Abstract
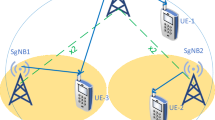
In this paper, we investigate secure communication over cellular uplinks in device-to-device (D2D)-enabled cellular networks. We consider a more general scenario, in which multiple D2D pairs could simultaneously share the same resource block with a specific cellular user. First, an opportunistic access control scheme based on wireless channel gains is proposed, by which the candidate selected set of D2D pairs sharing the same resource block is determined. The proposed scheme could guarantee reliable communications for both cellular users and D2D pairs, and further could combat eavesdroppers while keeping the legitimate cellular user as non-intrusive as possible, regarding D2D pairs as friendly jammers in a non-collaborative way. Then, we derive theoretical results to characterize the security and reliability of the typical cellular and D2D links, respectively. To further support the performance of this hybrid network, we next present an interference threshold optimization model. Our aim is to minimize the connection outage probability (COP) of D2D pairs subject to the secrecy requirement of the cellular user. Finally, simulation results are presented to validate the effectiveness of our proposed scheme.
Similar content being viewed by others
References
Agiwal M, Roy A, Saxena N. Next generation 5G wireless networks: a comprehensive survey. IEEE Commun Surv Tut, 2016, 18: 1617–1655
Asadi A, Wang Q, Mancuso V. A survey on device-to-device communication in cellular networks. IEEE Commun Surv Tut, 2014, 16: 1801–1819
Phunchongharn P, Hossain E, Kim D I. Resource allocation for device-to-device communications underlaying LTEadvanced networks. IEEE Wirel Commun, 2013, 20: 91–100
Ding G R, Wang J L, Wu Q H, et al. Cellular-base-station-assisted device-to-device communications in TV white space. IEEE J Sel Areas Commun, 2016, 34: 107–121
Yu G D, Xu L K, Feng D Q. Joint mode selection and resource allocation for device-to-device communications. IEEE Trans Commun, 2014, 62: 3814–3824
Li B, Fei Z S, Chen H B. Robust artificial noise-aided secure beamforming in wireless-powered non-regenerative relay.IEEE Access, 2016, 4: 7921–7929
Li B, Fei Z S. Robust beamforming and cooperative jamming for secure transmission in DF relay systems. EURASIP J Wirel Commun, 2016, 1: 1–11
Zhang L J, Jin L, Luo W Y, et al. Robust secure transmission for multiuser MISO systems with probabilistic QoS constraints. Sci China Inf Sci, 2016, 59: 022309
Khisti A, Wornell G. Secure transmission with multiple antennas-part I: the MISOME wiretap channel. IEEE Trans Inf Theory, 2010, 56: 3088–3104
Bloch M, Barros J, Rodrigues M R D, et al. Wireless information theoretic security. IEEE Trans Inf Theory, 2011, 54: 2515–2534
Li B, Fei Z S, Chu Z, et al. Secure transmission for heterogeneous cellular networks with wireless information and power transfer. IEEE Syst J, 2017. doi: 10.1109/JSYST.2017.2713881
Xiong J, Cheng L W, Ma D T, et al. Destination-aided cooperative jamming for dual-hop amplify-and-forward MIMO untrusted relay systems. IEEE Trans Veh Tech, 2016, 65: 7274–7284
Cheng L W, Li W, Ma D T, et al. Moving window scheme for extracting secret keys in stationary environments. IET Commun, 2016, 10: 2206–2214
Ji X S, Yang Y, Huang K Z, et al. Physical layer authentication scheme based on hash method. J Electron Inf Technol, 2016, 38: 2900–2907
Alam M, Yang D, Rodriguez J, et al. Secure device-to-device communication in LTE-A. IEEE Commun Mag, 2014, 52: 66–73
Zhu D H, Swindlehurst A L, Fakoorian S A A, et al. Device-to-device communications: the physical layer security advantage. In: Proceedings of IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), Florence, 2014. 1606–1610
