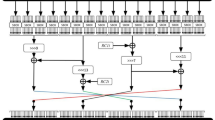
Abstract
This paper introduces the research progress of the State Key Laboratory of Information Security (SKLOIS) in China during 2002–2006. This introduction covers four selected areas with each covering some selected research findings. The four selected areas are: the fundamentals of cryptography; the design, analysis and testing of block cipher algorithms; the design and analysis of security protocols based on computational intractability; authentication, authorization and their applications.
Similar content being viewed by others
Explore related subjects
Discover the latest articles and news from researchers in related subjects, suggested using machine learning.References
Dai Z, Jiang S, Imamura K, et al. Asymptotic behavior of normalized linear complexity of ultimately non-periodic binary sequences. IEEE Transactions on Information Theory, 2004, 50(11): 2911–2915
Hu H G, Feng D G, Wu W L. Incomplete exponential sums over Galois rings with applications to some binary sequences derived from Z 2 1. IEEE Transactions on Information Theory, 2006, 52(5): 2260–2265
Wang L P, Zhu Y F, Pei D Y. On the lattice basis reduction multisequence synthesis algorithm. IEEE Transactions on Information Theory, 2004, 50(11): 2905–2910
Dai Z, Yang J. Multi-continued fraction algorithm and generalized B-M algorithm over Fq. Finite Fields and Their Applications, 2006, 12: 379–402
Dai Z. Multi-continued fraction algorithms and their applications to sequences. In: Proceedings of SETA2006. LNCS, 2006, 4086: 17–33
Hu H G, Feng D G. On the 2-adic complexity and the k-error 2-adic complexity of periodic binary sequences. In: Proceedings of SETA 2004. LNCS, 2005, 3486: 185–196
Feng X, Dai Z. Expected value of the normalized linear complexity of two-dimensional binary sequences. In: Proceedings of SETA 2004. LNCS, 2005, 3486: 113–128
Dai Z, Feng X, Yang J. Multi-continued fraction algorithm and generalized B-M algorithm over F2. In: Proceedings of SETA 2004. LNCS, 2005, 3486: 339–354
Dai Z, Imamura K, Yang J. Asymptotic behavior of normalized linear complexity of multi-sequences. In: Proceedings of SETA 2004. LNCS, 2005, 3486: 129–142
Wu C K, Dawson E. Correlation immunity and resiliency of symmetric boolean functions. Theoretical Computer Science, 2004, 312: 321–335
Zhang W Y, Wu C Kun, Li S Q. Construction of cryptographically important boolean permutations. Applicable Algebra in Engineering, Communication and Computing, 2004, 15(3–4): 173–177
Zhu Y F, Pei D Y. An algorithm for DLP on anomalous elliptic curves over Fp. Science in China Series A, 2002, 45(6): 773–777
Pei D Y. Authentication Codes and Combinatorial Designs. Boca Raton: Chapman & Hall/CRC, 2006
Wang M, Feng D. On Lin-Bose problem. Linear Algebra and Its Applications, 2004, 390: 279–285
Lu K. On the k(GV)-problem with a cyclic sylow 2-subgroup. Algebra Colloquinm, 2002, 9(2): 163–175
Zhang B, Feng D G. New guess-and-determine attack on the self-shrinking generator. In: Proceedings of ASIACRYPT 2006. LNCS, 2006, 4284: 54–68
Zhang B, Wu H J, Feng D G, et al. A fast correlation attack on the shrinking generator. In: Proceedings of RSA 2005. LNCS, 2005, 3376: 72–86
Zhang B, Feng D G. Security analysis of a new stream cipher. Science in China Series F, 2006, 49(3): 286–301
Zhang B, Wu H J, Feng D G, et al. Weaknesses of COSvd(2, 128) stream cipher. In: Proceedings of ICISC 2005. LNCS, 2005, 3935: 270–283
Wu W L, Feng D G. Linear cryptanalysis of NUSH block cipher. Science in China Series F, 2002, 45(1): 59–67
Wu W L, Feng D G. Collision attack of reduced-round camellia. Science in China Series F, 2005, 48(1): 78–90
Wu W L, Zhang W T, Feng D G. Improved integral cryptanalysis of FOX block cipher. In: Proceedings of ICISC 2005. LNCS, 2005, 3935: 229–241
Wang P, Feng D G, Wu W L. On the security of tweakable modes of operation: TBC and TAE. In: Proceedings of ISC 2005. LNCS, 2005, 3650: 274–287
Nie X Y, Hu L, Li J Y. Crystal updegrove, and Jintai Ding. Breaking a new instance of TTM cryptosystems. In: Proceedings of ACNS 2006. LNCS, 2006, 3989: 210–225
Li H D, Li B. An unbounded simulation-sound non-interactive zero-knowledge proof system for NP. In: Proceedings of ISC 2005. LNCS, 2005, 3822: 210–220
