Abstract
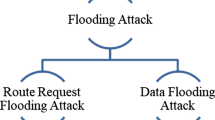
Due to their specific structure and plenty of their utilization, mobile ad-hoc networks are vulnerable to various attacks. An attack which impacts on network layer is referred to as flooding attack. By transmitting several packets, this attack occupies the processor so that it cannot receive the remaining data and packets. Hence, it causes disruption and disorder in the network. In this paper, for preventing this problem, a method has been proposed based on DSR routing protocol which quickly identifies the flooding attack. Indeed, the proposed method not only identifies and detects the malicious nodes in comparison with valid and proper nodes but also imposes sufficient penalties and reconsiders it again. The method proposed in this paper is called defending against flooding attacks-dynamic source routing. At the outset, it detects misbehavior in the network; then, for discovering malicious nodes, it uses average packet transmission RREQ which measures average transmission route request (RREQ) packets. The results of simulating the proposed method in NS-2 environment indicated that it improved packet delivery rate and end-to-end delay.






Similar content being viewed by others
References
Ghaffari, A. (2017). Real-time routing algorithm for mobile ad hoc networks using reinforcement learning and heuristic algorithms. Wireless Networks, 23, 703–714.
Asadi, E., & Ghaffari, A. (2016). A multicast routing protocol based on ODMRP with stable link in mobile ad hoc networks. International Journal of Computer Science and Information Security, 14, 68.
Ghaffari, A. (2015). Congestion control mechanisms in wireless sensor networks: A survey. Journal of Network and Computer Applications, 52, 101–115.
Azari, L., & Ghaffari, A. (2015). Proposing a novel method based on network-coding for optimizing error recovery in wireless sensor networks. Indian Journal of Science and Technology, 8, 859–867.
Mohammadi, R., & Ghaffari, A. (2015). Optimizing reliability through network coding in wireless multimedia sensor networks. Indian Journal of Science and Technology, 8, 834–841.
Ghaffari, A. (2014). Designing a wireless sensor network for ocean status notification system. Indian Journal of Science and Technology, 7, 809–814.
Chang, J.-M., Tsou, P.-C., Woungang, I., Chao, H.-C., & Lai, C.-F. (2015). Defending against collaborative attacks by malicious nodes in MANETs: A cooperative bait detection approach. IEEE Systems Journal, 9, 65–75.
Guo, Y., Gordon, S., & Perreau, S. (2007). A flow based detection mechanism against flooding attacks in mobile ad hoc networks. In Wireless communications and networking conference, 2007. WCNC 2007 (pp. 3105–3110). Washington: IEEE.
Verma, S. S., Patel, R., & Lenka, S. K. (2017). Analysing varying rate flood attack on real flow in MANET and solution proposal ‘real flow dynamic queue’. International Journal of Information and Communication Technology, 10, 276–286.
Faghihniya, M. J., Hosseini, S. M., & Tahmasebi, M. (2016). Security upgrade against RREQ flooding attack by using balance index on vehicular ad hoc network. Wireless Networks, 23(6), 1863–1874.
Sakiz, F., & Sen, S. (2017). A survey of attacks and detection mechanisms on intelligent transportation systems: VANETs and IoV. Ad Hoc Networks, 61, 33–50.
Kumar, S., & Dutta, K. (2017). Direct trust-based security scheme for RREQ flooding attack in mobile ad hoc networks. International Journal of Electronics, 104, 1034–1049.
Ahmed, M., Mahmood, A. N., & Hu, J. (2016). A survey of network anomaly detection techniques. Journal of Network and Computer Applications, 60, 19–31.
Yu, J., Kang, H., Park, D., Bang, H.-C., & Kang, D. W. (2013). An in-depth analysis on traffic flooding attacks detection and system using data mining techniques. Journal of Systems Architecture, 59, 1005–1012.
Hu, Y.-C., Johnson, D., & Maltz, D. (2004). The dynamic source routing protocol for mobile ad hoc networks (DSR). IETF Draft.
Kaur, T., Toor, A. S., & Saluja, K. K. (2014). Defending MANETs against flooding attacks for military applications under group mobility. In 2014 recent advances in engineering and computational sciences (RAECS), 2014 (pp. 1–6).
Gurung, S., & Chauhan, S. (2018). A novel approach for mitigating route request flooding attack in MANET. Wireless Networks, 24(8), 2899–2914.
Chaudhary, A., Tiwari, V., & Kumar, A. (2014). A novel intrusion detection system for ad hoc flooding attack using fuzzy logic in mobile ad hoc networks. In Recent advances and innovations in engineering (ICRAIE), 2014 (pp. 1–4).
Choudhury, P., Nandi, S., Pal, A., & Debnath, N. C. (2012). Mitigating route request flooding attack in MANET using node reputation. In 2012 10th IEEE international conference on industrial informatics (INDIN) (pp. 1010–1015).
Jiang, F.-C., Lin, C.-H., & Wu, H.-W. (2014). Lifetime elongation of ad hoc networks under flooding attack using power-saving technique. Ad Hoc Networks, 21, 84–96.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Mohammadi, P., Ghaffari, A. Defending Against Flooding Attacks in Mobile Ad-Hoc Networks Based on Statistical Analysis. Wireless Pers Commun 106, 365–376 (2019). https://doi.org/10.1007/s11277-019-06166-8
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-019-06166-8