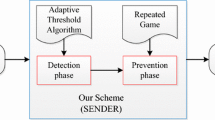
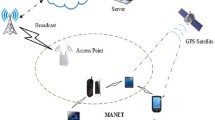
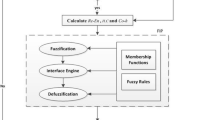
Abstract
Cognitive radio technology is aimed at utilizing the maximum available licensed spectrum for secondary users. However, the performance of a cognitive radio mobile ad hoc network can be degraded significantly due to selfish nodes that preoccupy idle licensed spectrum. Solving selfish attacks has become an important task in cognitive radio mobile ad hoc networks. We propose a selfish node detection algorithm that can solve the miss detection problem that happened with existing selfish node detection methods. The proposed algorithm reflects network errors to increase detection performance. In the simulation, our proposed algorithm is efficient and reliable for selfish node detection in various network conditions.








Similar content being viewed by others
Data Availability
Data sharing does not apply to this article as no datasets were generated or analyzed during the current study.
References
Zhang, W., Mallik, R. K., & Letaief, K. B. (2009). Optimization of cooperative spectrum sensing with energy detection in cognitive radio networks. IEEE Transactions on Wireless Communications, 8(9), 5761–5766. https://doi.org/10.1109/TWC.2009.12.081710
Feng, J., Lu, G., & Min, X. (2014). Social incentives for cooperative spectrum sensing in distributed cognitive radio networks. KSII Transactions on Internet and Information Systems, 8(2), 134–144. https://doi.org/10.3837/tiis.2014.02.002
Dai, J., & Wang, S. (2017). Clustering-based spectrum sharing strategy for cognitive radio networks. IEEE Journal on Selected Areas in Communications, 35(1), 228–237. https://doi.org/10.1109/JSAC.2016.2633698
Muñoz, C., Rodriguez-Colina, E., Pedraza, L. F., & Paez, I. P. (2020). Detection of dynamic location primary user emulation on mobile cognitive radio networks using USRP. Journal on Wireless Communications Network. https://doi.org/10.1186/s13638-020-1657-0
Kockaya, K., & Develi, I. (2020). Spectrum sensing in cognitive radio networks: threshold optimization and analysis. Journal on Wireless Communications and Networking. https://doi.org/10.1186/s13638-020-01870-7
Lee, K. E., Park, J. G., & Yoo, S. J. (2021). Intelligent cognitive radio ad-hoc network: Planning, learning and dynamic configuration. Electronics, 10(3), 254. https://doi.org/10.3390/electronics10030254
Hyder, C. S., Grebur, B., & Xiao, L. (2012). Defense against spectrum sensing data falsification attacks in cognitive radio networks. In M. Rajarajan, F. Piper, H. Wang, & G. Kesidis (Eds.), Security and Privacy in Communication Networks (LNICST) (pp. 154–171). Cham: Springer.
Gao, Z., Zhu, H., Li, S., Du, S., & Li, X. (2012). Security and privacy of collaborative spectrum sensing in CRAHNs. IEEE Wirel Comm, 19(4), 106–112. https://doi.org/10.1109/MWC.2012.6393525
Minho, J., Han, L., Dohoon, K., & Peter, H. I. (2013). Selfish attacks and detection in cognitive radio ad-hoc networks. IEEE Network, 27(3), 46–50. https://doi.org/10.1109/MNET.2013.6523808
Tan, K., Jana, S., Pathak, P. H., & Mohapatra, P. (2013). On insider misbehavior detection in cognitive radio networks. IEEE Network, 27(3), 4–9. https://doi.org/10.1109/MNET.2013.6523801
Zhang, L., Ding, G., Wu, Q., & Song, F. (2016). Defending against Byzantine attack in cooperative spectrum sensing: Defense reference and performance analysis. IEEE Access, 4, 4011–4024. https://doi.org/10.1109/ACCESS.2016.2593952
Qiuming, L., Yong, L., Yun, L., & Jun, Z. (2016). Throughput capacity of selfish wireless ad hoc networks with general node density. Information, 7(1), 1–16. https://doi.org/10.3390/info7010016
Al-Mathehaji, Y., Boussakta, S., Johnston, M., & Fakhrey, H. (2017). Defeating SSDF attacks with trusted nodes assistance in cognitive radio networks. IEEE Sensors Letters, 1(4), 1–4. https://doi.org/10.1109/LSENS.2017.2731623
Nie, G., Ding, G., Zhang, L., & Wu, Q. (2017). Byzantine defense in collaborative spectrum sensing via Bayesian learning. IEEE Access, 5, 20089–20098. https://doi.org/10.1109/ACCESS.2017.2756992
Zhao, F., Li, S., & Feng, J. (2019). Securing cooperative spectrum sensing against DC-SSDF attack using trust fluctuation clustering analysis in cognitive radio networks. Wireless Communications and Mobile Computing. https://doi.org/10.1155/2019/3174304
Yao, D., Yuan, S., Lv, Z., Wan, D., & Mao, W. (2020). An enhanced cooperative spectrum sensing scheme against SSDF attack based on Dempster-Shafer evidence theory for cognitive wireless sensor networks. IEEE Access, 8, 175881–175890. https://doi.org/10.1109/ACCESS.2020.3026738
