Abstract
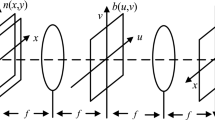
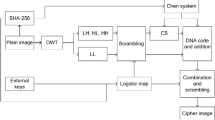
Based on compressive sensing and fractional discrete cosine transform (DCT) via polynomial interpolation (PI-FrDCT), an image encryption algorithm is proposed, in which the compression and encryption of an image are accomplished simultaneously. It can keep information secret more effectively with low data transmission. Three-dimensional piecewise and nonlinear chaotic maps are employed to obtain a generating sequence and the exclusive OR (XOR) matrix, which greatly enlarge the key space of the encryption system. Unlike many other fractional transforms, the output of PI-FrDCT is real, which facilitates the storage, transmission and display of the encrypted image. Due to the introduction of a plain-image-dependent disturbance factor, the initial values and system parameters of the encryption scheme are determined by cipher keys and plain-image. Thus, the proposed encryption scheme is very sensitive to the plain-image, which makes the encryption system more secure. Experimental results demonstrate the validity and the reliability of the proposed encryption algorithm.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.References
G. H. Situ, J. J. Zhang. A cascaded iterative Fourier transform algorithm for optical security applications. Optik–International Journal for Light and Electron Optics, vol. 114, no. 10, pp. 473–477, 2003. DOI: 10.1078/0030-4026-00291.
X. G. Wang, D. M. Zhao. Multiple-image encryption based on nonlinear amplitude-truncation and phase-truncation in Fourier domain. Optics Communications, vol. 284, no. 1, pp. 148–152, 2011. DOI: 10.1016/j.optcom.2010.09.034.
M. H. Annaby, M. A. Rushdi, E. A. Nehary. Image encryption via discrete fractional Fourier-type transforms generated by random matrices. Signal Processing: Image Communication, vol. 49, pp. 25–46, 2016. DOI: 10.1016/j.image.2016.09.006.
L. S. Sui, K. K. Duan, J. L. Liang, Z. Q. Zhang, H. N. Meng. Asymmetric multiple-image encryption based on coupled logistic maps in fractional Fourier transform domain. Optics and Lasers in Engineering, vol. 62, pp. 139–152, 2014. DOI: 10.1016/j.optlaseng.2014.06.003.
L. S. Sui, M. J. Xu, A. L. Tian. Optical noise-free image encryption based on quick response code and high dimension chaotic system in gyrator transform domain. Optics and Lasers in Engineering, vol. 91, pp. 106–114, 2017. DOI: 10.1016/j.optlaseng.2016.11.017.
Z. J. Liu, M. A. Ahmad, S. T. Liu. Image encryption based on double random amplitude coding in random Hartley transform domain. Optik–International Journal for Light and Electron Optics, vol. 121, no. 11, pp. 959–964, 2010. DOI: 10.1016/j.ijleo.2008.12.006.
S. M. Pan, R. H. Wen, Z. H. Zhou, N. R. Zhou. Optical multi-image encryption scheme based on discrete cosine transform and nonlinear fractional Mellin transform. Multimedia Tools and Applications, vol. 76, no. 2, pp. 2933–2953, 2017. DOI: 10.1007/s11042-015-3209-x.
N. R. Zhou, J. P. Yang, C. F. Tan, S. M. Pan, Z. H. Zhou. Double-image encryption scheme combining DWT-based compressive sensing with discrete fractional random transform. Optics Communications, vol. 354, pp. 112–121, 2015. DOI: 10.1016/j.optcom.2015.05.043.
G. Unnikrishnan, J. Joseph, K. Singh. Optical encryption by double-random phase encoding in the fractional Fourier domain. Optics Letters, vol. 25, no. 12, pp. 887–889, 2000. DOI: 10.1364/OL.25.000887.
R. Tao, J. Lang, Y. Wang. Optical image encryption based on the multiple-parameter fractional Fourier transform. Optics Letters, vol. 33, no. 6, pp. 581–583, 2008. DOI: 10.1364/OL.33.000581.
Y. P. Li, C. H. Wang, H. Chen. A hyper-chaos-based image encryption algorithm using pixel-level permutation and bit-level permutation. Optics and Lasers in Engineering, vol. 90, pp. 238–246, 2017. DOI: 10.1016/j.optlaseng. 2016.10.020.
Z. Parvin, H. Seyedarabi, M. Shamsi. A new secure and sensitive image encryption scheme based on new substitution with chaotic function. Multimedia Tools and Applications, vol. 75, no. 17, pp. 10631–10648, 2016. DOI: 10. 1007/s11042-014-2115-y.
R. Enayatifar, A. H. Abdullah, I. F. Isnin, A. Altameem, M. Lee. Image encryption using a synchronous permutation-diffusion technique. Optics and Laser Technology, vol. 90, pp. 146–154, 2017. DOI: 10.1016/j.optlaseng.2016. 10.006.
