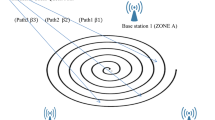
Abstract
Conventionally, the countries viewed the integrity of physical international border as a very challenging task. As, with theincreasing risks of terrorist activity, illegal transportation of peoples, weapons and drugs, the countries face unrivaled challenges in securing their borders efficiently. To cater these challengesvariousconformist approaches were formed in the recent past. However, all such approaches require a thorough manual intervention and high maintenance costs. This advocated to use new technologies which can decrease the maintenance costs and increase the performance of the border surveillance system. Recently Linear Wireless Sensor Networks (LWSN) have attracted the researcher due to the type of topology used in LWSN for the security of linear structures. As the international borders are also linear in nature, so the LWSN could be a best option for the security of these borders. In the era of wireless technologies, energy consumption and data security are the most challenging tasks. This works reveals the minimization of the energy consumption rate on the constrained sensor nodes and, ensuring the privacy of the shared data. Recently, Zone Based Routing Protocol (ZRP) have emerged as one of the efficient routing protocols to improve energy consumption and packet delivery ratio. The efficacy of this work demonstrates the applicability of the A* algorithm with a base of ZRP that enhances the communication flow, packet delivery ratio and energy consumption rate. The results obtained after the simulation done on NS2 on time duration from 0 to 60 s, have shown better performance (08–10%) of the proposed approach when compared to the state of art approaches for all the parameters namely communication overhead, packet delivery ratio and average energy consumption.









Similar content being viewed by others
Data availability
“There is no datasets generated or used “.
References
Hammoudeh, M., Al-Fayez, F., Lloyd, H., Newman, R., Adebisi, B., Bounceur, A., & Abuarqoub, A. (2017). A wireless sensor network border monitoring system: Deployment issues and routing protocols.". IEEE Sensors Journal, 17, 2572–2582.
Athmani, S., Djallel Eddine, B., Azeddine, B. (2013) Hierarchical energy efficient intrusion detection system for black hole attacks in WSNs." In 2013 World Congress on Computer and Information Technology (WCCIT), pp. 1–5. IEEE
Bagyaveereswaran, V., Mathur, T. D., Gupta, S., & Arulmozhivarman, P. (2016). Performance comparison of next generation controller and MPC in real time for a SISO process with low cost DAQ unit. Alexandria Engineering Journal, 55(3), 2515–2524.
Kavidha, V., & Ananthakumaran, S. (2019). Novel energy-efficient secure routing protocol for wireless sensor networks with Mobile sink. Peer-to-Peer Networking and Applications, 12(4), 881–892.
Singh, S. (2020) An energy aware clustering and data gathering technique based on nature inspired optimization in WSNs." Peer-to-Peer Networking and Applications: 1–18.
Bejaoui, C., Alexandre, G., Abdennaceur, K. (2015) Improved election of cluster heads in LEACH." In 2015 IEEE/ACS 12th International Conference of Computer Systems and Applications (AICCSA), pp. 1–4. IEEE
Butun, I., Morgera, S. D., & Sankar, R. (2013). A survey of intrusion detection systems in wireless sensor networks. IEEE communications surveys & tutorials, 16(1), 266–282.
Kumaramangalam, M.V., Kandasamy, A., Chandrasekaran, K. (2014) Zone-based routing protocol for wireless sensor networks." International Scholarly Research Notices
Ghosh, K., Sarmistha, N., Das, P. K., & Mahima, M. (2018). Intrusion detection at international borders and large military barracks with multi-sink wireless sensor networks: an energy efficient solution.". Wireless Personal Communications, 98, 1083–1101.
Arfaoui, I., & Noureddine, B. (2019). A border surveillance system using WSN under various environment characteristics.". International Journal of Sensor Networks, 30, 263–278.
Nasser, N., Al-Yatama, A., & Saleh, K. (2013). Zone-based routing protocol with mobility consideration for wireless sensor networks. Telecommunication Systems, 52(4), 2541–2560.
Sharawi, M., Emary, E., Saroit, I.A. and El-Mahdy, H., (2015). "WSN's energy-aware coverage preserving optimization model based on multi-objective bat algorithm." In 2015 IEEE Congress on Evolutionary Computation (CEC), pp. 472–479. IEEE
Benzerbadj, A., Bouabdellah, K., Ahcène, B., & Mohammad, H. (2018). Surveillance of sensitive fenced areas using duty-cycled wireless sensor networks with asymmetrical links.". Journal of Network and Computer Applications, 112, 41–52.
Clausen, T., Philippe, J, eds. "RFC3626: Optimized link state routing protocol (OLSR)." (2003).
Pitchai, R., Reshma, G., & Raja, J. (2020). An efficient packet image transmission based on texture content for border side security using sensor networks. International Journal of Computer Aided Engineering and Technology, 13(1–2), 63–72.
Kong, J. H., Ang, L. M., & Seng, K. P. (2015). A comprehensive survey of modern symmetric cryptographic solutions for resource constrained environments. Journal of Network and Computer Applications, 49, 15–50.
