Abstract
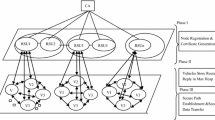
In the recent past information transmission through the vehicular ad hoc network (VANET) playing a vital role due to increase in accident statistics. There are numerous networking and VANET protocols helpful to control the trust while transmitting the data from source to destination nodes in traffic environment. In spite of many existing protocols for analyzing the trust in the network, the challenge of routing overhead, high energy consumption and malicious attacks issues still continue in the communication. This research introduces the trust collaboration nodes and Quality of Service (QoS) with energy multipath routing protocol for transmitting the information through VANET. Initially, the trusted nodes have been collected for analyzing the neighbouring nodes and the information are transmitted using the proposed QoS based energy efficient multipath routing protocol. During this transmission, the multi path protocol eliminates the intermediate attacks effectively when compared with the other existing protocols. The Proposed protocol maintains the QoS while routing the information from source to destination and further the efficiency has been analyzed through simulation experiments and Montgomery multiplier based Elliptic Curve Cryptography (ECC) will be used in future for better security and privacy.




Similar content being viewed by others
References
Mangrulkar, R. S., Chavan, P. V., & Dagadkar, S. N. (2010). Improving route selection mechanism using trust factor in AODV routing protocol for MaNeT. International Journal of Computer Applications, 36–39, 0975–8887.
Sehgal, A., Ahuja, R., & Kumari, S. (2011). A security architecture for mobile ad hoc networks. In Proceedings of the international conference on science and engineering (ICSE 2011). ISBN (Vol. 978, pp. 981-08).
Sen, J. (2010). A distributed trust management framework for detecting malicious packet dropping nodes in a mobile ad hoc network. arXiv preprint arXiv:1010.5176.
Sardar, M., & Majumder, K. (2014). A new trust based secure routing scheme in manet. In Proceedings of the international conference on frontiers of intelligent computing: Theory and applications (FICTA) 2013 (pp. 321–328). Cham: Springer.
Ye, M., Chan, E., Chen, G., & Wu, J. (2006, July). Energy efficient fractional coverage schemes for low cost wireless sensor networks. In 26th IEEE international conference on distributed computing systems workshops, 2006. ICDCS workshops 2006 (pp. 79–79). IEEE.
Hung, K. S., Lui, K. S., & Kwok, Y. K. (2007, March). A trust-based geographical routing scheme in sensor networks. In Wireless communications and networking conference, 2007. WCNC 2007. IEEE (pp. 3123–3127). IEEE.
Yi, S., Naldurg, P., & Kravets, R. (2001, October). Security-aware ad hoc routing for wireless networks. In Proceedings of the 2nd ACM international symposium on mobile ad hoc networking & computing (pp. 299–302). ACM.
Bar, R. K., Mandal, J. K., & Singh, M. M. (2013). QoS of MANet through trust based AODV routing protocol by exclusion of black hole attack. Procedia Technology, 10, 530–537.
Eissa, T., Razak, S. A., Khokhar, R. H., & Samian, N. (2013). Trust-based routing mechanism in MANET: Design and implementation. Mobile Networks and Applications, 18(5), 666–677.
Huang, J. W., Woungang, I., Chao, H. C., Obaidat, M. S., Chi, T. Y., & Dhurandher, S. K. (2011, December). Multi-path trust-based secure AOMDV routing in ad hoc networks. In Global telecommunications conference (GLOBECOM 2011), 2011 IEEE (pp. 1–5). IEEE.
Nagrath, P., & Bhardwaj, A. S. (2010). Authenticated routing protocol based on reputation system for adhoc networks. International Journal on Computer Science and Engineering (IJCSE), 2(9), 3095–3099.
Ye, M., Li, C., Chen, G., & Wu, J. (2005, April). EECS: An energy efficient clustering scheme in wireless sensor networks. In Performance, computing, and communications conference, 2005. IPCCC 2005. 24th IEEE International (pp. 535–540). IEEE.
Gong, B., Li, L., Wang, S., & Zhou, X. (2008, August). Multihop routing protocol with unequal clustering for wireless sensor networks. In Computing, communication, control, and management, 2008. ISECS International Colloquium on CCCM’08 (Vol. 2, pp. 552–556). IEEE.
Xue, F., & Kumar, P. R. (2004). The number of neighbors needed for connectivity of wireless networks. Wireless Networks, 10(2), 169–181.
Sarma Dhulipala, V. R., Kanaga chidambaresan, G. R., & Chandrasekaran, R. M. (2012). Lack of power avoidance: A fault classification based fault tolerant framework solution for lifetime enhancement and reliable communication in wireless sensor networks. Information Technology Journal, 11(6), 719.
Sarma Dhulipala, V. R., Chandrasekaran, R. M., & Prabakaran, R. (2009). Timing analysis and repeatability issues of mobile ad hoc networking application traffics in large scale scenarios. International Journal on Recent Trends in Engineering (IJRTE), 1(1), 463–467.
Baskar, S., Pavithra, S., & Vanitha, T. (2015, February). Optimized placement and routing algorithm for ISCAS-85 circuit. In 2015 2nd international conference on electronics and communication systems (ICECS) (pp. 958–964). IEEE.
Baskar, S. (2014, March). Error recognition and correction enhanced decoding of hybrid codes for memory application. In 2014 2nd International conference on devices, circuits and systems (ICDCS) (pp. 1–6). IEEE.
Baskar, S., & Sarma Dhulipala, V. R. (2016). Comparative analysis on fault tolerant techniques for memory cells in wireless sensor devices. Asian Journal of Research in Social Sciences and Humanities, 6(cs1), 519–528.
Acknowledgements
The authors would like to thank the TEQIP, Phase II for the funding to carry out the Research work from Anna University Chennai—Regional Office, BIT CAMPUS, Tiruchirappalli.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Baskar, S., Sarma Dhulipala, V.R. Collaboration of Trusted Node and QoS Based Energy Multi Path Routing Protocol for Vehicular Ad Hoc Networks. Wireless Pers Commun 103, 2833–2842 (2018). https://doi.org/10.1007/s11277-018-5965-1
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-018-5965-1