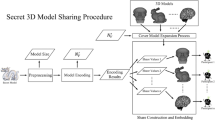
Abstract
Secret sharing can protect the security of important secret information in the network environment. However, the computational complexity and processing delay increase drastically when the secret information contains large amounts of data, such as three-dimensional (3D) data cubes. To improve the efficiency of secret sharing on 3D data cubes, this paper proposes a hardware architecture to accelerate the generation of shares and reconstruction of the secret. The proposed hardware architecture parallelizes the secret sharing process and optimizes on this basis to save large amounts of circuit resources. Simulation results show that this architecture performs secret sharing more than ten times faster than the software implementation. This study enables the secret sharing of 3D data cubes, which protect large amounts of data information throughout the process and allows complete reconstruction of 3D data cubes. To be able to handle secrets without decoding them, we then extend the hardware architecture to the four basic processes of multi-party computation, demonstrating the feasibility of the structure and providing preliminary research tools for the effective implementation of multi-party computation.


















Similar content being viewed by others
Data availability
The data used in this study are available from the corresponding author upon request.
References
Beimel, A., Chor, B.: Universally ideal secret-sharing schemes. IEEE Trans. Inf. Theory 40(3), 786–794 (1994)
Blakley, G.R.: Safeguarding cryptographic keys. In: International workshop on managing requirements knowledge, pp. 313–313. IEEE Computer Society (1979)
Blanton, M., Kang, A., Yuan, C.: Improved building blocks for secure multi-party computation based on secret sharing with honest majority. In: International Conference on Applied Cryptography and Network Security. Springer, pp. 377–397 (2020)
Chanu, O.B., Neelima, A.: A survey paper on secret image sharing schemes. Int. J. Multimed. Inf. Retriev. 8(4), 195–215 (2019). https://doi.org/10.1007/s13735-018-0161-3
Halpern, J., Teague, V.: Rational secret sharing and multiparty computation. In: Proceedings of the Thirty-Sixth Annual ACM Symposium on Theory of Computing, pp. 623–632 (2004)
Han, J., Susilo, W., Mu, Y., Yan, J.: Attribute-based oblivious access control. Comput. J. 55(10), 1202–1215 (2012). https://doi.org/10.1093/comjnl/bxs061
Hanaoka, G., Nishioka, T., Zheng, Y., Imai, H.: A hierarchical non-interactive key-sharing scheme with low memory size and high resistance against collusion attacks. Comput. J. 45(3), 293–303 (2002). https://doi.org/10.1093/comjnl/45.3.293
Hansen, J.P.: Secret sharing schemes with strong multiplication and a large number of players from toric varieties. Contemp. Math. 686, 171–185 (2017). https://doi.org/10.1090/conm/686/13783
Iftene, S.: General secret sharing based on the Chinese remainder theorem with applications in e-voting. Electro. Notes Theor. Comput. Sci. 186, 67–84 (2007). https://doi.org/10.1016/j.entcs.2007.01.065
Kabirirad, S., Eslami, Z.: Improvement of \((n, n)\)-multi-secret image sharing schemes based on Boolean operations. J. Inf. Secur. Appl. 47, 16–27 (2019). https://doi.org/10.1016/j.jisa.2019.03.018
Kumar, S.: Extending boolean operations-based secret image sharing to compartmented access structure. Multimed. Tools Appl. (2022). https://doi.org/10.1007/s11042-021-11554-z
Liu, J., Wu, Y., Liu, X., Zhang, Y., Xue, G., Zhou, W., Yao, S.: On the (in) security of recent group key distribution protocols. Comput. J. 60(4), 507–526 (2017). https://doi.org/10.1093/comjnl/bxw061
Liu, T., Yan, B., Pan, J.S.: Color visual secret sharing for QR code with perfect module reconstruction. Appl. Sci. (2019). https://doi.org/10.3390/app9214670
