Abstract
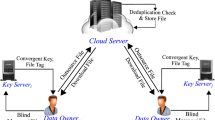
Data deduplication approach is utilized in cloud storage to decrease the bandwidth of communication and storage space by eliminating the data copies from the cloud service provider (CSP). However, one of the main problems of cloud storage is data deduplication with secure data storage. To overcome this issue, the researchers presented symmetric data storage methods based on an encryption algorithm. Nonetheless, the Enhanced Symmetric Key Encryption Algorithm (ESKEA) based on secure data storage with data deduplication is proposed in this research to further improve data confidentiality. In this approach, the block-level deduplication of data is performed using the Convergent Encryption (CE) algorithm to check the CSP duplicate copies of data. Then, ESKEA algorithm is presented for secure storage of data. In ESKEA, Spider Monkey Optimization Algorithm (SMOA) optimally selects the secret key. The results of this work showed that the execution of the proposed ESKEA is more effective than that of the SKEA in terms of upload time and download time.









Similar content being viewed by others
References
Tan, C., Hijazi, M., Lim, Y., & Gani, A. (2018). A survey on proof of retrievability for cloud data integrity and availability: Cloud storage state-of-the-art, issues, solutions and future trends. Journal of Network and Computer Applications, 110, 75–86.
Li, B., Huang, Y., Liu, Z., Li, J., Tian, Z., & Yiu, S. (2019). HybridORAM: practical oblivious cloud storage with constant bandwidth. Information Sciences, 479, 651–663.
Bedi, R., Singh, J., & Gupta, S. (2016). Analysis of multi cloud storage applications for resource constrained mobile devices. Perspectivesin Science, 8, 279–282.
Wang, R. (2017). Research on data security technology based on cloud storage. Procedia Engineering, 174, 1340–1355.
Li, H., Dong, M., Liao, X., & Jin, H. (2015). Deduplication-based energy efficient storage system in cloud environment. The Computer Journal, 58(6), 1373–1383.
Wen, Z., Luo, J., Chen, H., Meng, J., Li, X., Li, J. (2014). A verifiable data deduplication scheme in cloud computing. In: Proceedings of 6th international conference on intelligent networking and collaborative systems, 2014; Salerno, Italy.
Li, J., & Hou, M. (2018). Improving data availability for deduplication in cloud storage. International Journal of Grid and High Performance Computing, 10(2), 70–89.
Agarwala, A., Singh, P., Atrey, P. (2017). DICE: A dual integrity convergent encryption protocol for client side secure data deduplication. In: Proceddings of IEEE international conference on systems, man, and cybernetics (SMC); 2017; Banff, AB, Canada.
Li, J., Chen, X., Li, M., Li, J., Lee, P., & Lou, W. (2014). Secure deduplication with efficient and reliable convergent key management. IEEE Transactions on Parallel and Distributed Systems, 25(6), 1615–1625.
Daniel, E., & Vasanthi, N. (2017). LDAP: A lightweight deduplication and auditing protocol for secure data storage in cloud environment. Cluster Computing, 22, 1247–1258.
Yuan, H., Chen, X., Jiang, T., Zhang, X., Yan, Z., & Xiang, Y. (2018). DedupDUM: Secure and scalable data deduplication with dynamic user management. Information Sciences, 456, 159–173.
Jiang, S., Jiang, T., Wang, L. (2017). Secure and efficient cloud data deduplication with ownership management. IEEE Transactions on Services Computing. 1–1.
Malar, E., & Gauthaam, M. (2020). Wavelet analysis of EEG for the identification of alcoholics using probabilistic classifiers and neural networks. International Journal of Intelligence and Sustainable Computing, 1(1), 3.
Yang, C., Zhang, M., Jiang, Q., Zhang, J., Li, D., Ma, J., & Ren, J. (2017). Zero knowledge based client side deduplication for encrypted files of secure cloud storage in smart cities. Pervasive and Mobile Computing, 41, 243–258.
Li, X., Li, J., & Huang, F. (2015). A secure cloud storage system supporting privacy-preserving fuzzy deduplication. Soft Computing, 20(4), 1437–1448.
Shin, Y., Koo, D., Hur, J., & Yun, J. (2015). Secure proof of storage with deduplication for cloud storage systems. Multimedia Tools and Applications, 76(19), 19363–19378.
Kasiselvanathan, M., Sangeetha, V., & Kalaiselvi, A. (2020). Palm pattern recognition using scale invariant feature transform. International Journal of Intelligence and Sustainable Computing, 1(1), 44.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Elkana Ebinazer, S., Savarimuthu, N. & Mary Saira Bhanu, S. ESKEA: Enhanced Symmetric Key Encryption Algorithm Based Secure Data Storage in Cloud Networks with Data Deduplication. Wireless Pers Commun 117, 3309–3325 (2021). https://doi.org/10.1007/s11277-020-07989-6
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-020-07989-6