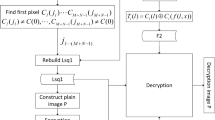
Abstract
Recently, a new secure image encryption scheme was proposed based on a novel 2D sine–cosine cross‑chaotic map. The authors claimed that the encryption scheme they proposed was secure enough to resist all the existing cryptanalytic attacks. However, the multi-round original cryptosystem with permutation–bit diffusion structure (PBDS) was found to have three security vulnerabilities and was proved to be equivalent to the one-round cryptosystem with PBDS, which would lead to the original cryptosystem being successfully cracked by chosen-plaintext attack (CPA). Subsequently, two efficient and feasible attack schemes were proposed in this paper, and they require \(\left\lceil {\log_{2} W \times H} \right\rceil + 1\) and \(\left\lceil {\log_{256} W \times H} \right\rceil + 1\) times of CPA in total, respectively. Simulation and experimental results have verified the effectiveness and feasibility of the two attack schemes.








Similar content being viewed by others
References
Kazuma, K.: Artificial intelligence technology and medical image processing. No Shinkei Geka. Neurol. Surg. 48(7), 654–664 (2020)
Li, Z.Y.: Application research of digital image technology in graphic design. J. Vis. Commun. Image Represent. 65 (2019)
Zhang, Y.S., Huang, H., Xiang, Y., Zhang, L.Y., He, X.: Harnessing the hybrid cloud for secure big image data service. IEEE Internet Things J. 4(5), 1380–1388 (2017)
Evsutin, O., Melman, A., Meshcheryakov, R.: Digital steganography and watermarking for digital images: a review of current research directions. IEEE Access. 8, 166589–166611 (2020)
Zhang, Y.S., He, Q., Xiang, Y., Zhang, L.Y., Liu, B., Chen, J.X., Xie, Y.Y.: Low-cost and confidentiality-preserving data acquisition for internet of multimedia things. IEEE Internet Things J. 5(5), 3442–3451 (2018)
Yuan, G.H., Hao, Q.: Digital watermarking secure scheme for remote sensing image protection. Chin Commun. 17(4), 88–98 (2020)
Roy, S.S., Basu, A., Chattopadhyay, A.: On the implementation of a copyright protection scheme using digital image watermarking. Multimed. Tools Appl. 79(19–20), 13125–13138 (2020)
Zhang, Y.S., Wang, P., Fang, L.M., He, X., Han, H., Chen, B.: Secure transmission of compressed sampling data using edge clouds. IEEE Trans. Ind. Inf. 16(10), 6641–6651 (2020)
Xue, F., Lu, W., Ren, H.L., Xiao, H.M., Zhang, Q., Liu, X.J.: Forensics of visual privacy protection in digital images. Multimed. Tools Appl. 79(17–18), 12427–12445 (2020)
Luo, Y.J., Qin, J.H., Xiang, X.Y., Tan, Y., Liu, Q., Xiang, L.Y.: Coverless real-time image information hiding based on image block matching and dense convolutional network. J. Real-Time Image Process. 17(3), 125–135 (2019)
Zhang, J.M., Sun, J., Wang, J., Yue, X.G.: Visual object tracking based on residual network and cascaded correlation filters. J. Ambient Intell. Humaniz, Comput (2020)
Zhang, J.M., Xie, Z.P., Sun, J., Zou, X., Wang, J.: A cascaded R-CNN with multiscale attention and imbalanced samples for traffic sign detection. IEEE Access. 8, 29742–29754 (2020)
Zhang, J.M., Jin, X.K., Sun, J., Wang, J., Li, K.Q.: Dual model learning combined with multiple feature selection for accurate visual tracking. IEEE Access. 7, 43956–43969 (2019)
Daudigny, R., Ledig, H., Muller, F., Valette, F.: SCARE of the DES - (Side channel analysis for reverse engineering of the data encryption standard). Appl. Cryptogr. Netw. Secur. Proc. 3531, 393–406 (2005)
Yap, W.S., Phan, R.C.W., Goi, B.M.: Cryptanalysis of a high-definition image encryption based on AES modification. Wirel. Pers. Commun. 88(3), 685–699 (2016)
Bunder, M., Nitaj, A., Susilo, W., Tonien, J.: Cryptanalysis of RSA-type cryptosystems based on Lucas sequences, Gaussian integers and elliptic curves. J. Inf. Secur. Appl. 40, 193–198 (2018)
Zhang, Y.S., Xiao, D.: An image encryption scheme based on rotation matrix bit-level permutation and block diffusion. Commun. Nonlinear Sci. Numer. Simul. 19(1), 74–82 (2014)
Ye, R.S.: A novel chaos-based image encryption scheme with an efficient permutation-diffusion mechanism. Opt. Commun. 284(22), 5290–5298 (2011)
Chen, J.X., Zhu, Z.L., Zhang, L.B., Zhang, Y.S., Yang, B.Q.: Exploiting self-adaptive permutation-diffusion and DNA random encoding for secure and efficient image encryption. Signal Process. 142, 340–353 (2018)
Enayatifar, R., Abdullah, A.H., Isnin, I.F., Altameem, A., Lee, M.: Image encryption using a synchronous permutation-diffusion technique. Opt. Lasers Eng. 90, 146–154 (2017)
Zhang, Y.S., Xiao, D.: Self-adaptive permutation and combined global diffusion for chaotic color image encryption. AEU-Int. J. Electron. Commun. 68(4), 361–168 (2014)
Wang, M.X., Wang, X.Y., Zhang, Y.Q., Zhou, S., Zhao, T.T., Yao, N.M.: A novel chaotic system and its application in a color image cryptosystem. Opt. Lasers Eng. 121, 479–494 (2019)
