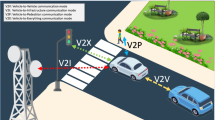
Abstract
The Vehicular Cloud Computing (VCC) provides significant benefits (e.g., higher resource availability, and low communication latency) to vehicular applications. However, still there exists latency related issues with applications that require real-time response, and it is difficult to achieve when using VCC. Therefore, the use of fog computing that provides the next level service of cloud computing from the centre to edge networks is envisioned. Apart from low latency, fog computing also supports mobility, location-awareness, and real-time data handling, which enables ubiquitous connectivity between fog nodes and smart vehicles. However, there remain several security and privacy challenges while using fog computing in VANET applications. To address these challenges, we propose the design of an authenticated message-exchange scheme for fog-assisted VCC (called AME-VCC). The proposed scheme ensures mutual authentication along with anonymity, which enables accountable privacy. The correctness of the protocol and its security is proved in the random oracle model, which indicates that it is provably secure under any probabilistic polynomial time adversary. Moreover, the comparative study of computation cost is done to prove the claim of efficiency. The analysis of security and performance indicates that AME-VCC is computationally efficient protocol, and it ensures authenticated secure message exchange with anonymity and unlinkability.






Similar content being viewed by others
References
Hou, X., Li, Y., Chen, M., Di, W., Jin, D., & Chen, S. (2016). Vehicular fog computing: A viewpoint of vehicles as the infrastructures. IEEE Transactions on Vehicular Technology, 65(6), 3860–3873.
Bonomi, F., Milito, R., Zhu, J., & Addepalli, S. (2012). Fog computing and its role in the internet of things. In: Proceedings of the first edition of the MCC workshop on Mobile cloud computing, pages, (pp. 13–16). ACM.
Khattak, H. A., Islam, S. U., Din, I. U., & Guizani, M. (2019). Integrating fog computing with vanets: A consumer perspective. IEEE Communications Standards Magazine, 3(1), 19–25.
Arul Mozhi Pradeepa, M., & Gomathi, B. (2017). Towards fog computing based cloud sensor integration for Internet of Things. International Journal of Computer Science and Engineering Communications, 5(6), 1761–1773.
Jia, X., He, D., Kumar, N., & Choo, K.-K.R. (2018). Authenticated key agreement scheme for fog-driven IoT healthcare system. Wireless Networks, 25, 4737–4750.
Basudan, S., Lin, X., & Sankaranarayanan, K. (2017). A privacy-preserving vehicular crowdsensing-based road surface condition monitoring system using fog computing. IEEE Internet of Things Journal, 4(3), 772–782.
Nkenyereye, L., Liu, C. H., & Song, J. S. (2019). Towards secure and privacy preserving collision avoidance system in 5G fog based internet of vehicles. Future Generation Computer Systems, 95, 488–499.
Ma, M., He, D., Wang, H., Kumar, N., & Choo, K. K. R. (2019). An efficient and provably secure authenticated key agreement protocol for fog-based vehicular ad-hoc networks. IEEE Internet of Things Journal, 6(5), 8065–8075.
Maged Hamada Ibrahim. (2016). Octopus: An edge-fog mutual authentication scheme. IJ Network Security, 18(6), 1089–1101.
Dolui, K., & Datta, S. K. (2017). Comparison of edge computing implementations: Fog computing, cloudlet and mobile edge computing. In: 2017 Global Internet of Things Summit (GIoTS), (pp. 1–6). IEEE.
Shen, J., Yang, H., Wang, A., Zhou, T., & Wang, C. (2019). Lightweight authentication and matrix-based key agreement scheme for healthcare in fog computing. Peer-to-Peer Networking and Applications, 12, 924–933.
Cui, Mingming, Han, Dezhi, & Wang, Jun. (2019). An efficient and safe road condition monitoring authentication scheme based on fog computing. IEEE Internet of Things Journal, 6(5), 9076–9084.
Pengfei, H., Ning, H., Qiu, T., Song, H., Wang, Y., & Yao, X. (2017). Security and privacy preservation scheme of face identification and resolution framework using fog computing in internet of things. IEEE Internet of Things Journal, 4(5), 1143–1155.
Srinivas, J., Das, A. K., Kumar, N., & Rodrigues, J. J. (2018). Cloud centric authentication for wearable healthcare monitoring system. IEEE Transactions on Dependable and Secure Computing, 17(5), 942–956.
Guan, Y., Shao, J., Wei, G., & Xie, M. (2018). Data security and privacy in fog computing. IEEE Network, 99, 1–6.
Wazid, M., Das, A. K., Kumar, N., & Vasilakos, A. V. (2019). Design of secure key management and user authentication scheme for fog computing services. Future Generation Computer Systems, 91, 475–492.
Zhong, H., Wen, J., Cui, J., & Zhang, S. (2016). Efficient conditional privacy-preserving and authentication scheme for secure service provision in vanet. Tsinghua Science and Technology, 21(6), 620–629.
Dolev, D., & Yao, A. (1983). On the security of public key protocols. IEEE Transactions on Information Theory, 29(2), 198–208.
Bellare, M., Pointcheval, D., & Rogaway, P. (2000). Authenticated key exchange secure against dictionary attacks. In: International conference on the theory and applications of cryptographic techniques, pages, (pp. 139–155). Springer.
Jakobsson, M., & Pointcheval, D. (2001). Mutual authentication for low-power mobile devices. In: International conference on financial cryptography, (pp. 178–195). Springer.
Lo, N.-W., & Tsai, J.-L. (2015). An efficient conditional privacy-preserving authentication scheme for vehicular sensor networks without pairings. IEEE Transactions on Intelligent Transportation Systems, 17(5), 1319–1328.
Jianhong, Z., Min, X., & Liying, L. (2014). On the security of a secure batch verification with group testing for vanet. International Journal of Network Security, 16(5), 351–358.
Tsai, J.-L., & Lo, N.-W. (2015). A privacy-aware authentication scheme for distributed mobile cloud computing services. IEEE Systems Journal, 9(3), 805–815.
Bayat, M., Barmshoory, M., Rahimi, M., & Aref, M. R. (2015). A secure authentication scheme for vanets with batch verification. Wireless Networks, 21(5), 1733–1743.
Odelu, V., Das, A. K., Wazid, M., & Conti, M. (2018). Provably secure authenticated key agreement scheme for smart grid. IEEE Transactions on Smart Grid, 9(3), 1900–1910.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Rana, S., Mishra, D., Lal, C. et al. Authenticated Message-Exchange Protocol for Fog-Assisted Vehicular Cloud Computing. Wireless Pers Commun 131, 1295–1312 (2023). https://doi.org/10.1007/s11277-023-10480-7
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-023-10480-7