Abstract
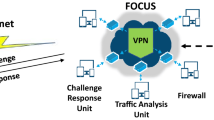
As Artificial Intelligence (AI) and the Internet of Things (IoT) applications become more eminent, business and government organizations have started thinking aggressively about processing and analyzing data. Despite efficient data processing and analyzing, business organizations are faced with several issues, because, with data becoming an organization’s most valuable, data tampering creates the threat of data breaches, and cyberattacks nullify the provisioning of a smarter and more continuous working world. Hence, protecting the advantages that AI applications and IoT devices provide must remain the primary concern for today’s organizations. In this article, Holistic Feistel Authentication and Learning-based Authorization (HFA-LA) method present this for protecting IoT applications against cyberattacks. More specifically, a lightweight authentication approach is designed by exploring the use of Feistel Block Message Authentication by the cloud service manager to identify the authenticated devices. A holistic authentication and authorization approaches is designed. In which Artificial Intelligent Feed Forward Learning and trust management via error measurement are adopted to analyze the IoT applications to access the cloud resources. This new HFA-LA method establish the connections between IoT devices and cloud services and combat against cyberattacks so that the communication latency (i.e., communication time and overhead) is improved, and security risks are well controlled for IoT applications. Simulation is performed with different metrics, such as, communication time, communication overhead, true positive rate, and false-positive rate. The observed results show that the HFA-LA method efficiently improves the true positive rate and reduces the communication time, the overhead and false positive rate more than the state-of-the-art methods.









Similar content being viewed by others
Data Availability
Data sharing not applicable to this article as no datasets were generated or analysed during the Current study.
References
Hasan, M., Islam, M. M., Zarif, M. I. I., & Hashem, M. M. A. (2019). Attack and anomaly detection in IoT sensors in IoT sites using machine learning approaches. Internet of Things, 7, 100059.
Park, J.-H., Salim, M. M., Jo, J. H., Sicato, J. C. S., Rathore, S., & Park, J. H. (2019). CIoT-Net: a scalable cognitive IoT based smart city network architecture. Human-centric Computing and Information Sciences, 9(1), 29.
Thakong, M., Phimoltares, S., Jaiyen, S., & Lursinsap, C. (2018). One-pass-throw-away learning for cybersecurity in streaming non-stationary environments by dynamic stratum network. PLoS ONE, 13(9), e0202937.
Mosenia, A., & Jha, N. K. (2016). A comprehensive study of security of internet-of-things. IEEE Transactions on Emerging Topics in Computing, 5(4), 586–602.
Radisavljevic-Gajic, V., Park, S., & Chasaki, D. (2017). Vulnerabilities of control systems in internet of things applications. IEEE Internet of Things Journal, 5(2), 1023–1032.
Liu, X., Qian, C., Hatcher, W. G., Hansong, X., Liao, W., & Wei, Y. (2019). Secure internet of things (IoT)-based smart-world critical infrastructures: Survey. IEEE Access: Case Study and Research Opportunities.
Machidon, O. M., Stanca, C., Ogrutan, P., Gerigan, C., & Aciu, L. (2018). Power-system protection device with IoT-based support for integration in smart environments. PLoS ONE, 13(12), e0208168.
Bailey, C., Chadwick, D. W., & de Lemos, R. (2014). Self-adaptive federated authorization infrastructures. Journal of Computer and System Sciences, 80(5), 935–952.
Shalan, A., & Zulkernine, M. (2014). Software control flow error detection and correlation with system performance deviation. Journal of Computer and System Sciences, 80(5), 953–972.
Xie, Y., & Wang, G. (2014). Message matching-based greedy behavior detection in delay tolerant networks. Journal of Computer and System Sciences, 80(5), 903–915.
Jang-Jaccard, J., & Nepal, S. (2014). A survey of emerging threats in cybersecurity. Journal of Computer and System Sciences, 80(5), 973–993.
Abomhara, M. (2015). Cyber security and the internet of things: Vulnerabilities, threats, intruders and attacks. Journal of Cyber Security and Mobility, 4(1), 65–88.
Maglaras, L., Ferrag, M.A., Derhab, A., Mukherjee, M., Janicke, H. & Rallis, S. (2019). Threats, protection and attribution of cyber attacks on critical infrastructures. arXiv preprint arXiv:1901.03899.
