Abstract
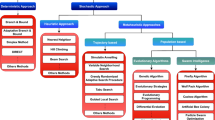
Android-based smartphones are gaining popularity, due to its cost efficiency and various applications. These smartphones provide the full experience of a computing device to its user, and usually ends up being used as a personal computer. Since the Android operating system is open-source software, many contributors are adding to its development to make the interface more attractive and tweaking the performance. In order to gain more popularity, many refined versions are being offered to customers, whose feedback will enable it to be made even more powerful and user-friendly. However, this has attracted many malicious code-writers to gain anonymous access to the user’s private data. Moreover, the malware causes an increase of resource consumption. To prevent this, various techniques are currently being used that include static analysis-based detection and dynamic analysis-based detection. But, due to the enhancement in Android malware code-writing techniques, some of these techniques are getting overwhelmed. Therefore, there is a need for an effective Android malware detection approach for which experimental studies were conducted in the present work using the static features of the Android applications such as Standard Permissions with Application Programming Interface (API) calls, Non-standard Permissions with API-calls, API-calls with Standard and Nonstandard Permissions. To select the prominent features, Feature Selection Techniques (FSTs) such as the BI-Normal Separation (BNS), Mutual Information (MI), Relevancy Score (RS), and the Kullback-Leibler (KL) were employed and their effectiveness was measured using the Linear-Support Vector Machine (L-SVM) classifier. It was observed that this classifier achieved Android malware detection accuracy of 99.6% for the combined features as recommended by the BI-Normal Separation FST.




Similar content being viewed by others
References
http://www.businessinsider.in/This-Chart-Shows-The-Massive-Pricing-Problem-Facing-Apples-iPhone-6/articleshow/39197536.cms. Accessed Oct 2016
https://techcrunch.com/2013/04/16/symantec-mobile-malware/. Accessed Nov 2016
http://www.darkreading.com/mobile/android-app-permission-in-google-play-contains-security-flaw/d/d-id/1328834. Accessed Jan 2017
https://www.eset.com/int/about/newsroom/research/fake-android-apps-bypass-google-play-store-security-installed-200000-times-in-a-month/. Accessed Jan 2017
Chuang, H.-Y., Wang, S.-D.: Machine learning based hybrid behavior models for Android malware analysis. In: IEEE International Conference on Software Quality, Reliability and Security, pp. 201–206 (2015). https://doi.org/10.1109/QRS.2015.37
Qin, Z., Xu, Y., Di, Y., Zhang, Q., Huang, J.: Android malware detection based on permission and behavior analysis. In: International Conference on Cyberspace Technology (CCT 2014), pp. 1–4 (2014). https://doi.org/10.1049/cp.2014.1352
Vinayakumar, R., Soman, K.P., Poornachandran, P.: Deep android malware detection and classification. In: Advances in Computing, Communications and Informatics (ICACCI 2017), pp. 1677–683 (2017)
Ariyapala, K., Do, H.G., Anh, H.N., Ng, W.K., Conti, M.: A host and network based intrusion detection for Android smartphones. In: 30th International Conference on Advanced Information Networking and Applications Workshops (WAINA), pp. 849–854 (2016). https://doi.org/10.1109/WAINA.2016.35
Sanz, B., Santos, I., Ugarte-Pedrero, X., Laorden, C., Nieves, J., Bringas, P.G.: Instance-based anomaly method for Android malware detection. In: International Conference on Security and Cryptography (SECRYPT 2013)
Apvrille, A., Strazzere, T.: Reducing the window of opportunity for Android malware Gotta catchem all. J. Comput. Virol. 8, 61–71 (2012)
Ham, H.-S., Choi, M.-J.: Analysis of Android malware detection performance using machine learning classifiers. In: ICTC (2013)
Vinayakumar, R., Soman, K.P., Poornachandran, P., Sachin Kumar, S.: Detecting Android malware using long short-term memory (LSTM). J. Intell. Fuzzy Syst. 34, 1277–1288 (2018)
Tong, F., Yan, Z.: A hybrid approach of mobile malware detection in Android. J. Parallel Distrib. Comput. 103, 22–31 (2017). https://doi.org/10.1016/j.jpdc.2016.10.012
Feizollah, A., Anuar, N.B., Salleh, R., Suarez-Tangil, G., Furnell, S.: Androdialysis: analysis of Android intent effectiveness in malware detection. Comput. Secur. 65, 121–134 (2017). https://doi.org/10.1016/j.cose.2016.11.007
