Abstract
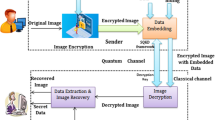
Protecting the data from malicious activities in wireless standards is one of the challenging key tasks. Moreover, cryptography plays a vital role in protecting the data in wireless channels. But some of the harmful attacks easily break the crypto algorithm, so quantum cryptography is introduced; it is the transmission of photon also proved better security for the quantum channel than the classical cryptography. So the attack in the quantum channel is difficult, but once if the quantum channel gets attacked by harmful attacks, then preventing them is too difficult. So, to enhance the security of the quantum channel, the current research proposed a novel Binary Salt Blowfish (BSB) for the encryption and decryption process. The aim of this proposed model is to enhance the security in the quantum channel against harmful activities. The proposed model is applied in the BB84 dataset; also, to check the efficiency of the proposed model, the attack like Man In The Middle (MITM) attack and Ciphertext Only Attack (COA) is launched in the quantum channel. But the quantum channel remains secure while in the presence of the attack by an efficient proposed algorithm. Finally, the efficiency of the proposed approach is compared with recent existing works and achieved better results by attaining better confidential as 99% and less error rate as 0.1. Also, it has improved the confidential rate up to 9% than the existing approaches.










Similar content being viewed by others
Explore related subjects
Discover the latest articles and news from researchers in related subjects, suggested using machine learning.References
Ma, H., Zhang, X., Xu, P., & Liu, F. (2020). Quantum secure primary communication based on quantum information compression. Wireless Personal Communications, 113, 2203–2214. https://doi.org/10.1007/s11277-020-07319-w
Miri, J., Nsiri, B., & Bouallegue, R. (2020). Certificateless based quantum cryptosystem for Ad-Hoc UWB-IR. Wireless Personal Communications, 114, 1805–1823. https://doi.org/10.1007/s11277-020-07449-1
Lai, H., Luo, M., Qu, Z., Xiao, F., & Orgun, M. A. (2018). A hybrid quantum key distribution protocol for tele-care medicine information systems. Wireless Personal Communications, 98(1), 929–943. https://doi.org/10.1007/s11277-017-4902-z
Ghilen, A., Azizi, M., & Bouallegue, R. (2017). Enhancing the security of IEEE 802.11i standard by integrating a quantum scheme for authentication and encryption key distribution. Wireless Personal Communications, 95(2), 1655–1675. https://doi.org/10.1007/s11277-016-3873-9
Zhou, N., Yan, X., Liang, H., Tao, X., & Li, G. (2018). Multi-image encryption scheme based on quantum 3D Arnold transform and scaled Zhongtang chaotic system. Quantum Information Processing, 17(12), 338. https://doi.org/10.1007/s11128-018-2104-6
Ottaviani, C., & Woolley, M. J. (2020). Terahertz quantum cryptography. IEEE Journal on Selected Areas in Communications. https://doi.org/10.1109/JSAC.2020.2968973
Krawczyk, H., Bellare, M., & Canetti, R. (1997). HMAC: Keyed-hashing for message authentication. No. RFC 2104.
Iqbal, H., & Krawec, W. O. (2020). Semi-quantum cryptography. Quantum Information Processing, 19(3), 97. https://doi.org/10.1007/s11128-020-2595-9
Aguado, A., López, D. R., Pastor, A., & López, V. (2020). Quantum cryptography networks in support of path verification in service function chains. IEEE/OSA Journal of Optical Communications and Networking, 12(4), B9–B19. https://doi.org/10.1364/JOCN.379799
Scarani, V., & Kurtsiefer, C. (2014). The black paper of quantum cryptography: Real implementation problems. Theoretical Computer Science, 560, 27–32. https://doi.org/10.1016/j.tcs.2014.09.015
Shor, P. W. (1999). Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer. SIAM Review, 41(2), 303–332. https://doi.org/10.1137/S0036144598347011
Ji, Z. X., Zhang, H. G., Wang, H. Z., Wu, F. S., Jia, J. W., & Wu, W. Q. (2019). Quantum protocols for secure multi-party summation. Quantum Information Processing, 18(6), 168. https://doi.org/10.1007/s11128-018-2141-1
Cozzolino, D., Da Lio, B., Bacco, D., & Oxenløwe, L. K. (2019). High-dimensional quantum communication: Benefits, progress, and future challenges. Advanced Quantum Technologies, 2(12), 1900038. https://doi.org/10.1002/qute.201900038
Kumar, A., Dadheech, P., Singh, V., Raja, L., & Poonia, R. C. (2019). An enhanced quantum key distribution protocol for security authentication. Journal of Discrete Mathematical Sciences and Cryptography, 22(4), 499–507. https://doi.org/10.1080/09720529.2019.1637154
Li, L., & Li, Z. (2020). A verifiable multiparty quantum key agreement based on bivariate polynomial. Information Sciences, 521, 343–349. https://doi.org/10.1016/j.ins.2020.02.057
Boyer, M., Liss, R., & Mor, T. (2020). Composable security against collective attacks of a modified BB84 QKD protocol with information only in one basis. Theoretical Computer Science, 801, 96–109. https://doi.org/10.1016/j.tcs.2019.08.014
Li, L., Li, J., Li, C., Li, H., Yang, Y., & Chen, X. (2019). The security analysis of quantum B92 protocol in collective-rotation noise channel. International Journal of Theoretical Physics, 58(4), 1326–1336. https://doi.org/10.1007/s10773-019-04025-7
Liu, B., Gao, Z., Xiao, D., Huang, W., Liu, X., & Xu, B. (2019). Quantum identity authentication in the orthogonal-state-encoding QKD system. Quantum Information Processing, 18(5), 137. https://doi.org/10.1007/s11128-019-2255-0
Niemiec, M. (2018). Error correction in quantum cryptography based on artificial neural networks. arXiv preprint
Renuka, D., & Reddy, P. C. (2018). Integrated classical and quantum cryptography scheme using three party authenticated key distribution protocols. Materials Today: Proceedings, 5(1), 1017–1023. https://doi.org/10.1016/j.matpr.2017.11.178
Kang, M. S., Choi, H. W., Pramanik, T., & Han, S. W. (2018). Universal quantum encryption for quantum signature using the swap test. Quantum Information Processing, 17(10), 254. https://doi.org/10.1007/s11128-018-2029-0
Yang, L., Wu, C., & Xie, H. (2018). Mutual authenticated quantum no-key encryption scheme over private quantum channel. Science China Information Sciences, 61(2), 022502. https://doi.org/10.1007/s11432-017-9180-2
Chaturvedi, A., Ray, M., & Veynar, R. (2018). On the security of semi-device-independent QKD protocols. Quantum Information Processing, 17(6), 131. https://doi.org/10.1007/s11128-018-1892-z
Li, Z., Li, Q., Liu, C., Peng, Y., Chan, W. H., & Li, L. (2018). Limited resource semiquantum secret sharing. Quantum Information Processing, 17(10), 285. https://doi.org/10.1007/s11128-018-2058-8
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no potential conflict of interest.
Ethical Approval
All applicable institutional and/or national guidelines for the care and use of animals were followed.
Informed Consent
For this type of study formal consent is not required.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Kumari, S. Enhancing the Quantum Communication Channel Using a Novel Quantum Binary Salt Blowfish Strategy. Wireless Pers Commun 123, 1085–1102 (2022). https://doi.org/10.1007/s11277-021-09171-y
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-021-09171-y