Diab, H.: An efficient chaotic image cryptosystem based on simultaneous permutation and diffusion operations. IEEE Access. 6, 42227–42244 (2018)
Diab, H., El-Semary, A.M.: Secure image cryptosystem with unique key streams via hyper-chaotic system. Signal Process. 142, 53–68 (2018)
Patro, K.A.K., Acharya, B.: An efficient colour image encryption scheme based on 1-D chaotic maps. J. Inf. Secur. Appl. 46, 23–41 (2019)
Chai, X.L., Fu, X.L., Gan, Z.H., Zhang, Y.S., Lu, Y., Chen, Y.R.: An efficient chaos-based image compression and encryption scheme using block compressive sensing and elementary cellular automata. Neural Comput. Appl. 32(9), 4961–4988 (2020)
Ali, T.S., Ali, R.: A new chaos based color image encryption algorithm using permutation substitution and Boolean operation. Multimed. Tools Appl. 79(27–28), 19853–19873 (2020)
Fridrich, J.: Symmetric ciphers based on two-dimensional chaotic maps. Int. J. Bifurcation Chaos 8(6), 1259–1284 (1998)
Pak, C., An, K., Jang, P.: A novel bit-level color image encryption using improved 1D chaotic map. Multimed. Tools Appl. 78(9), 12027–12042 (2019)
Zhou, Y.C., Bao, L., Chen, C.L.P.: A new 1D chaotic system for image encryption. Signal Process. 97, 172–182 (2014)
Pak, C., Huang, L.L.: A new color image encryption using combination of the 1D chaotic map. Signal Process. 138, 129–137 (2017)
Mondal, B., Kumar, P., Singh, S.: A chaotic permutation and diffusion based image encryption algorithm for secure communications. Multimed. Tools Appl. 77(23), 31177–31198 (2018)
Wu, J.H., Liao, X.F., Yang, B.: Image encryption using 2D Henon-Sine map and DNA approach. Signal Process. 153, 11–23 (2018)
Li, M., Wang, P.C., Liu, Y.F., Fan, H.J.: Cryptanalysis of a novel bit-level color image encryption using improved 1D chaotic map. IEEE Access. 7, 145798–145806 (2019)
Dhall, S., Pal, S.K., Sharma, K.: Cryptanalysis of image encryption scheme based on a new 1D chaotic system. Signal Process. 146, 22–32 (2018)
Dou, Y.Q., Li, M.: Cryptanalysis of a New Color Image Encryption Using Combination of the 1D Chaotic Map. Appl. Sci.-Basel. 10(6) (2020)
Li, M., Zhou, K.L., Ren, H., Fan, H.J.: Cryptanalysis of permutation-diffusion-based lightweight chaotic image encryption scheme using CPA. Appl. Sci.-Basel. 9(3) (2019)
Chen, J.X., Chen, L., Zhou, Y.C.: Cryptanalysis of a DNA-based image encryption scheme. Inf. Sci. 520, 130–141 (2020)
Norouzi, B., Seyedzadeh, S.M., Mirzakuchaki, S., Mosavi, M.R.: A novel image encryption based on hash function with only two-round diffusion process. Multimedia Syst. 20(1), 45–64 (2014)
Hu, G.Q., Xiao, D., Wang, Y., Li, X.Y.: Cryptanalysis of a chaotic image cipher using Latin square-based confusion and diffusion. Nonlinear Dyn. 88(2), 1305–1316 (2017)
Li, M., Lu, D.D., Xiang, Y., Zhang, Y.S., Ren, H.: Cryptanalysis and improvement in a chaotic image cipher using two-round permutation and diffusion. Nonlinear Dyn. 96(1), 31–47 (2019)
Mondal, B., Behera, P.K., Gangopadhyay, S.: A secure image encryption scheme based on a novel 2D sine-cosine cross-chaotic (SC3) map. J. Real-Time Image Process (2020)
Wu, Y., Yang, G.L., Jin, H.X., Noonan, J.P.: Image encryption using the two-dimensional logistic chaotic map. J. Electron. Imaging. 21(1) (2012)
Hua, Z.Y., Zhou, Y.C., Pun, C.M., Chen, C.L.P.: 2D Sine Logistic modulation map for image encryption. Inf. Sci. 297, 80–94 (2015)
Ping, P., Xu, F., Mao, Y.C., Wang, Z.J.: Designing permutation-substitution image encryption networks with henon map. Neurocomputing 283, 53–63 (2018)
Hua, Z.Y., Zhou, Y.C.: Image encryption using 2D logistic-adjusted-sine map. Inf. Sci. 339, 237–253 (2016)
Kerckhoffs, A.: La cryptographie militaire. J. des Sci. Militaires. 9, 161–191 (1883)
Acknowledgements
The authors are grateful for the constructive comments and suggestions from the editor of the journal and the anonymous reviewers on an earlier version of the paper.
Funding
This work was supported by the Science and Technology Research Project of Henan Province (212102210413), the PhD Scientific Research Foundation of Henan Normal University (5101119170143), the Science Foundation for Young Scholars of Henan Normal University (2015QK25), and the National Natural Science Foundation of China (61602158).
Author information
Authors and Affiliations
Corresponding authors
Ethics declarations
Conflict of interest
The authors have no conflicts of interest to declare that are relevant to the content of this article.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Li, M., Wang, P., Yue, Y. et al. Cryptanalysis of a secure image encryption scheme based on a novel 2D sine–cosine cross‑chaotic map. J Real-Time Image Proc 18, 2135–2149 (2021). https://doi.org/10.1007/s11554-021-01091-1
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11554-021-01091-1