Abstracts
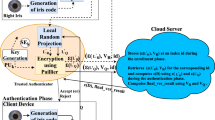
With the development of iris technology, iris identification has been widely used in various domains, as an efficient security authentication pattern. However, as more and more people have been involved in this authentication, they have begun to realize that this pattern may also lead to privacy leakage during the procedure of security authentication. For one thing, the adversary can reverse the iris information of the user with the unauthorized iris template and gets the privacy. For another, the adversary can also get the iris template from other poorly managed application and utilizes this template to access the user’s information in a special application to get the privacy of him. These two types of attack have seriously affected the promotion of iris identification. Thus, in order to cope with above attacks, and based on the conception of random projection and differential privacy protection, this paper proposes a novel privacy protection scheme short for RPDPP to protect the privacy of the user during the procedure of iris identification. In this scheme, a random projection is used in the phase of iris collection and template production, so that the iris template cannot be reversed into the iris information. Then before conserving the real template, several dummy templates that similar with the real iris template have been produced, and these dummies have disturbed the real template to comply with the restriction of ɛ-differential privacy. Thus, the real template of the user is difficult to be identified with other similar dummies, and the adversary cannot get the privacy of the user through multiple queries, even though he had obtained the iris template from other applications. At last, several experiments have been given with different parameters, and the protection ability has been compared with some similar algorithms, and then results of these experiments had further demonstrate the superiority of our proposed scheme.






Similar content being viewed by others
References
Marciniak, T., Dąbrowski, A., Chmielewska, A., & Krzykowska, A. A. (2014). Selection of parameters in iris recognition system. Multimedia Tools & Applications,68(1), 193–208.
Li, C., Zhou, W., & Yuan, S. (2015). Iris recognition based on a novel variation of local binary pattern. Visual Computer,31(10), 1419–1429.
Jillela, R. R., & Ross, A. (2015). Segmenting iris images in the visible spectrum with applications in mobile biometrics (pp. 4–16). Amsterdam: Elsevier.
Gunasekaran, K., Priya, S. A., Saravanan, D., & Akilan, P. (2014). Privacy preserving multimodal biometrics in online passport recognition. Biometrics & Bioinformatics,6(3), 94.
Uludag, U., Pankanti, S., Prabhakar, S., & Jain, A. K. (2004). Biometric cryptosystems: issues and challenges. Proceedings of the IEEE,92(6), 948–960.
Cimato, S., Gamassi, M., Piuri, V., Sassi, R., & Scotti, F. (2008). A Multi-biometric verification system for the privacy protection of iris templates. In International Workshop on Computational Intelligence in Security for Information Systems, Cisis’08, Genova, Italy.
Blundo, C., Cristofaro, E. D., & Gasti, P. (2011). EsPRESSo: Efficient privacy-preserving evaluation of sample set similarity. Journal of Computer Security,22(3), 355–381.
Maiorana, E., Campisi, P., & Neri, A. (2014). IRIS template protection using a digital modulation paradigm. In IEEE International Conference on Acoustics, Speech and Signal Processing.
Rathgeb, C., Breitinger, F., Busch, C., & Baier, H. (2014). On application of bloom filters to iris biometrics. Biometrics Iet, 3(4), 207–218.
Gupta, R., & Kumar, A. (2015). Hybrid protection mechanism to secure iris template. International Journal of advanced studies in Computer Science and Engineering, 4(3), 13–17.
Dwivedi, R., Dey, S., Singh, R., & Prasad, A. (2016). A privacy-preserving cancelable iris template generation scheme using decimal encoding and look-up table mapping. Computers & Security,65, 373–386.
Rathgeb, C., Tams, B., Wagner, J., & Busch, C. (2016). Unlinkable improved multi-biometric iris fuzzy vault. Eurasip Journal on Information Security,2016(1), 26.
Lai, Y. L., Jin, Z., Teoh, B. J., Goi, B. M., Yap, W. S., Chai, T. Y., et al. (2017). Cancellable iris template generation based on Indexing-First-One hashing. Pattern Recognition,64, 105–117.
Strzelczyk, P. (2011). Privacy preserving and secure iris-based biometric authentication for computer networks. Journal of Telecommunications & Information Technology, 4, 115–118.
Wong, K. S., & Kim, M. H. (2012). A privacy-preserving biometric matching protocol for iris codes verification. In Third FTRA international conference on mobile, ubiquitous, and intelligent computing.
Bringer, J., Chabanne, H., Favre, M., Patey, A., Schneider, T., & Zohner, M. (2014). GSHADE: Faster privacy-preserving distance computation and biometric identification. IH&MMSec ’14 Proceedings of the 2nd ACM workshop on Information hiding and multimedia security (pp. 187–198).
Barni, M., Droandi, G., & Lazzeretti, R. (2015). Privacy protection in biometric-based recognition systems: A marriage between cryptography and signal processing. Signal Processing Magazine IEEE,32(5), 66–76.
Rathgeb, C., Gomez-Barrero, M., Busch, C., Galbally, J., & Fierrez, J. (2015). Towards cancelable multi-biometrics based on bloom filters: a case study on feature level fusion of face and iris. In International workshop on biometrics and forensics.
Jegede, A., Udzir, N. I., Abdullah, A., & Mahmod, R. (2017). A secure and privacy preserving iris biometric authentication scheme with matrix transformation. In D. Choi, & S. Guilley (Eds.), Information Security Applications. WISA 2016. Lecture Notes in Computer Science (vol. 10144). Cham: Springer.
Dasgupta, S., & Gupta, A. (1999). An elementary proof of the Johnson-Lindenstrauss Lemma. Random Structures & Algorithms,22(1), 60.
Jassim, S., Al-Assam, H., & Sellahewa, H. (2009). Improving performance and security of biometrics using efficient and stable random projection techniques. In International symposium on image and signal processing and analysis.
Arriaga, R. I., & Vempala, S. (2006). An algorithmic theory of learning: robust concepts and random projection. In 1999 Symposium on Foundations of Computer Science.
Ping, X., Tianqing, Z., & Xiaofeng, W. (2014). A survey on differential privacy and applications. Chinese Journal of Computers,37(1), 101–122.
Xiaojian, Z., & Xiaofeng, M. (2014). Differential privacy in data publishcation and analysis. Chinese Journal of Computers,37(4), 927–949.
Dwork, C. (2006). Differential privacy. In Lecture notes in computer science (pp. 1–12).
Zhang, L., Ma, C., Yang, S., & Zheng, X. (2017). Probability indistinguishable: A query and location correlation attack resistance scheme. Wireless Personal Communications,97(4), 6167–6187.
Acknowledgements
This work was supported by University Nursing Program for Young Scholars with Creative Talents in Heilongjiang Province (Project Number: UNPYSCT-2017149, UNPYSCT-2017175). Basic scientific research service fee project of Heilongjiang provincial undergraduate universities (2018-KYYWF-0937); the Natural Science Fund of Heilongjiang Province for Outstanding Youth (YQ2019F018); the Special Doctor Scientific Research Fund Launch Project of Jiamusi University (Research on Privacy Protection of User Collaboration in Location Services).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Lei, Z., Lili, Y., Bin, W. et al. A Novel Privacy Protection Scheme for Iris Identification. Wireless Pers Commun 109, 2411–2425 (2019). https://doi.org/10.1007/s11277-019-06688-1
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-019-06688-1