Park, M., Han, J., Oh, H., & Lee, K. (2019). Threat assessment for android environment with connectivity to IoT devices from the perspective of situational awareness. Wireless Communications and Mobile Computing, 2019, 1–12.
Hyman, B., Alisha, Z., & Gordon, S. (2019). Secure controls for smart cities; applications in intelligent transportation systems and smart buildings. International Journal of Science and Engineering Applications, 8(6), 167–71.
Spathoulas, G., & Katsikas, S. (2019). Towards a secure industrial internet of things. Security and privacy trends in the industrial internet of things (pp. 29–45). Cham: Springer.
Zubiaga, A., Procter, R., & Maple, C. (2018). A longitudinal analysis of the public perception of the opportunities and challenges of the Internet of Things. PLoS ONE, 13(12), e0209472.
Wu, Xu., & Li, F. (2017). A multi-domain trust management model for supporting RFID applications of IoT. PLoS ONE, 12(7), e0181124.
Dilek, S., Çakır, H., & Aydın, M. (2015). Applications of artificial intelligence techniques to combating cyber crimes: A review. arXiv preprint arXiv:1502.03552.
Elsaeidy, A., Elgendi, I., Munasinghe, K. S., Sharma, D., & Jamalipour, A. (2017). A smart city cyber security platform for narrowband networks. In 2017 27th International Telecommunication Networks and Applications Conference (ITNAC), pp. 1–6. IEEE.
Baker, T., Asim, M., MacDermott, Á., Iqbal, F., Kamoun, F., Shah, B., Alfandi, O., & Hammoudeh, M. (2019). A secure fog-based platform for SCADA-based IoT critical infrastructure. Software: Practice and Experience., 50(5), 503–18.
Tahir, H., Tahir, R., & McDonald-Maier, K. (2018). On the security of consumer wearable devices in the internet of things. PLoS ONE, 13(4), e0195487.
Weems, C. F., Ahmed, I., Richard III, G. G., Russell, J. D., & Neill, E. L. (2018). Susceptibility and resilience to cyber threat: Findings from a scenario decision program to measure secure and insecure computing behavior. PLoS ONE, 13(12), e0207408.
Chen, Y.-Z., Huang, Z.-G., Shouhuai, Xu., & Lai, Y.-C. (2015). Spatiotemporal patterns and predictability of cyberattacks. PLoS ONE, 10(5), e0124472.
Díaz López, D., Uribe, M. B., Cely, C. S., Torres, A. V., Guataquira, N. M., Castro, S. M., Nespoli, P. & Mármol, F. G. (2018) Shielding IoT against cyber-attacks: An event-based approach using SIEM. Wireless Communications and Mobile Computing.
Mihoub, A., Fredj, O. B., Cheikhrouhou, O., Derhab, A., & Krichen, M. (2022). Denial of service attack detection and mitigation for internet of things using looking-back-enabled machine learning techniques. Computers and Electrical Engineering, 98, 1–12.
Rana, M. M., & Bo, R. (2019). IoT-based improved human motion estimations method Under cyber attacks. IEEE Internet of Things Journal IoT, 6(6), 2327-4662(c).
Samy, A., Haining, Y., & Zhang, H. (2020). Fog-based attack detection framework for internet of things using deep learning. IEEE Access, 8, 74571–85.
Rana, M. M. (2019). IoT-based electric vehicle state estimation andcontrol algorithms under cyber attacks. IEEE Internet of Things Journal IoT, 7(2), 2327–4662.
Jahromi, A. N., Karimipour, H., Dehghantanha, A., & Choo, K. K. R. (2021). Toward detection and attribution of cyber-attacks in IoT-enabled cyber-physical systems. IEEE Internet of Things Journal, 8(17), 1–11.
Funding
No Funding.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interests
On behalf of all authors, the corresponding author states that there is no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Rahim, R., Ramachandran, M., Jayachandran, P. et al. Holistic Feistel Authenticated Learning-`Based Authorization for Protecting the Internet of Things from Cyber Attacks. Wireless Pers Commun 127, 3511–3532 (2022). https://doi.org/10.1007/s11277-022-09930-5
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-022-09930-5