Abstract
Bus topology performs a significant part for describing the data transfer from one end to another in a single direction, where one node performs as a source and another end performs as the destination. The complexity of utilizing the bus topology is if the cable in the network has an issue then the entire network will be shut down. Moreover, high network traffic will arise which decreases the network performance because all the information is transferred in a single cable. The bus topology issue is complex to enhance the normal process but mathematically it is simple to reconstruct the function. Therefore, in this research data transmission of the bus topology can be designed by a novel linear algebraic theory. Besides, the linear algebraic theory for bus topology is validated by the specific theorems and the rank of the matrix is estimated by the proper calculations. The proposed design of bus topology is created by the MATLAB platform. Moreover, the created bus topology is validated in the Local Area Network (LAN) application for data transmission. Consequently, the proposed theory is compared with the other conventional techniques and proven the reliability of the novel method. Besides, the proposed bus topology design in LAN is compared with other existing methods in terms of throughput, delay, and packet delivery ratio. Therefore the results proved that the proposed scheme can attain better performance than the other conventional techniques.





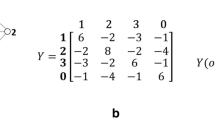
Source to Destination through the proposed bus topology



Similar content being viewed by others
Data Availability
Enquiries about data availability should be directed to the authors.
Notes
The two vector spaces have invertible linear transformation which is called an isomorphism.
Augmented matrix is the matrix which is used for performing the similar row operations on every given matrix.
This is the process of solving the linear equation that has been changed into row-echelon form.
Hermitian matrix is the complex square matrix which is equal to the conjugate transpose.
variational theorem states that the trial energy can be larger or equal to the true energy.
References
Ojha, R. P., Srivastava, P. K., Sanyal, G., & Gupta, N. (2021). Improved model for the stability analysis of wireless sensor network against malware attacks. Wireless Personal Communications, 116(3), 2525–2548. https://doi.org/10.1007/s11277-020-07809-x
Kuruba, P., & Dushyantha, N. D. (2021). Stability control in polygon based topology formation and information gathering in satellite based wireless sensor network. Wireless Personal Communications, 120(4), 2491–2518. https://doi.org/10.1007/s11277-020-07568-9
Sharma, S., & Verma, V. K. (2022). An integrated exploration on internet of things and wireless sensor networks. Wireless Personal Communications. https://doi.org/10.1007/s11277-022-09487-3
Cheney, W., & Kincaid, D. (2009). Linear algebra: Theory and applications. The Australian Mathematical Society, 110.
Ahmed, M. I., & Kannan, G. (2021). Secure end to end communications and data analytics in IoT integrated application using IBM Watson IoT platform. Wireless Personal Communications, 120(1), 153–168. https://doi.org/10.1007/s11277-021-08439-7
Sundaram, K., & Vellupillai, S. (2021). Designing a novel star topology using operad linear differential theory. Wireless Personal Communications, 120(1), 565–585. https://doi.org/10.1007/s11277-021-08478-0
Pade, J., & Tischendorf, C. (2019). Waveform relaxation: A convergence criterion for differential-algebraic equations. Numerical Algorithms, 81(4), 1327–1342. https://doi.org/10.1007/s11075-018-0645-5
Zhu, F., Zhang, C., Zheng, Z., & Farouk, A. (2021). Practical network coding technologies and softwarization in wireless networks. IEEE Internet of Things Journal, 8(7), 5211–5218. https://doi.org/10.1109/JIOT.2021.3056580
Patil, D., Tesi, P., & Trenn, S. (2019). Indiscernible topological variations in DAE networks. Automatica, 101, 280–289. https://doi.org/10.1016/j.automatica.2018.12.012
Sriyananda, M. G. S., Wang, X., & Rao, R. K. (2021). Crowdsensing-assisted path loss estimation and management of dynamic coverage in 3D wireless networks with dense small cells. IEEE Access, 9, 112670–112685. https://doi.org/10.1109/ACCESS.2021.3100085
Fang, Q., & Peng, J. (2018). Synchronization of fractional-order linear complex networks with directed coupling topology. Physica A: Statistical Mechanics and its Applications, 490, 542–553. https://doi.org/10.1016/j.physa.2017.08.050
Jogunola, O., Adebisi, B., Anoh, K., Ikpehai, A., Hammoudeh, M., Harris, G., & Gacanin, H. (2018). Distributed adaptive primal algorithm for P2P-ETS over unreliable communication links. Energies, 11(9), 2331. https://doi.org/10.3390/en11092331
Zhang, J., Raza, M., Khalid, R., Parveen, R., & Ramírez-Asís, E. H. (2021). Impact of team knowledge management, problem solving competence, interpersonal conflicts, organizational trust on project performance, a mediating role of psychological capital. Annals of Operations Research. https://doi.org/10.1007/s10479-021-04334-3
Li, H., Zheng, Y., & Alsaadi, F. E. (2019). Algebraic formulation and topological structure of Boolean networks with state-dependent delay. Journal of Computational and Applied Mathematics, 350, 87–97. https://doi.org/10.1016/j.cam.2018.10.003
Carrell, J. B. (2005). Fundamentals of linear algebra. The University of British Columbia.
