Abstract
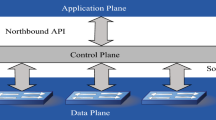
Software-defined networking (SDN) is an advanced networking technology that yields flexibility with cost-efficiency as per the business requirements. SDN breaks the vertical integration of control and data plane and promotes centralized network management. SDN allows data intensive applications to work more efficiently by making the network dynamically configurable. With the growing development of SDN technology, the issue of security becomes critical because of its architectural characteristics. Currently, Distributed denial of service (DDoS) is one of the most powerful attacks that cause the services to be unavailable for normal users. DDoS seeks to consume the resources of the SDN controller with the intention to slow down working of the network. In this paper, a detailed analysis of the effect of spoofed and non-spoofed TCP-SYN flooding attacks on the controller resources in SDN is presented. We also suggest a machine learning based intrusion detection system. Five different classification models belong to a variety of families are used to classify the traffic, and evaluated using different performance indicators. Cross-validation technique is used to validate the classification models. This work enables better features to be extracted and classify the traffic efficiently. The experimental results reveal significantly good performance with all the considered classification models.










Similar content being viewed by others
References
Singh, J., & Behal, S. (2020). Detection and mitigation of ddos attacks in sdn: A comprehensive review, research challenges and future directions. Computer Science Review, 37(100), 279.
Hakiri, A., Gokhale, A., Berthou, P., Schmidt, D. C., & Gayraud, T. (2014). Software-defined networking: Challenges and research opportunities for future internet. Computer Networks, 75, 453–471.
Kirkpatrick, K. (2013). Software-defined networking. Communication ACM, 56, 16–19.
Kreutz, D., Ramos, F. M. V., Veríssimo, P. E., Rothenberg, C. E., Azodolmolky, S., & Uhlig, S. (2015b). Software-defined networking: A comprehensive survey. Proceedings of the IEEE, 103(1), 14–76. https://doi.org/10.1109/JPROC.2014.2371999.
McKeown, N., Anderson, T., Balakrishnan, H., Parulkar, G., Peterson, L., Rexford, J., et al. (2008). Openflow: enabling innovation in campus networks. ACM SIGCOMM Computer Communication Review, 38(2), 69–74.
Tourrilhes, J., Sharma, P., Banerjee, S., & Pettit, J. (2014). SDN and openflow evolution: A standards perspective. Computer, 47(11), 22–29. https://doi.org/10.1109/MC.2014.326.
Goransson, P., Black, C., & Culver, T. (2016). Software defined networks: A comprehensive approach. Morgan Kaufmann.
Kreutz, D., Ramos, F. M., Verissimo, P., Rothenberg, C. E., Azodolmolky, S., & Uhlig, S. (2015a). Software-defined networking: A comprehensive survey. Proceedings of the IEEE, 103, 14–76.
Kim, H., & Feamster, N. (2013). Improving network management with software defined networking. IEEE Communications Magazine, 51(2), 114–119.
Swami, R., Dave, M., & Ranga, V. (2019). Software-defined Networking-based DDoS Defense Mechanisms. ACM Computing Surveys (CSUR), 52(2), 28.
Douligeris, C., & Mitrokotsa, A. (2004). DDoS attacks and defense mechanisms: Classification and state-of-the-art. Computer Networks, 44, 643–666.
Specht, S. M., & Lee, R. B. (2003). Distributed Denial of Service: Taxonomies of Attacks. Tools and Countermeasures, Princeton architecture laboratory for multimedia and security: Tech. rep., technical report.
Ramachandran, S., & Shanmugam, V. (2017). Impact of dos attack in software defined network for virtual network. Wireless Personal Communications, 94(4), 2189–2202.
Dayal, N., Maity, P., Srivastava, S., & Khondoker, R. (2016). Research trends in security and DDoS in SDN. Security and Communication Networks, 9(18), 6386–6411.
