Abstract
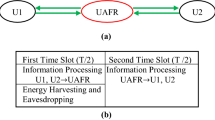
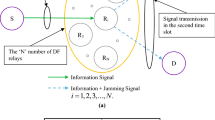
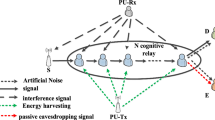
In this paper, we analyze the secrecy outage probability (SOP) of a cognitive cooperative radio network in a two-way communication in which two secondary source communicate with each other via multiple untrusted half-duplex amplify and forward relays in the absence of direct link. Due to the cognitive scenario, power is allocated to secondary nodes on the basis of outage constraint of the primary network. In the absence of direct link between two sources, communication completes in two time slots. In the first time slot, both of the sources broadcast the information signal and in the second time slot, a selected relay broadcasts the amplified information signals of both of the sources. Relays being untrusted, they can eavesdrop the message from the information signal. A particular relay, which maximizes the end-to-end secrecy capacity, is selected to broadcast the signal. The selected untrusted relay can only eavesdrop the message and other relays forcefully remain in idle condition. At the untrusted relay, information signals of both of the sources act as a jamming to each other. The selected untrusted relay harvests the energy using a power splitting ratio scheme. We observe the performance of the proposed model in terms of SOP. We find the optimal values of energy harvesting factor at which SOP becomes minimum. Several important parameters such as the impact of number of untrusted relays, primary transmit power, peak transmit power of secondary sources, threshold outage rate of primary receiver and threshold secrecy rate on SOP is indicated. An analytical expression for the SOP has been developed in a single integration form. Numerical results based on analytical expression are verified by MATLAB simulation.







Similar content being viewed by others
References
Barros, J., & Rodrigues, M. D. (2006) Secrecy capacity of wireless channels. In 2006 IEEE international symposium on information theory (vol. 1, pp. 356–360).
Liu, Y., Li, J., & Petropulu, A. P. (2013). Destination assisted cooperative jamming for wireless physical-layer security. IEEE Transactions on Information Forensics and Security, 8(4), 682–694.
Leung-Yan-Cheong, S. K., & Hellman, M. E. (1978). The Gaussian wire-tap channel. IEEE Transactions on Information Theory, 24(4), 451–456.
Sun, L., Zhang, T., Li, Y., & Niu, H. (2012). Performance study of two-hop amplify-and-forward systems with untrustworthy relay nodes. IEEE Transactions on Vehicular Technology, 61(8), 3801–3807.
Sun, L., Ren, P., Du, Q., Wang, Y., & Gao, Z. (2015). Security-aware relaying scheme for cooperative networks with untrusted relay nodes. IEEE Communications Letters, 19(3), 463–466.
Kalamkar, S. S., & Banerjee, A. (2017). Secure communication via a wireless energy harvesting untrusted relay. IEEE Transactions on Vehicular Technology, 66(3), 2199–2213.
Nguyen, B. V., & Kim, K. (2015). Secrecy outage probability of optimal relay selection for secure AnF cooperative networks. IEEE Communications Letters, 19(12), 2086–2089.
Pan, G., Tang, C., Li, T., & Chen, Y. (2015). Secrecy performance analysis for SIMO simultaneous wireless information and power transfer systems. IEEE Transactions on Communications, 63(9), 3423–3433.
Xiong, J., Cheng, L., Ma, D., & Wei, J. (2016). Destination-aided cooperative jamming for dual-hop amplify-and-forward MIMO untrusted relay systems. IEEE Transactions on Vehicular Technology, 65(9), 7274–7284.
Yao, R., Xu, F., Mekkawy, T., & Xu, J. (2016). Optimised power allocation to maximise secure rate in energy harvesting relay network. Electronics Letters, 52(22), 1879–1881.
Son, P. N., & Kong, H. Y. (2015). Cooperative communication with energy-harvesting relays under physical layer security. IET Communications, 9(17), 2131–2139.
Mamaghani, M. T., Kuhestani, A., & Wong, K. (2018). Secure two-way transmission via wireless-powered untrusted relay and external jammer. IEEE Transactions on Vehicular Technology, 67(9), 8451–8465.
Nasr, O., El-Rabaie, S., Sakran, H., El-Azm, A. A., & Shokair, M. (2012). Proposed relay selection scheme for physical layer security in cognitive radio networks. IET Communications, 6(16), 2676–2687.
Tang, C., Pan, G., & Li, T. (2014). Secrecy outage analysis of underlay cognitive radio unit over Nakagami-m fading channels. IEEE Wireless Communications Letters, 3(6), 609–612.
Zou, Y., Li, X., & Liang, Y.-C. (2014). Secrecy outage and diversity analysis of cognitive radio systems. IEEE Journal on Selected Areas in Communications, 32(11), 2222.
Tran, H., Zepernick, H. J., & Phan, H. (2013). Cognitive proactive and reactive df relaying schemes under joint outage and peak transmit power constraints. IEEE Communications Letters, 17(8), 1548–1551.
Zhong, B., & Zhang, Z. (2017). Secure full-duplex two-way relaying networks with optimal relay selection. IEEE Communications Letters, XX(X), 1–1.
Zhang, C., Ge, J., Li, J., Gong, F., & Ding, H. (2017). Complexity-aware relay selection for 5G large-scale secure two-way relay systems. IEEE Transactions on Vehicular Technology, 66(6), 5462–5466.
Khandaker, M. R. A., Wong, K.-K., & Zheng, G. (2017). Truth-telling mechanism for two-way relay selection for secrecy communications with energy-harvesting revenue. IEEE Transactions on Wireless Communications, 16(5), 1–1.
Acknowledgements
This research is supported by the Department of Electronics and Information Technology, Ministry of Communications and IT, Government of India under the Visvesvaraya Ph.D. Scheme administered by Media Lab Asia with Grant No. PhD-MLA/4(29)/2015-16.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Sharma, S., Roy, S.D. & Kundu, S. Two-Way Secure Communication with Multiple Untrusted Half-Duplex AF Relays. Wireless Pers Commun 110, 2045–2064 (2020). https://doi.org/10.1007/s11277-019-06829-6
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-019-06829-6