Abstract
The networks (SDN) poses many potential security threats because of its principle of dissociating the network management interface from the underneath networking components and making a programmable networking system. Many security countermeasures have been proposed regarding this current trending environment, but none of the research has considered the existing vulnerabilities in SDN entities. This paper demonstrates the vulnerabilities using CVSS in the first place and then identifies the mutual relationship between the vulnerabilities using Bayesian network methodology.


Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.References
Akhunzada A, Ahmed E, Gani A, Khan MK, Imran M, Guizani S (2015) Securing software defined networks: taxonomy, requirements, and open issues. IEEE Commun Mag 53(4):36–44
CVSS Special Interest Group(SIG), Common vulnerability scoring system v3.0: Specification, FIRST.ORG, Inc., (Jun 2015)
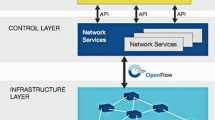
Open Networking Foundation Member, OpenFlow switch specificaion: version 1.3.0, The Open Networking Foundation, (Jun 2012)
Shu Z, Wan J, Li D, Lin J, Vasilakos AV, Imran M (2016) Security in software-defined networking: threats and countermeasures. Mob Netw Appl 21(5):764–776
Karmakar KK, Varadharajan V, Tupakula U (2016) On the design and implementation od a security architecture for software defined network. IEEE international conference on HPCC/Ssart city/data science and system 671–678
Al-Shaer E, Al-Haj S (2010) Flowchecker: configuration analysis and verification of federated OpenFlow infrastructures. In: Proceedings of the 3rd ACM workshop on assurable and usable security configuration, 37–44
Shin S, Yegneswaran V, Porras P, Gu G (2013) AVANT-GUARD: scalable and vigilant switch flow management in software-defined networks. ACM SIGSAC conference on computer & communications security 413–424
Kloti R, Kotronis V, Smith P (2013) OpenFlow: a security analysis. IEEE international conference on network protocols pp. 1–6
Herman S, Lambert S, Ostwald T, Shostack A (2006) Uncover security design Flwas using the STRIDE approach, http://msdn.microsoft.com/en-gb/magazine/cc163519.asp
Saini V, Duan Q, Paruchuri V (2008) Threat modeling using attack trees. J Comput Sci Coll 23(4):124–131
Wang H, Xu L, Gu G (2015) FloodGuard: a DoS attack prevention extension in software-defined networks. In: IEEE/IFIP international conference on dependable systems and networks pp. 239–250
Wang H, Xu L, Gu G (2015) OF-GUARD: a DoS attack prevention extension in software-defined networks. In: IEEE/IFIP international conference on dDependable systems and networks
Wang R, Jia Z, Ju L (2015) An entropy-based distributed DDoS detection mechanism in software-defined networking. In: IEEE Trustcom/BigDataSE/ISPA 310–317
Fonseca P, Bennesby R, Mota E, Passito A (2012) A replication component for resilient OpenFlow-based networking. In: IEEE network operations and management symposium (NOMS) 933–939
Wang S, Chavez K G, Kandeepan S (2017) SECO: SDN sEcure COntroller algorithm for detecting and defending denial of service attacks. In: International conference on information and communication technology (ICoIC7), 1–6
Wei L, Fung C (2015) FlowRanger: A request prioritizing algorithm for controller DoS attacks in Software Defined Networks. In: IEEE international conference on communications (ICC) 5254–5259
Dao NN, Park J, Cho S (January 2015) A feasible method to combat against DDoS attack in SDN network. In: International conference on information networking (ICOIN) 309–311
Sahay R, Blanc G, Zhang Z, Debar H (2015) Towards autonomic DDoS mitigation using software defined networking. Network and distributed system security (NDSS) symposium, 1–7
Dridi L, Zhani MF (2016) SDN-GUARD: DoS attacks mitigation in SDN networks. In: International conference on cloud networking 212–217
Porras P, Shin S, Yegneswaran V, Fong M, Tyson M, Gu G (2012) A security enforcement kernel for OpenFlow networks. In: Proceedings of the first workshop on Hot topics in software defined networks. ACM, 121–126
Canini M, Venzano D, Pereni P, Kosti D, Rexford J (2012) A NICE way to test OpenFlow applications. In: USENIX conference on networked systems design and implementation 10–10
Son S, Shin S, Yegneswaran V, Porras P, Gu G (June 2013) Model checking invariant security properties in OpenFlow. In: IEEE international conference on communications (ICC)
Mai H, Khurshid A, Agarwal R, Caesar M, Godfrey P, King S (2011) Debugging the data plane with anteater. In: ACM SIGCOMM 2011 conference, 29301
Kazemian P, Chan M, Zeng H, Varghese G, McKeown N, Whyte S (2013) Real time network policy checking using header space analysis. In: USENIX symposium on networked systems design and implementation, pp 99–112
Hp switch software - openflow supplement, https://support.hpe.com/hpsc/doc/public/display?docId=emr_na-c03170243, 1-32 (February 2012)
Horny M (2014) Bayesian networks, Bostom University School of Public Health,Technical Report, No.5, 1–14
Liy Y, Man H (2005) Network vulnerability assessment using Bayesian networks. In: Proceedings of the SPIE, Volume 5812, 61–71 )
Wang L, Islam T, Long T, Singhal A, Jajioda S (2008) An attack graph-based security metric. In: IFIP WG 11.3 working conference on data and applications security, 283 – 296
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Deb, R., Roy, S. Dynamic vulnerability assessments of software-defined networks. Innovations Syst Softw Eng 16, 45–51 (2020). https://doi.org/10.1007/s11334-019-00337-3
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11334-019-00337-3