Yan, Q., Yu, F. R., Gong, Q., & Li, J. (2015). Software-defined networking (SDN) and distributed denial of service (DDoS) attacks in cloud computing environments: A survey, some research issues, and challenges. IEEE Communications Surveys & Tutorials, 18(1), 602–622.
(2018) Arbor Networks.
(2018) Biggest DDoS Attacks Today And What You Can Learn From Them. Retrieved from 1, November, 2018 https://www.crn.com/slide-shows/security/8-biggest-ddos-attacks-today-and-what-you-can-learn-from-them.
Shieber, J. (2019). Telegram faces DDoS attack in China...again. https://techcrunch.com/2019/06/12/telegram-faces-ddos-attack-in-china-again/
Kottler, S. (2018). February 28th DDoS Incident Report. https://github.blog/2018-03-01-ddos-incident-report/
(2016) 2016 Dyn cyberattack. Retrieved from 10, September, 2018 https://en.wikipedia.org/wiki/2016_Dyn_cyberattack.
Swami, R., Dave, M., & Ranga, V. (2020a). DDoS Attacks and Defense Mechanisms Using Machine Learning Techniques for SDN. In Security and Privacy Issues in Sensor Networks and IoT, IGI Global (pp. 193–214).
Kolias, C., Kambourakis, G., Stavrou, A., & Voas, J. (2017). DDoS in the IoT: Mirai and other botnets. Computer, 50(7), 80–84.
Kambourakis, G., Kolias, C., & Stavrou, A. (2017). The mirai botnet and the iot zombie armies. In MILCOM 2017-2017 IEEE Military Communications Conference (MILCOM) (pp. 267–272). IEEE.
Michie, D., Spiegelhalter, D. J., Taylor, C., et al. (1994). Machine learning. Neural and Statistical Classification 13.
Moustafa, N., Hu, J., & Slay, J. (2019). A holistic review of network anomaly detection systems: A comprehensive survey. Journal of Network and Computer Applications, 128, 33–55.
(2017) NSL-KDD dataset. Retrieved from 10, September, 2018 https://www.unb.ca/cic/datasets/nsl.html/.
(2017) UNSW-NB15 dataset. Retrieved from 19, October, 2018 https://www.unsw.adfa.edu.au/unsw-canberra-cyber/cybersecurity/ADFA-NB15-Datasets/.
(2018) CICIDS2017 dataset. Retrieved from 2, January, 2019 https://www.unb.ca/cic/datasets/ids-2017.html.
Swami, R., Dave, M., & Ranga, V. (2020b). Voting-based intrusion detection framework for securing software-defined networks. Concurrency and Computation: Practice and Experience p e5927.
Mirkovic, J., & Reiher, P. (2004). A taxonomy of DDoS attack and DDoS defense mechanisms. ACM SIGCOMM Computer Communication Review, 34(2), 39–53.
Niyaz, Q., Sun, W., & Javaid, A. Y. (2016). A deep learning based DDoS detection system in software-defined networking (SDN). CoRR. http://arxiv.org/abs/1611.07400arXiv:1611.07400).
Liu, J., Lai, Y., & Zhang, S. (2017). FL-GUARD: A Detection and Defense System for DDoS Attack in SDN. In Proceedings of the 2017 International Conference on Cryptography, Security and Privacy, ACM, New York, NY, USA, ICCSP ’17 (pp. 107–111). https://doi.org/10.1145/3058060.3058074, http://doi.acm.org/10.1145/3058060.3058074.
Yu, Y., Guo, L., Liu, Y., Zheng, J., & Zong, Y. (2018). An efficient SDN-based DDoS attack detection and rapid response platform in vehicular networks. IEEE Access, 6, 44570–44579.
Chen, Z., Jiang, F., Cheng, Y., Gu, X., Liu, W., & Peng, J. (2018). XGBoost Classifier for DDoS Attack Detection and Analysis in SDN-Based Cloud. In IEEE, 2018 IEEE International Conference on Big Data and Smart Computing (BigComp) (pp. 251–256).
