Abstract
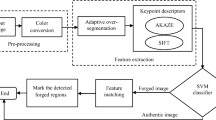
Digital images are tampered easily but detection of non-uniform texture is a challenging task. Therefore, various schemes are developed from many years by numerous researchers to overcome issues related to image forgery but still it requires reliability and validity to process in future for civilization safe and secure online/offline communication. Therefore, we worked on both categories of passive image forensics individually and then we applied the combined process-Block based and Key-Point based schemes in order to detect forgery in more efficient manner using segmentation algorithm with irregular blocks. Proposed algorithm includes cloning with different degree rotation for image forensic investigation. Proposed scheme is applied over many morphological operations, Post processing and invariant transform techniques to validate the results. This scheme gives consistent results in case of different image size, type of images, resizing, scaling, shifting, and multiple cloning with uniform and non-uniform textures. Proposed algorithm works under different test scenario and gives results in just 37 s to investigate the analysis with less computational efforts as it involves some manual calculation with large number of datasets used for experimental testing. Proposed work includes real time datasets for best result against latest State-of-art-Methodologies. Future scope can work on other type of forgeries like audio and video etc.








Similar content being viewed by others
References
Bashar, M. K., Noda, K., Ohnishi, N., & Mori, K. (2010). Exploring duplicated regions in natural images. IEEE Transactions on Information Forensics and Security. https://doi.org/10.1109/TIP.2010.2046599
Pun, C., Member, S., Yuan, X., & Bi, X. (2015). Over—Segmentation and feature point matching. IEEE Transactions on Information Forensics and Security, 6013(c), 1–12.
Christlein, V., Member, S., Riess, C., Member, A., Jordan, J., Member, S., et al. (2012). An evaluation of popular copy-move forgery detection approaches. IEEE Transactions Information Forensics and Security, 7(6), 1841–1854.
Li, J., Li, X., Yang, B., & Sun, X. (2015). Segmentation-based image copy-move forgery detection scheme. IEEE Transactions on Information Forensics and Security, 10(3), 507–518.
Pan, X., & Lyu, S. (2010). Region duplication detection using image feature matching. IEEE Transactions on Information Forensics and Security, 5(4), 857–867.
Ryu, S., Kirchner, M., Lee, M., & Lee, H. (2013). Rotation invariant localization of duplicated image regions based on Zernike moments. IEEE Transactions on Information Forensics and Security, 8(8), 1355–1370.
Zandi, M., Mahmoudi-Aznaveh, A., & Talebpour, A. (2016). Iterative copy-move forgery detection based on a new interest point detector. IEEE Transactions on Information Forensics and Security, 11(11), 2499–2512.
Amiano, L. D., Cozzolino, D., Poggi, G., & Verdoliva, L. (2018). A PatchMatch-based Dense-field algorithm for video copy-move detection and localization. IEEE Transactions on Circuits and Systems, 29, 669.
Teerakanok, S., & Uehara, T. (2019). Copy-move forgery detection: A state-of-the-art technical review and analysis. IEEE Access, 7, 40550.
Amerini, I., Ballan, L., Caldelli, R., Del Bimbo, A., & Serra, G. (2011). A SIFT-based forensic method for copy-move attack detection and transformation recovery. IEEE Transactions on Information Forensics and Security, 6, 1099.
Popescu, A. C. & Farid, H. (2004). Exposing digital forgeries by detecting duplicated image regions, Tech. Rep. TR2004–515, Dartmouth College.
Silva, E., et al. (2015). Going deeper into copy-move forgery detection: Exploring image telltales via multi-scale analysis and voting processes. Journal of Visual Communication and Image Representation, 29, 16–32.
Amerini, I., et al. (2013). Copy-move forgery detection and localization by means of robust clustering with J-Linkage. Signal Processing: Image Communication, 28, 659.
Amerini, I., et al. (2015). A feature-based forensic procedure for splicing forgeries detection. Mathematical Problems in Engineering. https://doi.org/10.1155/2015/653164
Amerini, I., Becarelli, R., Caldelli, R., & Del Mastio, A. (2014). Splicing forgeries localization through the use of first digit features. In 2014 IEEE International Workshop on Information Forensics and Security (WIFS) (pp. 143–148).
