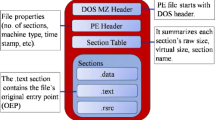
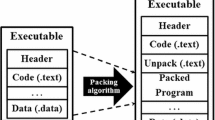
Abstract
Malware is one of the major concerns in computer security. The availability of easy to use malware toolkits and internet popularity has led to the increase in number of malware attacks. Currently signature based malware detection techniques are widely used. However, malware authors use packing techniques to create new variants of existing malwares which defeat signature based malware detection. So, it is very important to identify packed malware and unpack it before analysis. Dynamic unpacking runs the packed executable and provides an unpacked version based on the system. This technique requires dedicated hardware and is computationally expensive. As each individual packer uses its own unpacking algorithm it is important to have a prior knowledge about the packer used, in order to assist in reverse engineering. In this paper, we propose an efficient framework for packer identification problem using Byte plot and Markov plot. First packed malware is converted to Byte plot and Markov plot. Later Gabor and wavelet based features are extracted from Byte plot and Markov plot. We used SVMs (Support Vector Machine) in our analysis. We performed our experiments on nine different packers and we obtained about 95 % accuracy for nine of the packers. Our results show features extracted from Markov plot outperformed features extracted from Byte plot by about 3 %. We compare the performance of Markov plot with PEID (Signature based PE identification tool). Our results show Markov plot produced better accuracy when compared to PEID. We also performed multi class classification using Random Forest and achieved 81 % accuracy using Markov plot based features.








Similar content being viewed by others
References
Symantec, Internet Security Threat Report, 2011 trends, Vol. 17 Main Report, April 2012. Retrieved on 8/10/2012 http://www.symantec.com/content/en/us/enterprise/other_resources/b-istr_main_report_2011_21239364.en-us.pdf
Dell Sonic wall Inc, Anatomy of a cyber-attack, Retrieved on 8/10/2012. http://www.sonicwall.com/downloads/EB_Anatomy_of_a_CyberAttack_Final.pdf
Yan, W., Zhang, Z., Ansari, N.: Revealing packed malware. IEEE Secur. Priv. 7(5), 65–69 (2008). doi:10.1109/MSP.2008.126
Shadowserver, Packer Statistics, The Shadowserver Foundation, http://www.shadowserver.org/wiki/pmwiki.php/Stats/PackerStatistics
Armadillo, Digital River Accessed on June 2014 http://www.digitalriver.com/Armadillo
Themida Advanced windows software protection system. Accessed on June 2014 http://www.oreans.com/themida.php
PECompact Powerful executable compression for software developers and vendors. Accessed on June 2014 http://bitsum.com/pecompact/
Installshield Software Installation Solution Accessed on June 2014 http://www.installshield.com/
Ultimate Packer for Executables UPX Accessed on June 2014 http://upx.sourceforge.net/
Telock - free PE-File Encryptor/-Compressor Accessed on June 2014 http://www.telock.com-about.com
Ban, T., Isawa, R., Guo, S., Inoue, D., Nakao, K.: Efficient malware packer identification using support vector machines with spectrum kernel. In: AsiaJCIS pp. 69–76 (2013)
PEiD, most recent release (PEiD 0.95) could be downloaded from http://www.softpedia.com/
Lyda, R., Hamrock, J.: Using entropy analysis to find encrypted and packed malware. IEEE Secur. Priv. 5, 40–45 (2007)
Perdisci, R., Lanzi, A., Lee, W.: Classification of packed executables for accurate computer virus detection. Pattern Recogn. Lett. 29, 1941–1946 (2008)
Kolter, J.Z., Maloof, M.A.: Learning to detect and classify malicious executables in the wild. J. Mach. Learn. Res. 7, 2721–2744 (2006)
Sun, L., Versteeg, S., Boztaş, S., Yann, T.: Pattern recognition techniques for the classification of malware packers. In: Proceedings of the 15th Australasian Conference on Information Security and Privacy, ser. ACISP’10. Springer, Berlin, pp. 370–390 (2010)
Ugarte-Pedrero, X., Santos, I., Bringas, P.G.: Structural feature based anomaly detection for packed executable identification. In: Proceedings of the 4th International Conference on Computational Intelligence in Security for Information Systems (CISIS), pp. 50–57 (2011)
Stewart, J.: OllyBonE v0.1, Break-on-Execute for OllyDbg (2006)
