Abstract
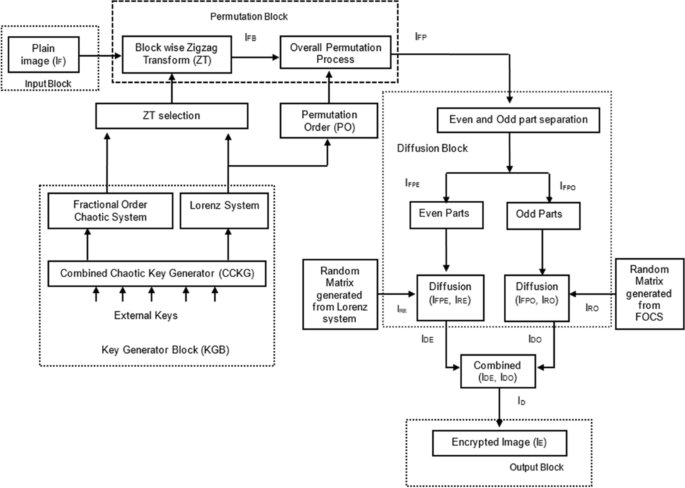
Medical images of patients must be securely transmitted and kept private in telemedicine. To secure such medical images, this paper proposes a single round chaotic image encryption scheme based on a permutation-diffusion structure. A combined chaotic key generator (CCKG) is proposed to enhance key sensitivity and generation in order to improve the security of medical images to be encrypted. CCKG is used to produce the initial seeds for the fractional order chaotic system (FOCS) and Lorenz system (LS) for the permutation and diffusion processes, respectively. CCKG together with proposed permutation and diffusion methods enhances cipher image security in single round. Using zigzag transform (ZT) scanning, the plain image is first permuted block by block. The type of scanning used on each block is heavily influenced by the ZT selection from FOCS and LS. Following block-wise permutation, the permutation order (PO) generated from LS performs overall permutation. Based on the pixel positions, the overall permuted image is divided into odd and even parts. Then these parts of the images are diffused separately by the random pixel matrices generated by LS and FOCS. The cipher image is formed by combining the odd and even parts after diffusion. Secret key analysis, statistical analysis, differential attack analysis, and simulations confirm that with a single round of image encryption, the proposed system is competent, robust and effective.
Graphical abstract



















Similar content being viewed by others
References
Priyanka, Maheshkar S (2017) Region-based hybrid medical image watermarking for secure telemedicine applications. Multimedia Tools Appl 76:36173647. https://doi.org/10.1007/s11042-016-3913-1
Garrity M (2019) “Malware attacks from within hospital, exposes need to encrypt medical imaging”, cyber security, Becker’s Healthcare, https://www.beckershospitalreview.com/cybersecurity/hospital-malware-attacks-from-within-exposes-need-to-encrypt-medical-imaging.html
Kumar Patro KA, Acharya B (2019) An efficient colour image encryption scheme based on 1-D chaotic maps. J Inf Secur Appl 46:23–41. https://doi.org/10.1016/j.jisa.2019.02.006
Kumar S, Panna B, Jha RK (2019) Medical image encryption using fractional discrete cosine transform with chaotic function. Med Biol Eng Comput 57:2517–2533. https://doi.org/10.1007/s11517-019-02037-3
Lima VS, Madeiro F, Lima JB (2020) Encryption of 3D medical images based on a novel multiparameter cosine number transform. Comput Biol Med 121:103772. https://doi.org/10.1016/j.compbiomed.2020.103772
Gopalakrishnan T, Ramakrishnan S (2019) Image encryption using hyper-chaotic map for permutation and diffusion by multiple hyper-chaotic maps. Wireless Pers Commun 109:437–454. https://doi.org/10.1007/s11277-019-06573-x
Madhusudhan KN, Sakthivel P (2021) A secure medical image transmission algorithm based on binary bits and Arnold map. J Ambient Intell Human Comput 12:5413–5420. https://doi.org/10.1007/s12652-020-02028-5
Ping P, Xu F, Mao Y, Wang Z (2018) Designing permutation–substitution image encryption networks with Henon map. Neurocomputing 283:53–63. https://doi.org/10.1016/j.neucom.2017.12.048
Xu L, Gou X, Li Z, Li J (2017) A novel chaotic image encryption algorithm using block scrambling and dynamic index based diffusion. Opt Lasers Eng 91:41–52. https://doi.org/10.1016/j.optlaseng.2016.10.012
Li Y, Wang C, Chen H (2017) A hyper-chaos-based image encryption algorithm using pixel-level permutation and bit-level permutation. Opt Lasers Eng 90:238–246. https://doi.org/10.1016/j.optlaseng.2016.10.020
Chai X, Chen Y, Broyde L (2017) A novel chaos-based image encryption algorithm using DNA sequence operations. Opt Lasers Eng 88:197–213. https://doi.org/10.1016/j.optlaseng.2016.08.009