Kang X L, Ji X S, Huang K Z. Secure D2D underlaying cellular communication based on artificial noise assisted. J Commun, 2015, 36: 149–156
Kang X L, Ji X S, Huang K Z, et al. Secure D2D communication underlaying cellular networks: artificial noise assisted. In: Proceedings of IEEE International Conference on Vehicular Technology (VTC), Montreal, 2016
Chen Y J, Ji X S, Huang K Z, et al. Secrecy-outage-probability-based access strategy for device-to-device communications underlaying cellular networks. J Commun, 2016, 37: 86–94
Yue J T, Ma C, Yu H, et al. Secrecy-based channel assignment for device-to-device communication: an auction approach. In: Proceedings of IEEE International Conference on Wireless Communications and Signal Processing (WCSP), Hangzhou, 2013. 1–6
Chu Z, Cumanan K, Xu M, et al. Robust secrecy rate optimizations for multiuser multiple-input-single-output channel with device-to-device communications. IET Commun, 2015, 9: 396–403
Zhang H, Wang T Y, Song L Y, et al. Radio resource allocation for physical-layer security in D2D underlay communications. In: Proceedings of IEEE International Conference on Communications (ICC), Sydney, 2014. 2319–2324
Sun L, Du Q H, Ren P Y, et al. Two birds with one stone: towards secure and interference-free D2D transmissions via constellation rotation. IEEE Trans Veh Tech, 2016, 65: 8767–8774
Li W, Wu H Q, Song M, et al. Secrecy-oriented resource sharing for cellular device-to-device underlay. In: Proceedings of IEEE International Conference on Global Communications Conference (GLOBECOM), San Diego, 2015. 1–5
Zhang R Q, Cheng X, Yang L Q. Cooperation via spectrum sharing for physical layer security in device-to-device communications underlaying cellular networks. IEEE Trans Wirel Commun, 2016, 15: 5651–5663
Ma C, Liu J Q, Tian X H, et al. Interference exploitation in D2D-enabled cellular networks: a secrecy perspective. IEEE Trans Commun, 2015, 63: 229–242
Xu X M, He B, Yang W W, et al. Secure transmission design for cognitive radio networks with poisson distributed eavesdroppers. IEEE Trans Inf Foren Secur, 2016, 11: 373–387
Wang C, Wang H M, Xia X G. Uncoordinated jammer selection for securing SIMOME wiretap channels: a stochastic geometry approach. IEEE Trans Wirel Commun, 2015, 14: 2596–2612
Stoyan D, Kendall W S, Mecke J. Stochastic Geometry and Its Applications. 2nd ed. Hoboken: Wiley, 1996
Wang C, Wang H M. Opportunistic jamming for enhancing security: stochastic geometry modeling and analysis. IEEE Trans Veh Tech, 2016, 14: 2596–2612
Zhou X Y, Ganti R, Andrews J, et al. Physical layer security in cellular networks: a stochastic geometry approach. IEEE Trans Wirel Commun, 2013, 12: 2776–2787
Haenggi M, Ganti R K. Interference in large wireless networks. Found Trends Netw, 2008, 3: 127–248
Haenggi M. On distances in uniformly random networks. IEEE Trans Inf Theory, 2005, 51: 3584–3586
Acknowledgements
This work was supported in part by National High Technology Research and Development Program of China (863) (Grant No. SS2015AA011306), Open Research Fund of National Mobile Communications Research Laboratory, Southeast University (Grant No. 2013D09) and National Natural Science Foundation of China (Grant Nos. 61379006, 61521003, 61401510).
Author information
Authors and Affiliations
Corresponding author
Additional information
Conflict of interest The authors declare that they have no conflict of interest.
Rights and permissions
About this article
Cite this article
Chen, Y., Ji, X., Huang, K. et al. Opportunistic access control for enhancing security in D2D-enabled cellular networks. Sci. China Inf. Sci. 61, 042304 (2018). https://doi.org/10.1007/s11432-017-9160-y
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11432-017-9160-y