Akbaş, M. İ, & Turgut, D. (2013). Lightweight routing with dynamic interests in wireless sensor and actor networks.". Ad Hoc Networks, 8, 2313–2328.
Varshney, S., Kumar, C., Swaroop, A., Khanna, A., Gupta, D., Rodrigues, J. J., & De Albuquerque, V. H. C. (2018). Energy efficient management of pipelines in buildings using linear wireless sensor networks.". Sensors, 18, 2618.
Mutlag, A. A., Mohd Khanapi, A. G., Arunkumar, N., Mazin Abed, M., & Othman, M. (2019). Enabling technologies for fog computing in healthcare IoT systems.". Future Generation Computer Systems, 90, 62–78.
Zheng, Yi., Yuwen, W., Zhenzhen, L., Li, D., Yu, J., Hong, Z. (2014) A mobility and load aware OLSR routing protocol for UAV mobile ad-hoc networks. : 1–019.
Brahmbhatt, S., Aishwary, K., Gaurav, S. (2015) SSLSM: signal strength based link stability estimation in MANETs." In 2015 International Conference on Computational Intelligence and Communication Networks (CICN), pp. 173–177. IEEE, 2015.
Tang, B., Jin, W., Xuehua, G., Yuhui, Z., & Jeong-Uk, K. (2012). A novel data retrieving mechanism in wireless sensor networks with path-limited mobile sink. J. Grid Distrib. Comput, 5, 133–140.
Dhamdhere, S. D., Guru, S. K., & Pune, C. D. (2014). Robust data collection in wireless sensor networks with mobile sinks. J. Comput. Sci. Inf. Technol, 5, 4999–5002.
Mitra, R., & Sharma, S. (2018). Proactive data routing using controlled mobility of a mobile sink in wireless sensor networks. Computers & Electrical Engineering, 70, 21–36.
Vahabi, S., Mohammadreza, E., & Seyed Ebrahim, D. (2019). Integration of geographic and hierarchical routing protocols for energy saving in wireless sensor networks with mobile sink.". Wireless Networks, 25, 2953–2961.
Gallegos, A., Taku, N., Tomoko, I., Yoshio, N. (2016) Simulation study of maximum amount shortest path routing in wireless sensor networks using ns-3." In 2016 Eighth International Conference on Ubiquitous and Future Networks (ICUFN), pp. 198–204. IEEE
Gallegos, A., Noguchi, T., Izumi, T., & Nakatani, Y. (2018). Zone-based energy aware data collection protocol for WSNs. IEICE Transactions on Communications, 101(3), 750–762.
Hammoudeh, M. (2016) Putting the lab on the map: A wireless sensor network system for border security and surveillance. ACM, pp. 1–1. 2016.
Laouira, Mohammed Lamine, AbdelkrimAbdelli, Jalel Ben Othman, and Hyunbum Kim. "An efficient WSN based solution for border surveillance." IEEE Transactions on Sustainable Computing (2019).
Nikookar, H., and H. Monsuur. (2018). Challenges for cooperative wireless sensor networks in border control applications." In NL ARMS Netherlands Annual Review of Military Studies 2018, pp. 131–142. TMC Asser Press
Mostafaei, H., Chowdhury, M. U., & Obaidat, M. S. (2018). Border surveillance with WSN systems in a distributed manner. IEEE Systems Journal, 12(4), 3703–3712.
Haney, K. (2020) Re-evaluating coverage metrics for wireless sensor network border security applications.
Lessin, A. M., Lunday, B. J., & Hill, R. R. (2019). A multi-objective, bilevel sensor relocation problem for border security. Taylor and Francis IISE Transactions, 51(10), 1091–1109.
Varshney, S., Kumar, C., & Swaroop, A. (2021). Lightning-based lion optimization algorithm for monitoring the pipelines using linear wireless sensor network. Wireless Personal Communications, 117, 2475–2494.
Yang, H (2023) A practical method for connectivity and coverage reliability analysis for linear wireless sensor networks. Ad Hoc Networks: 103183
Varshney, S., Kumar, C., & Swaroop, A. (2022). Pipeline surveillance along the international border using hybrid optimization algorithm." Journal of Ambient Intelligence and Humanized Computing: 1–9.
Yang, H.-B. (2023). Reliability comparison between plain-based and cluster-based linear wireless sensor networks. IEEE Sensors Journal, 23(6), 6303–6311.
Funding
“The authors declare that no funds, grants, or other support were received during the preparation of this manuscript.”
Author information
Authors and Affiliations
Contributions
“All authors contributed to the study conception, design, preparation and analysis. The first draft of the manuscript was written by all authors. All authors read and approved the final manuscript.”
Corresponding author
Ethics declarations
Conflict of interest
“The authors have no relevant financial or non-financial interests to disclose.”
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Varshney, S., Kumar, C. & Swaroop, A. Sensor Architecture and Routing Algorithm for Surveillance of International Border Using Linear Wireless Sensor Network. Wireless Pers Commun 132, 549–569 (2023). https://doi.org/10.1007/s11277-023-10624-9
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-023-10624-9