Siddeq, M. M., & Rodrigues, M. A. (2017). DCT and DST based image compression for 3D reconstruction. 3D Research. https://doi.org/10.1007/s13319-017-0116-0
Warbhe, A. D., Dharaskar, R. V., & Thakare, V. M. (2016). A survey on keypoint based copy-paste forgery detection techniques. Physics Procedia, 78(December 2015), 61–67.
Malviya, V., & Ladhake, S. A. (2016). Pixel based image forensic technique for copy-move forgery detection using auto color correlogram. Procedia Computer Science, 79, 383–390.
Tang, C., Kong, A. W. K., & Craft, N. (2011). Using a knowledge-based approach to remove blocking artifacts in skin images for forensic analysis. IEEE Transactions on Information Forensics and Security, 6(3 PART 2), 1038–1049.
Mahdian, S. (2006). Saic, S (2006) “Detection of copy-move forgery using a method based on blur moment invariants. Forensic Science International, 171, 180–189.
Bi, X., & Pun, C. (2018). PT. Pattern Recognition.
Cao, Y., et al. (2012). A robust detection algorithm for copy-move forgery in digital images. Forensic Science International, 214(1–3), 33–43.
Pandey, R. C., Singh, S. K., Shukla, K. K., & Agrawal, R. (2015). Fast and robust passive copy-move forgery detection using SURF and SIFT image features. In 9th International Conference on Industrial and Information Systems ICIIS 2014.
Prasad, S., & Ramkumar, B. (2017) Passive copy-move forgery detection using SIFT, HOG and SURF features. In 2016 IEEE International Conference on Recent Trends in Electronics, Information & Communication Technology (RTEICT) (pp. 706–710).
Fadl, S. M., Semary, N. A. (2015). A proposed accelerated image copy-move forgery detection. In 2014 IEEE Visual Communications and Image Processing Conference VCIP 2014 (pp. 253–257).
Sudhakar, K., Sandeep, V. M., & Kulkarni, S. (2014). Shape based copy move forgery detection using level set approach. In 2014 Fifth International Conference on Signal and Image Processing (pp. 213–217).
Lin, H.-J., Wang, C.-W., & Kao, Y.-T. (2009). Fast copy-move forgery detection. WSEAS Transactions on Signal Processing (WSEAS-TSP), 5, 188–197.
Karsh, R. K., Laskar, R. H., & Aditi, S. (2017). Robust image hashing through DWT-SVD and spectral residual method. EURASIP Journal on Image and Video Processing, 2017(1), 31.
De Carvalho, T. J., Member, S., Riess, C., Member, A., Angelopoulou, E., Pedrini, H., & Rocha, A. D. R. (2013). Exposing digital image forgeries by illumination color classification. IEEE Transactions on Information Forensics and Security, 8(7), 1182–1194.
Chierchia, G., Member, S., Poggi, G., Sansone, C., & Verdoliva, L. (2014). A Bayesian-MRF approach for PRNU-based image forgery detection. IEEE Transactions on Information Forensics and Security, 9(4), 554–567.
Li, H., Luo, W., Qiu, X., & Huang, J. (2017). Image Forgery Localization via Integrating. IEEE Transactions on Information Forensics and Security, 6013(c), 1–13.
Ardizzone, E., Bruno, A., & Mazzola, G. (2015). Copy-move forgery detection by matching triangles of keypoints. IEEE Transactions on Information Forensics and Security, 10, 2084.
Wattanachote, K., Shih, T. K., Member, S., & Chang, W. (2015). Tamper detection of JPEG image due to seam modifications. IEEE Transactions on Information Forensics and Security, 10, 2477.
Li, H., Luo, W., & Huang, J. (2017). Localization of diffusion-based inpainting in digital images. IEEE Transactions on Information Forensics and Security, 6013(2), 1–15.
Carvalho, T., Faria, F. A., Pedrini, H., da Torres, R., & Rocha, A. (2015). Illuminant based Transformed Spaces for Image Forensics. IEEE Transactions on Information Forensics and Security, 11, 720.
Joshi, S., Member, S., & Khanna, N. (2017). Single classifier-based passive system for source printer classification using local texture features. IEEE Transactions on Information Forensics and Security, 13, 1603.
Mayer, O., Member, S., & Stamm, M. C. (2018). Accurate and Efficient Image Forgery Detection Using Lateral Chromatic Aberration. IEEE Transactions on Information Forensics and Security, 6013(c), 1–16.
Guo, Y., Cao, X., Member, S., & Zhang, I. W. (2018). Fake colorized image detection. IEEE Transactions on Information Forensics and Security, 6013(c), 1–13.