Aswini, A.M., Vinod, P.: Android malware analysis using ensemble features. In: International Conference on Security, Privacy and Applied Cryptographic Engineering (SPACE 2014), LNCS 8804, pp. 303–318 (2014)
Milosevic, N., Dehghantanha, A., Choo, K.-K.R.: Machine learning aided Android malware classification. Comput. Electr. Eng. 61, 266–274 (2017). https://doi.org/10.1016/j.compeleceng.2017.02.013
Kim, H.-H., Choi, M.-J.: Linux kernel-based feature selection for Android malware detection. In: The 16th Asia-Pacific Network Operations and Management Symposium, pp. 1–4 (2014). https://doi.org/10.1109/APNOMS.2014.6996540
Xiaoyan, Z., Juan, F., Xiujuan, W.: Android malware detection based on permissions. In: International Conference on Information and Communications Technologies (ICT 2014), pp. 1–5 (2014). https://doi.org/10.1049/cp.2014.0605
Zhu, J., Wu, Z., Guan, Z., Chen, Z.: API sequences based malware detection for Android. In: IEEE 12th International Conference on Ubiquitous Intelligence and Computing and IEEE 12th International Conference on Automatic and Trusted Computing and IEEE 15th International Conference on Scalable Computing and Communications and Its Associated Workshops (UIC-ATC-ScalCom), pp. 673–676 (2015). https://doi.org/10.1109/UIC-ATC-ScalCom-CBDCom-IoP.2015.135
Peiravian, N., Zhu, X.: Machine learning for Android malware detection using permission and API calls. In: IEEE 25th International Conference on Tools with Artificial Intelligence (2013). https://doi.org/10.1109/ICTAI.2013.53
Chan, P.P.K., Song, W.-K.: Static detection of Android malware by using permissions and API calls. In: International Conference on Machine Learning and Cybernetics, vol. 1, 82–87 (2014). https://doi.org/10.1109/ICMLC.2014.7009096
Qiao, M., Sung, A.H., Liu, Q.: Merging permission and API features for Android malware detection. In: 5th International Congress on Advanced Applied Informatics (IIAI-AAI 2016), pp. 566–571 (2016). https://doi.org/10.1109/IIAI-AAI.2016.237
Su, M.-Y., Fung, K.-T., Huang, Y.-H., Kang, M.-Z., Chung, Y.-H.: Detection of Android malware: combined with static analysis and dynamic analysis. In: 2016 International Conference on High Performance Computing & Simulation (HPCS), pp. 1013–1018 (2016). https://doi.org/10.1109/HPCSim.2016.7568448
http://stackoverflow.com/questions/18717286/what-are-thecontents-of-an-android-apk-file. Accessed Feb 2017
APKTool. https://ibotpeaches.github.io/Apktool/. Accessed Sept 2016
Battiti, R.: Using mutual information for selecting features in supervised neural net learning. IEEE Trans. Neural Netw. 5(4), 537–550 (1994)
Ling, X.F.: Feature selection. http://courses.washington.edu/ling572/winter2013/slides/class7feature selection.pdf. Accessed Sept 2016
Bonev, B.I.: Feature selection based on information theory. http://www.dccia.ua.es/~boyan/papers/TesisBoyan.pdf. Accessed Sept 2016
Drebin Dataset. https://www.sec.cs.tu-bs.de/~danarp/drebin/. Accessed Oct 2016
Maiorca, D., Ariu, D., Corona, I., Aresu, M., Giacinto, G.: Stealth attacks: an extended insight into the obfuscation effects on Android malware. Comput. Secur. 51, 16–31 (2015). https://doi.org/10.1016/j.cose.2015.02.007
Shahzad, F., Shahzad, M., Farooq, M.: In-execution dynamic malware analysis and detection by mining information in process control blocks of Linux OS. Inf. Sci. 231, 45–63 (2013). https://doi.org/10.1016/j.ins.2011.09.016
Hearst, M.A., Dumais, S.T., Osuna, E., Platt, J., Scholkopf, B.: Support vector machines. IEEE Intell. Syst. Appl. 13(4), 18–28 (1998)
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendix A
Appendix A
1.1 Calculation of precision
Where X \(=\) Benign Files Precision, XT \(=\) Total number of Benign Files, Y \(=\) Malware Files Precision, and YT \(=\) Total number of Malware Files.
1.2 Calculation of recall
Where U \(=\) Benign Files Recall, UT \(=\) Total number of Benign Files, V = Malware Files Recall, and VT \(=\) Total number of Malware Files.
Rights and permissions
About this article
Cite this article
Singh, A.K., Jaidhar, C.D. & Kumara, M.A.A. Experimental analysis of Android malware detection based on combinations of permissions and API-calls. J Comput Virol Hack Tech 15, 209–218 (2019). https://doi.org/10.1007/s11416-019-00332-z
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11416-019-00332-z