Anh, L. Q., & Van Hung, N. (2018). Stability of solution mappings for parametric bilevel vector equilibrium problems. Computational and Applied Mathematics, 37(2), 1537–1549. https://doi.org/10.1007/s40314-016-0411-z
Jagadeesh, H., Joshi, R., & Rao, M. (2021). Group secret-key generation using algebraic rings in wireless networks. IEEE Transactions on Vehicular Technology, 70(2), 1538–1553. https://doi.org/10.1109/TVT.2021.3054031
Fika, P., Mitrouli, M., & Roupa, P. (2014). Estimates for the bilinear form Xt A−Y with applications to linear algebra problems. Electronic Transactions on Numerical Analysis, 43, 70–89.
Garg, A., Makam, V., Oliveira, R., & Wigderson, A. (2019). Wigderson, Search problems in algebraic complexity, GCT, and hardness of generator for invariant rings. arXiv:1910.01251.
Ibrar, M., Wang, L., Muntean, G. M., Shah, N., Akbar, A., & Ibrahim, K. (2021). SOSW: Scalable and optimal nearsighted location selection for fog node deployment and routing in SDN-based wireless networks for IoT systems. Annals of Telecommunications, 76(5), 331–341. https://doi.org/10.1007/s12243-021-00845-z
Wang, W., Li, Y., Yu, T., Huang, B, & Yang, W. Q. (2021). The optimization design of wireless network router efficiency based on multi-attribute decision-making model. In 2021 International conference on digital society and intelligent systems (DSInS). IEEE. https://doi.org/10.1109/DSInS54396.2021.9670616
Duan, G. (2021). Application of computer network multimedia technology in the teaching reform of advanced algebra. The international conference on cyber security intelligence and analytics. Springer, Cham. https://doi.org/10.1007/978-3-030-69999-4_89
Hoang, T. M. (2021). A Study on Anomaly Data Traffic Detection Method for Wireless Sensor Networks. The international conference on intelligent systems & networks. Springer, Singapore. https://doi.org/10.1007/978-981-16-2094-2_52
Swain, R. R., Khilar, P. M., & Dash, T. (2019). Neural network based automated detection of link failures in wireless sensor networks and extension to a study on the detection of disjoint nodes. Journal of Ambient Intelligence and Humanized Computing, 10(2), 593–610. https://doi.org/10.1007/s12652-018-0709-3
Megalingam, R. K., Tantravahi, S., Tammana, H. S. S. K., Puram, H. S. R., & Ganta, S. (2021). Robot operating system integrated sensing system and forward kinematics of a robot manipulator of a rescue robot. In 2021 International Conference on Intelligent Technologies (CONIT). IEEE. https://doi.org/10.1109/CONIT51480.2021.9498567
Giannini, J. A., Richard, D., Manning, M. L., & Lerner, E. (2021). Bond-space operator disentangles quasilocalized and phononic modes in structural glasses. Physical Review E, 104(4), 044905. https://doi.org/10.1103/PhysRevE.104.044905
Khalid, W., Yu, H., Do, D. T., Kaleem, Z., & Noh, S. (2021). RIS-aided physical layer security with full-duplex jamming in underlay D2D networks. IEEE Access, 9, 99667–99679. https://doi.org/10.1109/ACCESS.2021.3095852
Acknowledgements
None.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no potential conflict of interest.
Ethical Approval
All applicable institutional and/or national guidelines for the care and use of animals were followed.
Informed Consent
For this type of study formal consent is not required.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Sundaram, K., Velupillai, S. Linear Algebraic Theory for Designing the Bus Topology to Enhance the Data Transmission Process. Wireless Pers Commun 126, 401–420 (2022). https://doi.org/10.1007/s11277-022-09751-6
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-022-09751-6