Stallings W (2010) Cryptography and network security: principles and practice, 5th edn. Prentice Hall Press
Lian S, Sun J, Wang Z (2005) A block cipher based on a suitable use of the chaotic standard map. Chaos, Solitons Fractals 26(1):117–129. https://doi.org/10.1016/j.chaos.2004.11.096
Pareek NK, Patidar V, Sud KK (2006) Image encryption using chaotic logistic map. Image Vis Comput 24(9):926–934. https://doi.org/10.1016/j.imavis.2006.02.021
Kwok HS, Tang WKS (2007) A fast image encryption system based on chaotic maps with finite precision representation. Chaos, Solitons Fractals 32(4):1518–1529. https://doi.org/10.1016/j.chaos.2005.11.090
Wong K-W, Kwok BS-H, Law W-S (2008) A fast image encryption scheme based on chaotic standard map. Phys Lett A 372(15):2645–2652. https://doi.org/10.1016/j.physleta.2007.12.026
Wang Y, Wong K-W, Liao X, Xiang T, Chen G (2009) A chaos-based image encryption algorithm with variable control parameters. Chaos, Solitons Fractals 41(4):1773–1783. https://doi.org/10.1016/j.chaos.2008.07.031
Wong K-W, Kwok BS-H, Yuen C-H (2009) An efficient diffusion approach for chaos-based image encryption. Chaos, Solitons Fractals 41(5):2652–2663. https://doi.org/10.1016/j.chaos.2008.09.047
Patidar V, Pareek NK, Sud KK (2009) A new substitution–diffusion based image cipher using chaotic standard and logistic maps. Commun Nonlinear Sci Numer Simul 14(7):3056–3075. https://doi.org/10.1016/j.cnsns.2008.11.005
Rhouma R, Solak E, Belghith S (2010) Cryptanalysis of a new substitution–diffusion based image cipher. Commun Nonlinear Sci Numer Simul 15(7):1887–1892. https://doi.org/10.1016/j.cnsns.2009.07.007
Ye R (2011) A novel chaos-based image encryption scheme with an efficient permutation-diffusion mechanism. Optics Communications 284(22):5290–5298. https://doi.org/10.1016/j.optcom.2011.07.070
Zhang G, Liu Q (2011) A novel image encryption method based on total shuffling scheme. Optics Communications 284(12):2775–2780. https://doi.org/10.1016/j.optcom.2011.02.039
Wang X, He G (2011) Cryptanalysis on a novel image encryption method based on total shuffling scheme. Optics Communications 284(24):5804–5807. https://doi.org/10.1016/j.optcom.2011.08.053
Eslami Z, Bakhshandeh A (2013) An improvement over an image encryption method based on total shuffling. Optics Communications 286:51–55. https://doi.org/10.1016/j.optcom.2012.07.052
Zhu C (2012) A novel image encryption scheme based on improved hyperchaotic sequences. Optics Communications 285(1):29–37. https://doi.org/10.1016/j.optcom.2011.08.079
Wang X, Zhao J, Liu H (2012) A new image encryption algorithm based on chaos. Optics Communications 285(5):562–566. https://doi.org/10.1016/j.optcom.2011.10.098
Zhu H, Zhao C, Zhang X, Yang L (2014) An image encryption scheme using generalized Arnold map and affine cipher. Optik - Int J Light Electron Opt 125(22):6672–6677. https://doi.org/10.1016/j.ijleo.2014.06.149
Jeng F-G, Huang W-L, Chen T-H (2015) Cryptanalysis and improvement of two hyper-chaos-based image encryption schemes. Signal Process: Image Commun 34:45–51. https://doi.org/10.1016/j.image.2015.03.003
Gao T, Chen Z (2008) A new image encryption algorithm based on hyper-chaos. Phys Lett A 372(4):394–400. https://doi.org/10.1016/j.physleta.2007.07.04
Rhouma R, Belghith S (2008) Cryptanalysis of a new image encryption algorithm based on hyper-chaos. Phys Lett A 372(38):5973–5978. https://doi.org/10.1016/j.physleta.2008.07.05
Belazi A, Abd El-Latif AA, Belghith S (2016) A novel image encryption scheme based on substitution-permutation network and chaos. Signal Process 128:155–170. https://doi.org/10.1016/j.sigpro.2016.03.021
Gopalakrishnan T, Ramakrishnan S (2016) Chaotic image encryption with hash keying as key generator. IETE J Res 63(2):172–187. https://doi.org/10.1080/03772063.2016.1251855
