Abstract
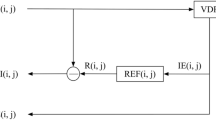
Usage of Internet has increased enormously in this decade due to the pandemic began due to COVID19. Data in the form of Text, Image and Video are communicated across the world through mails, chat applications and meeting applications etc. Such third-party applications are vulnerable while sensitive information such as personal, financial, medical and military communications occurs. Visual Cryptography (VC) is an encryption scheme that protects data in the form of image. In source, VC encrypts the image by dividing into shares and distributes to the receiver side. At the destination, the shares are stacked together physically or digitally to reveal the original data. VC also uses cover images to enhance security. VC supports secret sharing of multiple images. In this research paper, a new Multiple grayscale Secret Image Sharing (MSIS) strategy is proposed for secure transmission of more than one grayscale secret image data to the destination. MSIS uses color cover images to enhance the security. It also minimizes the number of shares and cover images to reduce the complexity.






Similar content being viewed by others

References
Naor, M., Shamir, A. (1994). Visual cryptography. In Proceedings of the EUROCRYPT, pp 1–12.
Shyu, S. J., Huang, S. Y., Lee, Y. K., Wang, R. K., & Chen, K. (2012). Sharing multiple secrets in visual cryptography. Pattern Recognition, 40(12), 3633–3651.
Verheul, E. R., & Tilborg, H. C. A. (1997). Constructions and properties of k out of n visual secret sharing schemes. Designs, Codes and Cryptography, 11, 179–196.
Yan, X., Wang, S., El-Latif, A., & Niu, X. (2015). Random grids-based visual secret sharing with improved visual quality via error diffusion. Multimedia Tools and Applications, 74, 9279–9296.
Sridhar, S., Sathishkumar, R., & Sudha, G. (2017). Adaptive halftoned visual cryptography with improved quality and security. Multimedia Tools Application, 76, 815–834.
Ateniese, G., Blundo, C., Santis, A. D., & Stinson, D. R. (2001). Extended capabilities for visual cryptography. Theoretical Computer Science, 250, 143–161.
Blundo, C., Santis, A. D., & Naor, M. (2000). Visual cryptography for grey level images. Information Process Letter, 6, 255–259.
Wu, X., & Sun, W. (2013). Random grid-based visual secret sharing with abilities of OR and XOR decryptions. Journal of Visual Communication and Image Representation, 24, 48–62.
Wu, X., Liu, T., & Sun, W. (2013). Improving the visual quality of random grid-based visual secret sharing via error diffusion. Journal of Visual Communication Image Representation, 24, 552–566.
Ren, Y., Liu, F., Guo, T., Feng, R., & Lin, D. (2016). Cheating prevention visual cryptography scheme using Latin square. IET Information Security, 11(4), 211–219.
Lin, C. C., & Tsai, W. H. (2003). Visual cryptography for gray- level images by dithering techniques. Pattern Recognition Letters, 24, 349–358.
Zhou, Z., Arce, G. R., & Di Crescenzo, G. (2006). Halftone visual cryptography. IEEE Transactions on Image Processing, 15, 2441–2453.
Wang, Z., & Arce, G. R. (2009). Halftone visual cryptography via error diffusion. IEEE Transactions on Information Forensics and Security, 4, 383–396.
Yan, B., Xiang, Y., & Hua, G. (2019). Improving the visual quality of size-invariant visual cryptography for grayscale images: An analysis-by-synthesis approach. IEEE Transactions on Image Processing, 28(2), 896–911.
Wang, R. Z., & Shyu, S. J. (2017). Scalable secret image sharing. Signal Processing Image Communication, 22, 363–373.
Mhala, N. C., Jamal, R., & Pais, A. R. (2018). Randomised visual secret sharing scheme for grey-scale and colour images. IET Image Processing, 12(3), 422–431.
Deshmukh, M., Nain, N., & Ahmed, M. (2018). Efficient and secure multi secret sharing schemes based on boolean XOR and arithmetic modulo. Multimedia Tools Application, 77, 89–107.
John Blesswin, A., Christhuraj, M. R., Sukumaran, R., & Selva Mary, G. (2020). Enhanced semantic visual secret sharing scheme for the secure image communication. Multimedia Tools and Applications, 79, 17057–17079.
Selva Mary, G., & Manoj Kumar, S. (2020). Secure grayscale image communication using significant visual cryptography scheme in real time applications. Multimedia Tools and Applications, 79, 10363–10382.
Jia, X., Wang, D., Nie, D., & Zhang, C. (2018). Collaborative visual cryptography schemes. IEEE Transactions on Circuits and Systems for Video Technology, 28(5), 1056–1070.
Mudia, H. M., & Chavan, P. V. (2016). Fuzzy logic based image encryption for confidential data transfer using (2, 2) secret sharing scheme. Procedia Computer Science, 78, 632–639.
Wang, D. S., Song, T., Dong, L., & Yang, C. N. (2013). Optimal contrast grayscale visual cryptography schemes with reversing. IEEE Transactions, 8(12), 2059–2072.
Selva Mary, G., & Manoj Kumar, S. (2019). A self-verifiable computational visual cryptographic protocol for secure two-dimensional image communication. Measurement Science and Technology, 30(12), 125404.
Fu, Z., Cheng, Y., & Yu, B. (2018). Visual cryptography scheme with meaningful shares based on QR codes. IEEE Access, 6, 59567–59574.
Lin, C. H., Chen, T. H., Wu, Y. T., Tsao, K. H., & Lin, K. S. (2013). Multi-factor cheating prevention in visual secret sharing by hybrid codebooks. Journal of Visual Communication and Image Representation, 25, 1543–2155.
Funding
Not Applicable.
Author information
Authors and Affiliations
Contributions
All authors contributed to the study conception, design and implementation. Material preparation, data collection and analysis were performed by Dr. AJB, SMG, Dr. MKS. The first draft of the manuscript was written by Dr. AJB, and all authors commented on previous versions of the manuscript. All authors read and approved the final manuscript. SMG acts on behalf of all co-authors and ensures that questions related to the accuracy or integrity of any part of the work.
Corresponding author
Ethics declarations
Conflict of interest
The authors declared that they have no conflict of interest.
Consent to Participate
All authors provided their concern to participate in this journal.
Consent for Publication
All authors provided their concern to publish the paper in this journal.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
John Blesswin, A., Selva Mary, G. & Manoj Kumar, S. Multiple Secret Image Communication Using Visual Cryptography. Wireless Pers Commun 122, 3085–3103 (2022). https://doi.org/10.1007/s11277-021-09041-7
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-021-09041-7