Valsmith, Q.D.: Covert debugging: circumventing software armoring techniques, Black Hat USA (2007)
Martignoni, L., Christodorescu, M., Jha, S.: OmniUnpack: fast, generic, and safe unpacking of malware. In: 23rd Annual Computer Security Applications Conference (ACSAC) (2007)
Shafiq, M., Tabish, S., Farooq, M.: PE-Probe: leveraging packer detection and structural information to detect malicious portable executables. In: Proceedings of the Virus Bulletin Conference (VB), pp. 29–33 (2009)
Farooq, M.: PE-Miner: mining structural information to detect malicious ex-ecutables in realtime. In: Proceedings of the 12th International Symposium on Recent Advances in Intrusion Detection (RAID). Springer, Heidelberg, pp. 121–141 (2009)
Ban, T., Nakao, K.: Application of string kernel based support vector machine for malware packer identification. In: Proceedings of the 2013 International Joint Conference on Neural Networks, ser. IJCNN’13. San Francisco, CA: Morgan Kaufmann Publishers Inc. (2013)
Levenshtein, V.: Binary codes capable of correcting deletions, insertions and reversals. Sov. Phys. Dokl. 10, 707 (1966)
Conti, G., Bratus, S., Shubina, A., Lichtenberg, A., Ragsdale, R., Perez-Alemany, R., Sangster, B., Supan, M.: A visual study of binary fragment types Black Hat USA (2010)
Conti, G., Bratus, S., Sangster, B., Ragsdale, S., Supan, M., Lichtenberg, A., Perez, R., Shubina, A.: Automated mapping of large binary objects using primitive fragment type classification digital forensics research conference (DFRWS) (2010)
Yoo, I.: Visualizing windows executable viruses using self-organizing maps. In: 2004 International Workshop on Visualization for Cyber Security (VizSec)
Quist, D.A., Liebrock, L.M.: Visualizing compiled executables for malware analysis. In: International Workshop on Visualization for Cyber Security (VizSec), pp. 27–32 (2009)
Kancherla, K., Mukkamala, S.: Image visualization based malware detection. In: CICS, pp. 40–44 (2013)
Akansu, A.N., Serdijn, W.A., Selesnick, I.W.: Wavelet transforms in signal processing: a review of emerging applications. Phys. Commun. 3(1), 1–18 (2010)
Grigorescu, S.E., Petkov, N., Kruizinga, P.: Comparison of texture features based on gabor filters. IEEE Trans. Image Process. 1(10), 1160–1167 (2002)
Offensive Computing Open Malware Accessed on May 2013 http://www.offensivecomputing.net/
Boser, B.E., Guyon, I.M., Vapnik, V.N.: A training algorithm for optimal margin classifiers. Comparison of classifier methods: a case study in handwritten digit recognition. In: Proceedings of the 12th International Conference on Pattern Recognition and Neural Networks, Jerusalem, pp. 77–87 (1992)
Lee, J.H., Lin, C.J.: Automatic model selection for support vector machines, Technical Report, Department of Computer Science and Information Engineering, National Taiwan University (2000)
Chang, C.C., Lin, C.J.: LIBSVM: A Library for Support Vector Machines. National Taiwan University, Taipei, Department of Computer Science and Information Engineering (2001)
Egan, J.P.: Signal Detection Theory and ROC Analysis. Academic Press, New York (1975)
KRebel, U.: Pairwise classification and support vector machines. In: Scholkopf, B., Burges, C.J.C., Smola, A.J. (eds.) Advances in Kernel Methods-Support Vector Learning. MIT Press, Cambridge (1998)
Friedman, J.H.: Another approach to polychotomous classification. Technical report, Department of Statistics, Stanford University (1996)
Platt, J.C., Cristianini, N., Shawe-Taylor, J.: Large margin DAGs for multiclass classification. In: Solla, S.A., Leen, T.K., Müller, K.-R. (eds.) Advances in Neural Information Processing Systems 12 (NIPS-99), pp. 547–553. MIT Press, Cambridge (2000)
Breiman, L.: Random forests. J. Mach. Learn. 45, 5–32 (2001)
Salford Systems, TreeNet, CART, Random Forests Manual
Crammer, K., Singer, Y.: On the Learnability and Design of Output Codes for Multiclass Problems. In: Computational learning theory, pp. 35–46 (2000)
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Kancherla, K., Donahue, J. & Mukkamala, S. Packer identification using Byte plot and Markov plot. J Comput Virol Hack Tech 12, 101–111 (2016). https://doi.org/10.1007/s11416-015-0249-8
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11416-015-0249-8