Abstract
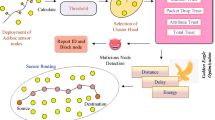
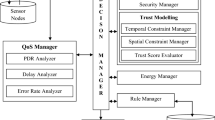
Wireless Sensor Network (WSN) and its security concern play a vital part in its effecting functioning. WSN routing layer attacks pose a great threat to its functionality, whereas if a situation arises in which multiple attacks co-exist, then the scenario will become worse. In such cases the reliability of the network deployed is greatly questionable. Thus an Intrusion detection cum Trust based framework is mandatory to detect such co existing malicious activities in order to maintain the network reliability. Energy packed Cluster heads and sink nodes are utilized for this kind of trust computation process. To achieve this, an energy based abnormality detection of malicious nodes is proposed, upon which based on the packet rate and the lifetime of sensor nodes a trust value is computed. The trust framework involves two phases namely Threat Detection phase which performs attack categorization based on Energy, Packet Count and Z scores followed by the second phase which computes the trust values for each node. Trust scores are computed based on the intensity of the attack in terms of their network performance degradation. Attacks such as Gray hole, Black hole, Wormhole, Flooding and Data Modification attacks are addressed. Data Modification attacks are detected uniquely based on the Z scores values of the sensed data set and upon the location of the nodes. If any node is found to consume abnormal energy either below or above certain threshold, identified nodes are categorized into two groups based on their threshold. Hierarchical decision making is introduced, which implies only the abnormal energy consuming nodes (among the total sensor nodes deployed in the network) are considered for further packet count based attack categorization. This way we can reduce the computational overhead of traditional trust models in which each node is checked for its reliability against multiple trust factors. Upon detecting the attacks and computing the trust values of nodes, only the nodes which have a nominal trust value are included in the routing process. Simulations were carried out in NS2 Mannasim Framework with static and mobile sensor nodes. Proposed Energy-Lifetime-Packet Count (ELPC)-Trust framework was tested under five different types of attack scenarios in a co-existing manner. Performance of the network by including the proposed ELPC trust and by ignoring the detected malicious nodes increases the throughput by 500 and PDR by 40% when compared with the attack scenario. But on the other hand introduces a delay of 0.5 seconds. Network Performance is improved in case of static networks. Under mobile scenarios proposed ELPC trust incurs high amount of delay.

























Similar content being viewed by others
References
Messai, M. L. (2014). Classification of attacks in wireless sensor networks. International Congress on Telecommunication and Applications.
Farruh, I., & Yousaf, B. Z. (2017). Trust mechanisms to secure routing in wireless sensor networks: Current state of the research and open research issues. Journal of Sensors. https://doi.org/10.1155/2017/4724852.
Dharini, N., Duraipandian, N., Katiravan, J. (2018). A novel IDS to detect multiple DoS attacks with network lifetime estimation based on learning-based energy prediction algorithm for hierarchical WSN. International Conference on Intelligent Computing and Applications. Advances in Intelligent Systems and Computing. doi:10.1007/978-981-13-2182-5_1
Guangjie, H., Jinfang, J., Wen, S., Lei, S., & Joel, R. (2013). IDSEP: A novel intrusion detection scheme based on energy prediction in cluster-based wireless sensor networks. IET Information Security,7(2), 97–105.
Feng, R., Xu, X., Zhou, X., & Wan, J. (2011). A trust evaluation algorithm for wireless sensor networks based on node behaviours and D-S evidence theory. Sensors,11(2), 1345–1360.
Wu, R., Deng, X., Lu, R., Shen, X. (2012). Trust-based anomaly detection in wireless sensor networks. In Proceedings 1st IEEE International Conference on Communications in China, pp. 203–207.
Li, X., Zhou, F., & Du, J. (2013). LDTS: A lightweight and dependable trust system for clustered wireless sensor networks. IEEE Transactions on Information Forensics and Security,8(6), 924–935.
Atakli, I, M., Hu, H., Chen, Y., Ku, W.S., Zhou, S. (2008). Malicious node detection in wireless sensor networks using weighted trust evaluation. In Proceedings of the 2008 Spring Simulation Multiconference, pp. 836–843.