Yan, Y., Member, S., & Ren, W. (2018). Recolored image detection via a deep discriminative model. IEEE Transactions on Information Forensics and Security, 14, 5–17.
Li, Y., Member, S., & Zhou, J. (2018). Fast and effective image copy-move forgery detection via hierarchical feature point matching. IEEE Transactions on Information Forensics and Security, 14, 1307.
Qiao, T., Shi, R., Luo, X., Xu, M., Zheng, N., & Wu, Y. (2018). Statistical model-based detector via texture weight map: Application in re-sampling authentication. IEEE Transactions on Multimedia, 21, 1077.
Su, Li, C., Lai, Y., & Yang, J. (2017). A fast forgery detection algorithm based on exponential-fourier moments for video region duplication. IEEE Trans on Multimedia, 20, 825.
Neubert, T., Makrushin, A., Hildebrandt, M., Kraetzer, C., & Dittmann, J. (2018). Extended StirTrace benchmarking of biometric and forensic qualities of morphed face images. IET Journals, 7, 325–332.
Dixit, R., Naskar, R., & Mishra, S. (2017). Blur-invariant copy-move forgery detection technique with improved detection accuracy utilising SWT-SVD. IET Image Processing, 11, 301–309.
Cristin, R., Ananth, J. P., & Raj, V. C. (2018). Illumination-based texture descriptor and fruitfly support vector neural network for image forgery detection in face images. IET Image Processing, 12, 1439–1449.
Soni, B., Das, P. K., & Thounaojam, D. M. (2018). Keypoints based enhanced multiple copy- move forgeries detection system using density-based spatial clustering of application with noise clustering algorithm. IET Image Processing., 12, 2092.
Fadl, S. M., Han, Q., & Li, Q. (2019). Inter-frame forgery detection based on differential energy of residue. IET Image Processing, 13, 522–528.
Soni, B., Das, P. K., & Thounaojam, D. M. (2017). CMFD: A detailed review of block based and key feature based techniques in image copy- move forgery detection. IET Image Processing, 12, 167.
Sheng, H., Shen, X., Lyu, Y., & Shi, Z. (2018). Image splicing detection based on Markov features in discrete octonion cosine transform domain. IET Image Processing, 12(c), 1815–1823.
Mahdian, B., Nedbal, R., & Saic, S. (2013). Blind verification of digital image originality: A statistical approach. IEEE Transactions on Information Forensics and Security, 8(9), 1531–1540.
Monika, S., & Dipali, B. (2019). Robust copy-paste detection algorithm using SIFT for digital image forensics. International Journal of Recent Technology and Engineering, 8(4), 3616–3627.
Monika, & Dipali, B. (2019). Forensic science research summary for forgery detection of Digital Images. International Journal of Engineering and Advanced Technology, 9(2).
Monika, S., & Dipali, B. (2019). Image forgery detection and localization using DCT-based forensic analysis approach. International Journal of Advanced Science and Technology, 28(18), 699–713.
Bansal, D., Khan, M., & Salhan, A. K. (2009). Real time acquisition and PC to PC wireless transmission of human carotid pulse waveform. Computers in Biology and Medicine, 39(10), 915–920.
Bansal, D., Khan, M., Salhan, A. K. (2010). Wireless transmission of EMG signal and analysis of its correlation with simultaneously acquired carotid pulse wave using dual channel system. In Second International Conference on eHealth, Telemedicine and Social Medicine (pp. 125–129).
Bansal, D. (2013). Design of 50 Hz notch filter circuits for better detection of online ECG Dipali Bansal. Computers in Biology and Medicine, 13(1), 30–48.
Bansal, D., & Singh, V. R. (2014). Algorithm for online detection of HRV from coherent ECG and carotid pulse wave. Computers in Biology and Medicine, 14(4), 333.
Bansal, D., Mahajan, R., Roy, S., Rathee, D., & Singh, S. (2015). Real-time man—Machine interface and control using deliberate eye blink. Computers in Biology and Medicine, 18(4), 370–384.
Mahajan, R., & Bansal, D. (2015). Automated cardiac state diagnosis from hybrid features of ECG using neural network classifier. International Journal of Biomedical Engineering and Technology, 17(3), 209–231.
Mahajan, R., & Bansal, D. (2015). Depression diagnosis and management using EEG- based affective brain mapping in real time. International Journal of Biomedical Engineering and Technology, 18(2), 115–138.