Banu SA, Amirtharajan R (2020) A robust medical image encryption in dual domain: chaos-DNA-IWT combined approach. Med Biol Eng Comput 58:1445–1458. https://doi.org/10.1007/s11517-020-02178-w
Ravichandran D, Banu SA, Murthy B et al (2021) An efficient medical image encryption using hybrid DNA computing and chaos in transform domain. Med Biol Eng Comput 59:589–605. https://doi.org/10.1007/s11517-021-02328-8
Liu L, Miao S (2016) A new image encryption algorithm based on logistic chaotic map with varying parameter. SpringerPlus 5:289. https://doi.org/10.1186/s40064-016-1959-1
Ge M, Ye R (2018) A novel image encryption scheme based on 3D bit matrix and chaotic map with Markov properties. Egypt Inform J. https://doi.org/10.1016/j.eij.2018.10.001
Chu YD, Li XF, Zhang JG, Chang YX (2007) Computer simulation and circuit implementation for a new autonomous chaotic system. J Sichuan Univ 44(3):550–556
Ranjith Kumar R, Jayasudha S, Pradeep S (2016) Efficient and secure data hiding in encrypted images: a new approach using chaos. Inf Secur J: A Global Perspect 25(4–6):235–246. https://doi.org/10.1080/19393555.2016.1248582
Alzheimer’s Disease Neuroimaging Initiative (ADNI) Dataset: https://ida.loni.usc.edu/home/projectPage.jsp?project=ADNI
Cheng J, Huang W, Cao S, Yang R, Yang W, Yun Z et al (2015) brainTumorDataPublic_1-766.zip. figshare. Dataset. https://doi.org/10.6084/m9.figshare.1512409.v1
Lindner L, Kolodziej M, Egger J (2018) Skull-stripped contrast-enhanced MRI datasets. figshare. Dataset. https://doi.org/10.6084/m9.figshare.7472168.v1
François M, Grosges T, Barchiesi D, Erra R (2012) A new image encryption scheme based on a chaotic function. Signal Processing: Image Communication, Elsevier 27(3):249–259
Yin Q, Wang C (2018) A new chaotic image encryption scheme using breadth-first search and dynamic diffusion. Int J Bifurcation Chaos 28(04):1850047. https://doi.org/10.1142/s0218127418500475
Pareek NK, Patidar V, Sud KK (2013) Diffusion–substitution based gray image encryption scheme. Digital Signal Processing 23(3):894–901. https://doi.org/10.1016/j.dsp.2013.01.005
Norouzi B, Mirzakuchaki S, Seyedzadeh SM, Mosavi MR (2012) A simple, sensitive and secure image encryption algorithm based on hyper-chaotic system with only one round diffusion process. Multimed Tools Appl 71(3):1469–1497. https://doi.org/10.1007/s11042-012-1292-9
Etemadi Borujeni S, Eshghi M (2011) Chaotic image encryption system using phase-magnitude transformation and pixel substitution. Telecommun Syst. https://doi.org/10.1007/s11235-011-9458-8
Masood F, Ahmad J, Shah SA, Jamal SS, Hussain I (2020) A novel hybrid secure image encryption based on Julia set of fractals and 3D Lorenz chaotic map. Entropy 22(3):274. https://doi.org/10.3390/e22030274
Ranjith Kumar R, Balakumar M (2014) A new chaotic image encryption using parametric switching based permutation and diffusion. ICTACT j image video process 14(04):795–804. https://doi.org/10.21917/ijivp.2014.0114
Fu C, Zhang G, Bian O, Lei W, Ma H (2014) A Novel medical image protection scheme using a 3-dimensional chaotic system. PLoS ONE 9(12):e115773. https://doi.org/10.1371/journal.pone.0115773
Hua Z, Zhou B, Zhou Y (2018) Sine-transform-based chaotic system with FPGA implementation. IEEE Trans Industr Electron 65(3):2557–2566
Xingyuan W, Junjian Z, Guanghui C (2019) An image encryption algorithm based on zigzag transform and LL compound chaotic system. Opt Laser Technol 119:105581. https://doi.org/10.1016/j.optlastec.2019.105581
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Kumar D, Sudha V K & Ranjithkumar R A one-round medical image encryption algorithm based on a combined chaotic key generator. Med Biol Eng Comput 61, 205–227 (2023). https://doi.org/10.1007/s11517-022-02703-z
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11517-022-02703-z




