Abstract
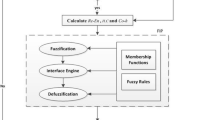
In mobile ad hoc network (MANET), the existing papers are two-level-hash technique reduces false positives however it does not verify the location and RSS information of the Sybil nodes. Also in multivariate verification technique, the Sybil attackers are detected using the difference between received beacon packet of RSS and its estimated claimed position. But chances of incorrect values are possible leading to misdetection. In this paper, the designing of fuzzy based collaborative verification system is proposed for Sybil attack detection in MANET. Using this method, if the source nodes want to communicate with a destination, it relies on the monitoring nodes that collaboratively exchange the details that include distance, angle and RSS difference with the two-hop neighbor nodes. Based on the collected information, it applies fuzzy logic decision to detect the lightly or heavily suspected node. Since the Sybil attack is confirmed by a collaborative exchange of monitoring nodes that have a chance for minimizing the false and miss detection. From the results, the overhead is minimized from overhearing all the nodes using the proposed technique.
















Similar content being viewed by others
References
Djenouri, D., Khelladi, L., & Badache, N. (2005). A survey of security issues in mobile ad hoc and sensor networks. IEEE Communications Surveys and Tutorials,7(4), 2–28.
Hoebeke, J., Moerman, I., Dhoedt, B., & Demeester, P. (2004). An overview of mobile ad hoc networks: Applications and challenges. Journal of Communications and Network,3(3), 60–66.
Chlamtac, I., Conti, M., & Liu, J. J. N. (2003). Mobile ad hoc networking: Imperatives and challenges. Ad Hoc Networks,1(1), 13–64.
Douceur, J. R. (2002). The Sybil attack. In P. Druschel, F. Kaashoek, A. Rowstron (Eds.), International workshop on peer-to-peer systems (pp. 251–260). Springer.
Joshi, N., & Challa, M (2014). Secure authentication protocol to detect Sybil attacks in MANETs. International Journal of Computer Science & Engineering Technology (IJCSET), 5, 2229–3345.
Vasudeva, A., & Sood, M. (2012). Sybil attack on lowest Id clustering algorithm in the mobile ad hoc network. International Journal of Network Security & Its Applications (IJNSA),4(5), 135.
Abbas, S., Merabti, M., Llewellyn-Jones, D., & Kifayat, K. (2013). Lightweight Sybil attack detection in MANETs. IEEE Systems Journal,7(2), 236–248.
Garg, R., & Sharma, H. (2014). Proposed lightweight Sybil attack detection technique in MANET. International Journal of Advanced Research in Electrical, Electronics and Instrumentation Engineering,3(5), 7142–7147.
Paul, A., Sinha, S., & Pal, S. (2013). An efficient method to detect Sybil attack using trust based model. In Proceedings of the international conference on advances in computer science, AETACS. Amsterdam: Elsevier.
Shehzad, D., Umar, A. I., Ul Amin, N., & WaqarIshaq. (2014). A novel mechanism for detection of Sybil attack in MANETs. In International conference on computer science and information systems (ICSIS).
Zhou, T., Choudhury, R. R., Ning, P., & Chakrabarty, K. (2011). P2DAP—Sybil attacks detection in vehicular ad hoc networks. IEEE Journal on Selected Areas in Communications,29(3), 582–594.
El Zoghby, N., Cherfaoui, V., Ducourthial, B., & Denoeux, T. (2012). Distributed data fusion for detecting Sybil attacks in VANETs. In Belief functions: Theory and applications (pp. 351–358). Berlin: Springer.
Grover, J., Gaur, M. S., & Laxmi, V. (2015). Multivariate verification for Sybil attack detection in VANET. Open Computer Science,5, 60–78.
Conti, M., Di Pietro, R., Mancini, L. V., & Mei, A. (2009). Mobility and cooperation to thwart node capture attacks in MANETs. EURASIP Journal on Wireless Communications and Networking,2009(1), 945943.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Rajadurai, H., Gandhi, U.D. Fuzzy Based Collaborative Verification System for Sybil Attack Detection in MANET. Wireless Pers Commun 110, 2179–2193 (2020). https://doi.org/10.1007/s11277-019-06836-7
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-019-06836-7