Ye, J., Cheng, X., Zhu, J., Feng, L., & Song, L. (2018). A DDoS attack detection method based on SVM in software defined network. Security and Communication Networks, 2018, 1–8.
Mohammadi, R., Javidan, R., & Conti, M. (2017). SLICOTS: An SDN-Based lightweight countermeasure for TCP SYN flooding attacks. IEEE Transactions on Network and Service Management, 14(2), 487–497. https://doi.org/10.1109/TNSM.2017.2701549.
Han, B., Yang, X., Sun, Z., Huang, J., & Su, J. (2018). OverWatch: A cross-plane DDoS attack defense framework with collaborative intelligence in SDN. Security and Communication Networks 2018.
Zhu, L., Karim, M. M., Sharif, K., Li, F., Du, X., & Guizani, M. (2019). Sdn controllers: Benchmarking & performance evaluation. arXiv preprint arXiv:190204491.
Sommer, R., & Paxson, V. (2010). Outside the closed world: On using machine learning for network intrusion detection. In 2010 IEEE symposium on security and privacy (pp. 305–316). IEEE.
Sultana, N., Chilamkurti, N., Peng, W., & Alhadad, R. (2019). Survey on SDN based network intrusion detection system using machine learning approaches. Peer-to-Peer Networking and Applications, 12(2), 493–501.
(1988). Tcpdump. https://www.tcpdump.org/.
Breiman, L. (2001). Random forests. Machine learning, 45, 5–32.
Safavian, S. R., & Landgrebe, D. (1991). A survey of decision tree classifier methodology. IEEE Transactions on Systems, Man, and Cybernetics, 21(3), 660–674.
Ying, C., Qi-Guang, M., Jia-Chen, L., & Lin, G. (2013). Advance and prospects of AdaBoost algorithm. Acta Automatica Sinica, 39(6), 745–758.
Kleinbaum, D. G., Dietz, K., Gail, M., Klein, M., & Klein, M. (2002). Logistic regression. Berlin: Springer.
Kubat, M. (1999). Neural networks: A comprehensive foundation by Simon Haykin, Macmillan. The Knowledge Engineering Review, 13, 409–412.
(2008). Scapy. https://scapy.readthedocs.io/en/latest/.
(2006). Wireshark. https://www.wireshark.org/.
(2019) Mininet. http://mininet.org/.
Kalkan, K., Altay, L., Gür, G., & Alagöz, F. (2018). JESS: Joint Entropy-Based DDoS Defense Scheme in SDN. IEEE Journal on Selected Areas in Communications, 36(10), 2358–2372. https://doi.org/10.1109/JSAC.2018.2869997.
(2016) Open vSwitch. Retrieved from December 2018 https://www.openvswitch.org//.
Shalimov, A., Zuikov, D., Zimarina, D., Pashkov, V., & Smeliansky, R. (2013). Advanced study of SDN/OpenFlow controllers. In Proceedings of the 9th central & eastern european software engineering conference (p. 1). ACM.
(2017) Ryu. https://www.osrg.github.io/ryu/.
Kohavi, R., et al. (1995). A study of cross-validation and bootstrap for accuracy estimation and model selection. Ijcai, 14, 1137–1145.
Panda, M., Abraham, A., & Patra, M. R. (2012). A hybrid intelligent approach for network intrusion detection. Procedia Engineering, 30, 1–9.
Shenfield, A., Day, D., & Ayesh, A. (2018). Intelligent intrusion detection systems using artificial neural networks. ICT Express, 4(2), 95–99.
Bhavsar, Y. B., & Waghmare, K. C. (2013). Intrusion detection system using data mining technique: Support vector machine. International Journal of Emerging Technology and Advanced Engineering, 3(3), 581–586.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Swami, R., Dave, M. & Ranga, V. Detection and Analysis of TCP-SYN DDoS Attack in Software-Defined Networking. Wireless Pers Commun 118, 2295–2317 (2021). https://doi.org/10.1007/s11277-021-08127-6
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-021-08127-6