T. G. Gao, Z. Q. Chen. A new image encryption algorithm based on hyper-chaos. Physics Letters A, vol. 372, no. 4, pp. 394–400, 2008. DOI: 10.1016/j.physleta.2007.07.040.
W. Zhang, K. W. Wong, H. Yu, Z. L. Zhu. An image encryption scheme using reverse 2-dimensional chaotic map and dependent diffusion. Communications in Nonlinear Science and Numerical Simulation, vol. 18, no. 8, pp. 2066–2080, 2013. DOI: 10.1016/j.cnsns.2012.12.012.
I. Venturini, P. Duhamel. Reality preserving fractional transforms. In Proceedings of IEEE International Conference on Acoustics, Speech, and Signal Processing, Montreal, Canada, vol. 5, pp. 205–208, 2004.
J. Lang. Image encryption based on the reality-preserving multiple-parameter fractional Fourier transform. Optics Communications, vol. 285, no. 10–11, pp. 2584–2590, 2012. DOI: 10.1016/j.optcom.2012.01.085.
N. R. Zhou, Y. X. Wang, L. H. Gong, X. B. Chen, Y. X. Yang. Novel color image encryption algorithm based on the reality preserving fractional Mellin transform. Optics & Laser Technology, vol. 44, no. 7, pp. 2270–2281, 2012. DOI: 10.1016/j.optlastec.2012.02.027.
Z. J. Liu, Y. Zhang, H. F. Zhao, M. A. Ahmad, S. T. Liu. Optical multi-image encryption based on frequency shift. Optik–International Journal for Light and Electron Optics, vol. 122, no. 11, pp. 1010–1013, 2011. DOI: 10.1016/j. ijleo.2010.06.039.
E. J. Candès. Compressive sampling. In Proceedings of the International Congress of Mathematics, Madrid, Spain, pp. 1433–1452, 2006.
E. J. Candès, J. Romberg, T. Tao. Robust uncertainty principles: Exact signal reconstruction from highly incomplete frequency information. IEEE Transactions on Information Theory, vol. 52, no. 2, pp. 489–509, 2006. DOI: 10.1109/TIT.2005.862083.
D. L. Donoho. Compressed sensing. IEEE Transactions on Information Theory, vol. 52, no. 4, pp. 1289–1306, 2006. DOI: 10.1109/TIT.2006.871582.
R. Huang, K. Sakurai. A robust and compression-combined digital image encryption method based on compressive sensing. In Proceedings of the 7th International Conference on Intelligent Information Hiding and Multimedia Signal Processing, Dalian, China, pp. 105–108, 2011. DOI: 10.1109/IIHMSP.2011.53.
Y. Rachlin, D. Baron. The secrecy of compressed sensing measurements. In Proceedings of the 46th Annual Allerton Conference on Communication, Control, and Computing, Urbana, USA, pp. 813–817, 2008. DOI: 10.1109/ALLERTON.2008.4797641.
M. R. Mayiami, B. Seyfe, H. G. Bafghi. Perfect secrecy via compressed sensing. In Proceedings of Iran Workshop on Communication and Information Theory, Tehran, Iran, pp. 1–5, 2013. DOI: 10.1109/IWCIT.2013.6555751.
P. Lu, Z. Y. Xu, X. Lu, X. Y. Liu. Digital image information encryption based on compressive sensing and double random-phase encoding technique. Optik–International Journal for Light and Electron Optics, vol. 124, no. 16, pp. 2514–2518, 2013. DOI: 10.1016/j.ijleo.2012.08.017.
G. Q. Hu, D. Xiao, Y. Wang, T. Xiang. An image coding scheme using parallel compressive sensing for simultaneous compression-encryption applications. Journal of Visual Communication and Image Representation, vol. 44, pp. 116–127, 2017. DOI: 10.1016/j.jvcir.2017.01.022.
C. Feng, L. Xiao, Z. H. Wei. Compressive sensing inverse synthetic aperture radar imaging based on gini index regularization. International Journal of Automation and Computing, vol. 11, no. 4, pp. 441–448, 2014. DOI: 10.1007/s11633-014-0811-8.
E. J. Candès. The restricted isometry property and its implications for compressed sensing. Comptes Rendus Mathematique, vol. 346, no. 9–10, pp. 589–592, 2008. DOI: 10. 1016/j.crma.2008.03.014.
B. K. Natarajan. Sparse approximate solutions to linear systems. SIAM Journal on Computing, vol. 24, no. 2, pp. 227–234, 1995. DOI: 10.1137/S0097539792240406.
S. S. Chen, D. L. Donoho, M. A. Saunders. Atomic decomposition by basis pursuit. SIAM Journal on Scientific Computing, vol. 20, no. 1, pp. 33–61, 1998. DOI: 10.1137/S1064827596304010.
