
Zou, Y., Wang, X., & Shen, W. (2013). Optimal relay selection for physical-layer security in cooperative wireless networks. IEEE Journal on Selected Areas in Communications, 31(10), 2099–2111. https://doi.org/10.1109/JSAC.2013.131011.
Krikidis, I., Thompson, J. S., McLaughlin, S., & Goertz, N. (2009). Max-min relay selection for legacy amplify-and-forward systems with interfer-ence. IEEE Transactions on Wireless Communications, 8(6), 3016–3027.
Xia, M., & Aïssa, S. (2015). Fundamental relations between reactive and proactive relay-selection strategies. IEEE Communications Letters, 19(7), 1249–1252.
Bletsas, A., Shin, H. D., & Win, M. Z. (2007). Cooperative communications with outage-optimal opportunistic relaying. IEEE Transactions on Wireless Communications, 6(9), 1–10.
Kirkidis, I. (2010). Opportunistic relay selection for cooperative networks with secrecy constraints. IET Communications, 4(15), 1787–1791.
Sakran, H., Shokair, M., Nasr, O., El-Rabaie, S., & El-Azm, A. A. (2012). Proposed relay selection scheme for physical layer security in cognitive radio networks. IET Communications, 6(16), 2676–2687. https://doi.org/10.1049/iet-com.2011.0638.
Do, N.T., Bao, V.N.Q., & An, B. (2015). A relay selection protocol for wireless energy harvesting relay networks. In 2015 International conference on advanced technologies for communications (ATC) (Ho Chi Minh City). pp. 243–247. https://doi.org/10.1109/ATC.2015.7388327
Prasad, B., Roy, S. D., & Kundu, S. (2014). Outage performance of cognitive relay network with imperfect channel estimation under proactive DF relaying. In Proceedings of IEEE national conference on communication (NCC) (IIT Kanpur). Feb 2014.
Nasir, A. A., Zhou, X., Durrani, S., & Kennedy, R. A. (2013). Relaying protocols for wireless energy harvesting and information processing. IEEE Transactions on Wireless Communications, 12(7), 3622–3636. https://doi.org/10.1109/TWC.2013.062413.122042.
Suraweera, H. A., Smith, P. J., & Shafi, M. (2010). Capacity limits and performance analysis of cognitive radio with imperfect channel knowledge. IEEE Transactions on Vehicular Technology, 59(4), 1811–1822.
Zhou, X., Zhang, R., & Ho, C. K. (2013). Wireless information and power transfer: Architecture design and rate-energy tradeoff. IEEE Transactions on Communications, 61(11), 4754–4767. https://doi.org/10.1109/TCOMM.2013.13.120855.
Zhang, X., Xing, J., Yan, Z., Gao, Y., & Wang, W. (2013). Outage performance study of cognitive relay networks with imperfect channel knowledge. IEEE Communications Letters, 17(1), 27–30.
Bloch, M., Barros, J., Rodrigues, M. R. D., & McLaughlin, S. W. (2008). Wireless information-theoretic security. IEEE Transactions on Information Theory, 54(6), 2515–2534.
Zou, Y., Wang, X., Shen, W., & Hanzo, L. (2014). Security versus reliability analysis of opportunistic relaying. IEEE Transactions on Vehicular Technology, 63(6), 2653–2661.
Acknowledgements
This research work is supported by ITRA of Media Lab Asia through sponsored project with Grant number ITRA/15(64)/Mobile/USEAADWN/01. Some part of this work was presented in international conference WPMC, Hyderabad, India on Dec, 2015.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Maji, P., Prasad, B., Roy, S.D. et al. Secrecy Outage of a Cognitive Radio Network with Selection of Energy Harvesting Relay and Imperfect CSI. Wireless Pers Commun 100, 571–586 (2018). https://doi.org/10.1007/s11277-017-5221-0
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-017-5221-0