Xu, Z., Sun, Z., Guo, L., Muhammad, Z. H., & Chintha, T. (2022). Joint spectrum sensing and spectrum access for defending massive SSDF attacks: A novel defense framework. Chinese Journal of Electronics, 31, 240–254. https://doi.org/10.1049/cje.2021.00.090
Fu, Y., & He, Z. (2023). Massive SSDF attackers identification in cognitive radio networks by using consistent property. IEEE Transactions on Vehicular Technology. https://doi.org/10.1109/TVT.2023.3253865
Mohsen, R. M., & Naima, K. (2018). Security threats and countermeasures of MAC layer in cognitive radio networks. Ad Hoc Networks, 70, 85–102. https://doi.org/10.1016/j.adhoc.2017.11.003
Zhang, L., Nie, G., Ding, G., Wu, Q., Zhang, Z., & Han, Z. (2019). Byzantine attacker identification in collaborative spectrum sensing: A robust defense framework. IEEE Transactions on Mobile Computing, 18(9), 1992–2004. https://doi.org/10.1109/TMC.2018.2869390
Fu, Y., & He, Z. (2019). Bayesian-inference-based sliding window trust model against probabilistic SSDF attack in cognitive radio networks. IEEE Systems Journal, 14(2), 1764–1775. https://doi.org/10.1109/JSYST.2019.2936263
Singh, H., Kumar, V., Saxena, K., Boncho, B., & Prasad, R. (2020). Proposed model for radio wave attenuation due to rain (RWAR). Wireless Personal Communications, 115, 791–807. https://doi.org/10.1007/s11277-020-07598-3
Khaled, H., Ahmad, I., Habibi, D., & Phung, Q. V. (2020). A secure and energy-aware approach for cognitive radio communications. IEEE Open Journal of the Communications Society, 1, 900–915. https://doi.org/10.1109/OJCOMS.2020.3009241
Kumar, S., & Majhi, S. (2020). Blind symbol timing offset estimation for offset-QPSK modulated signals. ETRI Journal, 42, 324–332. https://doi.org/10.4218/etrij.2019-0199
Singh, H., Prasad, R., & Bonev, B. (2018). The studies of millimeter waves at 60 GHz in outdoor environments for IMT applications: A state of art. Wireless Personal Communications, 100, 463–474. https://doi.org/10.1007/s11277-017-5090-6
Fahiem, A., Kumar, P., & Soumyadev, M. (2022). Beacon non-transmission attack and its detection in intelligent transportation systems. Internet of Things. https://doi.org/10.1016/j.iot.2022.100602
Pirayesh, H., & Zeng, H. (2022). Jamming attacks and anti-jamming strategies in wireless networks: A comprehensive survey. IEEE Communications Surveys & Tutorials, 24(2), 767–809. https://doi.org/10.1109/COMST.2022.3159185
Nidhi, A. M., & Prasad, R. (2020). Overview of 5G new radio and carrier aggregation: 5G and beyond networks. International Symposium on Wireless Personal Multimedia Communications, Okayama, Japan, pp 1–6. https://doi.org/10.1109/WPMC50192.2020. 9309496
Quy, V. K., Nam, V. H., Linh, D. M., Ngoc, L. A., & Gwanggil, J. (2022). Wireless communication technologies for IoT in 5G: Vision, applications, and challenges. Wireless Communications and Mobile Computing. https://doi.org/10.1155/2022/3229294
Xiaozhen, L., Liang, X., Pengmin, L., Xiangyang, J., Chenren, X., Shui, Y., & Weihua, Z. (2023). Reinforcement learning-based physical cross-layer security and privacy in 6G. IEEE Communications Surveys & Tutorials, 25(1), 425–466. https://doi.org/10.1109/COMST.2022.3224279
Quy, V. K., Chehri, A., Quy, N. M., Han, N. D., & Ban, N. T. (2023). Innovative trends in the 6G Era: A comprehensive survey of architecture, applications, technologies, and challenges. IEEE Access, 11, 39824–39844. https://doi.org/10.1109/ACCESS.2023.3269297
Acknowledgements
N/A
Funding
N/A
Author information
Authors and Affiliations
Contributions
The study conception and methodology are performed by V.K. Quy and N.D. Han. Material preparation, data collection and analysis were performed by V.K. Quy, N.V. Hau, D.M. Linh, N.T. Ban, and N.D. Han. The first draft of the manuscript was written by V.K. Quy and N.D. Han. All authors commented on previous versions of the manuscript. All authors read and approved the final manuscript. The corresponding author is Dr. Nguyen Dinh Han.
Corresponding author
Ethics declarations
Conflict of interest
The authors declare no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Quy, V.K., Nguyen, VH., Linh, D.M. et al. An Improved Selfish Node Detection Algorithm for Cognitive Radio Mobile Ad Hoc Networks. Wireless Pers Commun 133, 683–697 (2023). https://doi.org/10.1007/s11277-023-10788-4
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-023-10788-4