Y. Zhang, Y. Y. Wang, C. Zhang. Total variation based gradient descent algorithm for sparse-view photoacoustic image reconstruction. Ultrasonics, vol. 52, no. 8, pp. 1046–1055, 2012. DOI: 10.1016/j.ultras.2012.08.012.
S. G. Mallat, Z. F. Zhang. Matching pursuits with time-frequency dictionaries. IEEE Transactions on Signal Processing, vol. 41, no. 12, pp. 3397–3415, 1993. DOI: 10.1109/78.258082.
E. T. Liu, V. N. Temlyakov. The orthogonal super greedy algorithm and applications in compressed sensing. IEEE Transactions on Information Theory, vol. 58, no. 4, pp. 2040–2047, 2012. DOI: 10.1109/TIT.2011.2177632.
H. Mohimani, M. Babaie-Zadeh, C. Jutten. A fast approach for overcomplete sparse decomposition based on smoothed l0 norm. IEEE Transactions on Signal Processing, vol. 57, no. 1, pp. 289–301, 2009. DOI: 10.1109/TSP.2008.2007606.
G. Cariolaro, T. Erseghe, P. Kraniauskas. The fractional discrete cosine transform. IEEE Transactions on Signal Processing, vol. 50, no. 4, pp. 902–911, 2002. DOI: 10.1109/78.992138.
J. H. Wu, F. F. Guo, P. P. Zeng, N. R. Zhou. Image encryption based on a reality-preserving fractional discrete cosine transform and a chaos-based generating sequence. Journal of Modern Optics, vol. 60, no. 20, pp. 1760–1771, 2013. DOI: 10.1080/09500340.2013.858189.
Y. R. Liang, G. P. Liu, N. R. Zhou, J. H. Wu. Image encryption combining multiple generating sequences controlled fractional DCT with dependent scrambling and diffusion. Journal of Modern Optics, vol. 62, no. 4, pp. 251–264, 2014. DOI: 10.1080/09500340.2014.964342.
Y. R. Liang, J. H. Wu. New image encryption combining fractional DCT via polynomial interpolation with dependent scrambling and diffusion. Journal of China Universities of Posts and Telecommunications, vol. 22, no. 5, pp. 1–9, 2015. DOI: 10.1016/S1005-8885(15)60673-2.
A. Akhshani, S. Behnia, A. Akhavan, H. Abu Hassan, Z. Hassan. A novel scheme for image encryption based on 2D piecewise chaotic maps. Optics Communications, vol. 283, no. 17, pp. 3259–3266, 2010. DOI: 10.1016/j.optcom.2010. 04.056.
N. R. Zhou, A. D. Zhang, J. H. Wu, D. J. Pei, Y. X. Yang. Novel hybrid image compression-encryption algorithm based on compressive sensing. Optik–International Journal for Light and Electron Optics, vol. 125, no. 18, pp. 5075–5080, 2014. DOI: 10.1016/j.ijleo.2014.06.054.
A. S. Arumugam, D. N. Krishnan. Biometric encryption and bio-fusion authentication using combined Arnold transition and permutation matrices. International Journal of Engineering Science and Technology, vol. 2, no. 10, pp. 5357–5369, 2010.
V. Patidar, N. K. Pareek, G. K. Purohit, K. K. Sud. A robust and secure chaotic standard map based pseudorandom permutation-substitution scheme for image encryption. Optics Communications, vol. 284, no. 19, pp. 4331–4339, 2011. DOI: 10.1016/j.optcom.2011.05.028.
Acknowledgements
This work was supported by National Natural Science Foundation of China (Nos. 61662047 and 61462061).
Author information
Authors and Affiliations
Corresponding author
Additional information
Recommended by Associate Editor Zhi-Jie Xu
Ya-Ru Liang received the B. Sc. degree in automation from Heilongjiang Institute of Technology, China in 2002, the M. Sc. degree in power electronics and power drives from Shenyang University of Technology, China in 2008, and the Ph. D. degree in mechanical engineering from Nanchang University, China in 2016. Currently, she is a lecturer in Department of Electronic Information Engineering, Jiangxi Agricultural University, China.
Her research interests include image processing, image encryption and information security.
Zhi-Yong Xiao received the B. Sc. degree in electronic information engineering from Nanchang Hangkong University, China in 2001, and the M. Sc. degree in control theory and engineering from East China University of Technology, China in 2008. He is a Ph. D. degree candidate in mechanical engineering at School of Mechatronic Engineering, Nanchang University, China.
His research interests include image processing, computer vision and pattern recognition.
Rights and permissions
About this article
Cite this article
Liang, YR., Xiao, ZY. Image Encryption Algorithm Based on Compressive Sensing and Fractional DCT via Polynomial Interpolation. Int. J. Autom. Comput. 17, 292–304 (2020). https://doi.org/10.1007/s11633-018-1159-2
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11633-018-1159-2