Mahajan, R., & Bansal, D. (2017). Real time EEG based cognitive brain computer interface for control applications via arduino interfacing. Procedia Computer Science, 115, 812–820.
Singh, S., & Bansal, D. (2014). Design and development of BCI for online acquisition, monitoring and digital processing of EEG waveforms. Computers in Biology and Medicine, 16(4), 359–373.
Al-Qershi, O. M., & Khoo, B. E. (2013). Passive detection of copy-move forgery in digital images: State-of-the-art. Forensic Science International, 231(1–3), 284–295.
Hashmi, M. F., Anand, V., & Keskar, A. G. (2014). Copy-move image forgery detection using an efficient and robust method combining un-decimated wavelet transform and scale invariant feature transform. AASRI Procedia, 9(Csp), 84–91.
Gupta, A., Saxena, N., & Vasistha, S. K. (2013). Detecting copy move forgery using DCT. International Journal of Scientific and Research Publications, 3(5), 3–6.
Boonsivanon, K., & Meesomboon, A. (2016). IKDSIFT: An improved keypoint detection algorithm based-on SIFT approach for non-uniform illumination. Procedia Computer Science, 86(March), 269–272.
Warif, N. B. A., Wahab, A. W. A., Idris, M. Y. I., Salleh, R., & Othman, F. (2017). SIFT-Symmetry: A robust detection method for copy-move forgery with reflection attack. Journal of Visual Communication and Image Representation, 46, 219–232.
Prasad, S., & Ramkumar, B. (2017). Passive copy-move forgery detection using SIFT, HOG and SURF features. In 2016 IEEE International Conference on Recent Trends in Electronics, Information and Communication Technology, RTEICT 2016—Proceedings (pp. 706–710).
Daugman, J. (1980). Two-dimensional analysis of cortical receptive field profiles. Vision Research, 20, 846–856.
Liu, G., Wang, J., Lian, S., & Wang, Z. (2011). A passive image authentication scheme for detecting region-duplication forgery with rotation. Journal of Network and Computer Applications, 34, 1557–1565.
Mahdian, B., & Saic, S. (2007). Detection of copy-move forgery using a method based on blur moment invariants. Forensic Science International, 171, 180–189.
Zhao, J., & Guo, J. (2013). Passive forensics for copy-move image forgery using a method based on DCT and SVD. Forensic Science International, 233, 158.
Chang, I., Yu, J. C., & Chang, C. (2013). A forgery detection algorithm for exemplar-based inpainting images using multi-region relation. IMAVIS, 31(1), 57–71.
Luo, W., Huang, J., Qiu, G. (2006). Robust detection of region duplication forgery in digital image. In Proceedings of the 18th International Conference on Pattern Recognition (vol. 4, pp. 746–749).
Qu, Z., Luo, W., Huang, J. (2008). A convolutive mixing model for shifted double JPEG compression with application to passive image authentication. In IEEE International Conference on Acoustics, Speech and Signal Processing (pp. 1661–1664).
Bashar, M., Noda, K., Ohnishi, N., & Mori, K. (2010). Exploring duplicated regions in natural images. IEEE Transactions on Image Processing. https://doi.org/10.1109/TIP.2010.2046599
Ustubioglu, B., et al. (2016). A new copy move forgery detection technique with automatic threshold determination. AEU International Journal of Electronics and Communications, 70(8), 1076–1087.
Li, L., Li, S., Zhu, H. (2013). An efficient scheme for detecting copy-move forged images by local binary patterns. Journal of Information Hiding and Multimedia Signal Processing, 4(1), 46–56.
Zhang, Z. et al. (2008). A survey on passive-blind image forgery by doctor method detection. In Proceedings of the 7th International Conference on Machine Learning and Cybernetics, ICMLC (vol. 6(July), pp. 3463–3467).
Lin, C.-W., Wang, Y.-T., & Kao. (2009). Fast copymove forgery detection. WSEAS Trans. Signal Process. (WSEAS-TSP) (PP.188–197).
Acknowledgements
Authors would like to thank the reviewers for their valuable comments.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Monika, Bansal, D. & Passi, A. Image Forgery Detection and Localization Using Block Based and Key-Point Based Feature Matching Forensic Investigation. Wireless Pers Commun 127, 2823–2839 (2022). https://doi.org/10.1007/s11277-022-09898-2
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-022-09898-2