McEliece, R.J., Sarwate, D.V.: On sharing secrets and Reed-Solomon codes. Commun. ACM 24(9), 583–584 (1981). https://doi.org/10.1145/358746.358762
Pan, J.S., Sun, X.X., Chu, S.C., Abraham, A., Yan, B.: Digital watermarking with improved SMS applied for QR code. Eng. Appl. Artif. Intell. 97, 104049 (2021). https://doi.org/10.1016/j.engappai.2020.104049
Pan, J.S., Liu, T., Yang, H.M., Yan, B., Chu, S.C., Zhu, T.: Visual cryptography scheme for secret color images with color QR codes. J. Vis. Commun. Image Represent. 82, 103405 (2022)
Patel, R., Wolfe, P.F., Munafo, R., Varia, M., Herbordt, M.: Arithmetic and Boolean secret sharing MPC on FPGAs in the data center. In: 2020 IEEE High Performance Extreme Computing Conference (HPEC), pp. 1–8. IEEE (2020)
Pilaram, H., Eghlidos, T., Toluee, R.: An efficient lattice-based threshold signature scheme using multi-stage secret sharing. IET Inf. Secur. 15(1), 98–106 (2021). https://doi.org/10.1049/ise2.12007
Prasetyo, H., Simatupang, J.W.: XOR-ed based friendly-progressive secret sharing. In: 2019 International Symposium on Intelligent Signal Processing and Communication Systems (ISPACS), pp. 1–2. IEEE (2019)
Qin, C., Jiang, C., Mo, Q., Yao, H., Chang, C.C.: Reversible data hiding in encrypted image via secret sharing based on GF (p) and GF (\(2^{8}\)). IEEE Trans. Circ. Syst. Video Technol. 32(4), 1928–1941 (2021). https://doi.org/10.1109/TCSVT.2021.3091319
Rolf, O.: Contemporary cryptography. Ph.D. thesis, Artech House, Inc. (2011)
Shamir, A.: How to share a secret. Commun. ACM 22(11), 612–613 (1979). https://doi.org/10.1145/359168.359176
Stangl, J., Lorünser, T., Dinakarrao, S.M.P.: A fast and resource efficient FPGA implementation of secret sharing for storage applications. In: 2018 Design, Automation & Test in Europe Conference & Exhibition (DATE), pp. 654–659. IEEE (2018)
Thien, C.C., Lin, J.C.: Secret image sharing. Comput. Graph. 26(5), 765–770 (2002). https://doi.org/10.1016/S0097-8493(02)00131-0
Wang, R.Z., Su, C.H.: Secret image sharing with smaller shadow images. Pattern Recogn. Lett. 27(6), 551–555 (2006). https://doi.org/10.1016/j.patrec.2005.09.021
Wang, F., Chang, C.C., Harn, L.: Simulatable and secure certificate-based threshold signature without pairings. Secur. Commun. Netw. 7(11), 2094–2103 (2014). https://doi.org/10.1002/SEC.921
Xing, F., Yan, X., Yu, L., Sun, Y.: Information hiding in the sharing domain. J. Vis. Commun. Image Represent. 86, 103520 (2022). https://doi.org/10.1016/j.jvcir.2022.103520
Xiong, L., Han, X., Yang, C.N.: CP-PSIS: CRT and polynomial-based progressive secret image sharing. Signal Process. 185, 108064 (2021). https://doi.org/10.1016/j.sigpro.2021.108064
Acknowledgements
This work was funded by the Shandong Provincial Natural Science Foundation (No. ZR2021MF050), the Ministry of Education in China (MOE) Project of Humanities and Social Sciences (Project No. 18YJAZH110), and the National Statistics Science Project (2021LY082).
Author information
Authors and Affiliations
Contributions
All authors contributed to the study conception and design. Material preparation, data collection and analysis were performed by TL, BY, J-SP and H-MY. The first draft of the manuscript was written by Z-MW and all authors commented on previous versions of the manuscript. All authors read and approved the final manuscript.
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no competing interests.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Wu, ZM., Liu, T., Yan, B. et al. FPGA acceleration of secret sharing for 3D data cubes. J Real-Time Image Proc 20, 82 (2023). https://doi.org/10.1007/s11554-023-01337-0
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11554-023-01337-0