Abstract
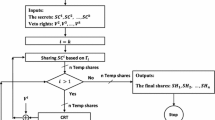
A secret sharing scheme permits a secret to be shared among participants in such a way that only qualified subsets of participants can recover the secret. Secret sharing is useful in management of cryptographic keys. Based on identity, we analyze the secret sharing scheme among weighted participants. Then we present a dynamic scheme about secret sharing among weighted participants. At last, we analyze the secret sharing scheme among weighted participants, which can make all weighted participants verifiable and dynamic.
Similar content being viewed by others
References
G. R. Blakey, Safeguarding cryptographic keys, Proc. of the 1979 AFIPS National Computer Conference, AFIPS Press, Montvale, 1979, 48: 313–317.
A. Shamir, E. W. Chionh, and R. N. Goldman, How to share a secret, Communication of ACM, 1979, 22(11): 612–613.
D. P. Huang, H. Y. Wang, L. S. Huang, Y. Q. Dai, Dynamic threshold secret sharing scheme(in Chinese), Journal of Tsinghua Univ. Sci. and Tech., 2006, 46(1): 102–105.
M. S. Wang, Z. J. Liu, and Y. S. Zhang, Secret sharing among weighted participants, Journal of Beijing Electonic Science and Technology Institute, 2005, 13(2): 1–9.
J. He and E. Dawson, Shared secret reconstruction, Designs, Codes, and Cryptography, 1998, 14(3): 221–237.
John D. Lipson, Chinese remainder and interpolation algorithm, Proceedings of ACM Symposium on Symbolic and Algebraic Computation, ACM Press, 1971, 372–391.
M. Tompa and H. Woll, How to share a secet with cheaters, Journal of Cryptology, 1988, 1(2): 133–139.
C. Padro, G. Saez, and J. Villar, Detection of Cheaters in vector space secret sharing schemes, Designs, Codes, and Cryptography, 1999, 16(1): 75–85.
Author information
Authors and Affiliations
Corresponding author
Additional information
The research is supported by Research Funds of Information Security and Secrecy Laboratory of Beijing Electronic Science & Technology Institute under Grant No. YZDJ0712, partially by National Basic Research Program under Grant No. 2004CB318000, and Beijing Municipal Natural Science Foundation under Grant No. 4063040.
Rights and permissions
About this article
Cite this article
Zhang, Y., Liu, Z. Dynamic and Verifiable Secret Sharing Among Weighted Participants. Jrl Syst Sci & Complex 20, 481–485 (2007). https://doi.org/10.1007/s11424-007-9044-z
Received:
Revised:
Issue Date:
DOI: https://doi.org/10.1007/s11424-007-9044-z