Jiang, J., Han, G., Wang, F., Shu, L., & Guizani, M. (2015). An efficient distributed trust model for wireless sensor networks. IEEE Transactions on Parallel and Distributed Systems,26(5), 1228–1237.
Shaikh, R. A., Jameel, H., D’Auriol, B. J., Heejo Lee, H., Sungyoung Lee, S., & Song, Y. J. (2009). Group-based trust management scheme for clustered wireless sensor networks. IEEE Transactions on Parallel and Distributed Systems,20(11), 1698–1712.
Yao, Z., Kim, D., & Doh, Y. (2006) Plus: parameterized and localized trust management scheme for sensor networks security. In Proceedings of 2006 IEEE International Conference on Mobile Ad hoc and Sensor Systems (MASS), pp. 437–446.
Weizhi, M., Wenjuan, L., Chunhua, S., Jianying, Z., & Rongxing, L. (2017). Enhancing trust management for wireless intrusion detection via traffic sampling in the era of big data. IEEE Access,6, 7234–7243.
Boyuan, S., & Donghui, L. (2018). A comprehensive trust aware routing with multi attributes for WSNs. IEEE Access,6, 4725–4821.
Miglani, A., Bhatia, T., Sharma, G., Shrivastava, G. (2017). An energy efficient and trust aware framework for secure routing in LEACH for WSN: Scalable Computing. Practice and Experience: Special Issue on Secure Solutions for Networks in Mobile Scenarios. Scalable Computing, 13(3), 207–218
Zhenguo, C., Liqin, T., & Chuang, L. (2017). Trust model of wireless sensor networks and its application in data fusion. Sensors,17(4), 1–16.
Amjad, M., Akbar, K., Muhammad, M. U., Salwani, A., & Khairul, A. Z. A. (2017). Secure knowledge and cluster based intrusion detection mechanism for smart wireless sensor networks. IEEE Access,6, 5688–5694.
Vishwa, T. A., & Morgera, S. D. (2018). A multi-level intrusion detection system for wireless sensor networks based on immune theory. IEEE Access,6, 47364–47373.
Katiravan, J., Duraipandian, N., & Dharini, N. (2015). A two level detection of routing layer attacks in hierarchical wireless sensor networks using learning based energy prediction. KSII Transactions on Internet and Information Systems,9(11), 4644–4661.
NS2 Resource Website. (2014) Retrieved from Dec 20, 2014 https://www.nsnam.com.
NS2 Mannasim Framework Resource Website. (2014). Retrieved from Dec 20, 2014 https://www.mannasim.dcc.ufmg.br/
Mica 2 motes Data sheet Resource Document. (2014). Retrieved from Dec 20, 2014 https://www.eol.ucar.edu/isf/facilities/isa/internal/CrossBow/DataSheets/mica2.pdf.
BonnMotion v.4 Resource Document. (2018) Retrieved from Jan 25, 2018 https://sys.cs.uos.de/bonnmotion/doc/README.pdf.
Buruhanudeen, S., Othman, M., & Ali, B. M. (2007) Mobility models, broadcasting methods on factors contributing towards the efficiency of the MANET routing protocols: overview. In Proceedings of IEEE fourteenth International Conference on Telecommunication and Eighth Malaysia International Conference on Communications, pp. 231–236.
Heinzelman, W., Chandrakasan, A., & Balakrishnan, H. (2000). Energy-efficient communication protocols for wireless microsensor networks. Proceedings of the 33rd Hawaaian International Conference on Systems Science.
Lindsey, S. & Raghavendra, C. S. (2002). PEGASIS: Power-efficient gathering in sensor information systems. IEEE Aerospace Conference Proceedings, p. 26.
AODV Ietf Resource Website. (2014). Retrieved from Dec 20, 2014 https://tools.ietf.org/html/draft-ietf-manet-aodv-13.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Dharini, N., Duraipandian, N. & Katiravan, J. ELPC-Trust Framework for Wireless Sensor Networks. Wireless Pers Commun 113, 1709–1742 (2020). https://doi.org/10.1007/s11277-020-07288-0
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-020-07288-0