Deng Y, Lin D H. Instance-dependent verifiable random functions and their applications to simultaneous resetability. In: Proceedings of Eurocrypt 2007. LNCS, 2007, 4515: 134–154
Zhang Z F, Feng D G, Xu J, et al. Efficient ID-based optimistic fair exchange with provable security. In: Proceedings of ICICS 2005. LNCS, 2005, 3783: 14–26
Zhang Z F, Feng D G. Efficient fair certified e-mail delivery based on RSA. In: Proceedings of ISPA 2005. LNCS, 2005, 3759: 368–377
Zhang Z F, Xu J, Feng D G. Efficient identity-based protocol for fair certified e-mail delivery. In: Proceedings of CANS 2005. LNCS, 2005, 3810: 200–210
Zhang Z F, Wong D S, Xu J, et al. Certificateless public-key signature: Security model and efficient construction. In: Proceedings of ACNS 2006. LNCS, 2006, 3989: 293–308
Hu B C, Wong D S, Zhang Z F, et al. Key replacement attack against a generic construction of certificateless signature. In: Proceedings of ACISP 2006. LNCS, 2006, 4058: 235–246
Zhu W T. Optimizing the tree structure in secure multicast key management. IEEE Communications Letters, 2005, 9(5): 477–479
Xu J, Zhang Z F, Feng D G. ID-based proxy signature using bilinear pairings, parallel and distributed processing and applications. LNCS, 2005, 3759: 359–367
Xu J, Zhang Z F, Feng D G. ID-based aggregate signatures from bilinear pairings. In: Proceedings of CANS 2005. LNCS, 2005, 3810: 110–119
Zhang F, Feng D G. Identity-based PKI scheme for machine readable travel document. AINA, 2006, (2): 461–465
Xu Z, Feng D G, Li L, et al. UC-RBAC: A usage constrained role-based access control model. In: Proceedings of. ICS 2003. LNCS, 2003, 2836: 337–347
Li X F, Feng D G. Composing administrative scope of delegation policies based on extended XACML. In: Proceedings of EDOC 2006. Washington DC: IEEE Computer Society, 2006, 467–470
Wang W J, Hu L. Efficient and provably secure generic construction of three-party password-based authenticated key exchange protocols. In: Proceedings of INDOCRYPT 2006. LNCS, 2006, 4329: 118–132
Dai Z, Wang K, Ye D. Multi-continued fraction algorithm on multi-formal laurent series. ACTA Arith, 2006, 122(1): 1–16
Hu L, Pei D. Polynomial characterization of characteristic ideal of maximal periodic arrays over Galois rings. Discrete Mathematics, 2004, 278(1–3): 139–149
Jiang S, Dai Z, Gong G. On interleaved sequences over finite fields. Discrete Mathematics, 2002, 252(1–3): 161–178
Wang K, Zhang X K. Subgroups of ideal class groups of real quadratic algebraic function fields. Science in China A, 2003, 46(3): 339–345
Hu L. Maximal periodic two-dimensional arrays over Galois rings. Communication in Algebra, 2005, 33(7): 2361–2374
Lv S W, Fan X B, Zhou Y J. Design and Analysis of Stream Ciphers. Beijing: China Soft Electronics Press, 2003
Wang P, Feng D G, Wu W L. Symmetric nonce respecting security model and the MEM mode of operation. In: Proceedings of INDOCRYPT 2006. LNCS, 2006, 4329: 280–286
Wang P, Feng D G, Wu W L. HCTR: A tweakable enciphering mode. In: Proceedings of SKLOIS CSIC 2005. LNCS, 2005, 3822: 175–188
Yin Y, Li B. Secure cross-realm C2C-PAKE protocol, information security and privacy. In: Proceedings of ACISP 2006. LNCS, 2006, 4058: 395–406
Sun H B, Lin D D. Dynamic security analysis of group key agreement protocol. IEE Proceedings Communications, 2005, 152(2): 134–137
Cao T J, Lin D D, Xue R. A randomized RSA-based partially blind signature scheme for electronic cash. Computers and Security, 2005, 24(1): 44–49
Zhang Z F, Feng D G. Cryptanalysis of some signature scheme with message recovery. Applied Mathematics and Computation, 2005, 170(1): 103–114
Yao G, Ren K, Bao F, et al. Making the key agreement protocol in mobile ad hoc network more efficient. In: Proceedings of ACWS 2003. LNCS, 2003, 2846: 343–356
Zhou Z F. Classification of universally ideal homomorphic secret sharing schemes and ideal black-box secret sharing schemes. In: Proceedings of ISC 2005. LNCS, 2005, 3822: 370–383
Li H D, Yang X, Feng D G, et al. Distributed oblivious function evaluation and its applications. Journal of Computer Science and Technology, 2004, 19(6): 942–947
Li H D, Ji D Y, Feng D G, et al. Oblivious polynomial evaluation. Journal of Computer Science and Technology, 2004, 19(4): 550–554
Zhu W T. Cryptanalysis of two group key management protocols for secure multicast. In: Proceedings of CANS 2005. LNCS, 2005, 3810: 35–48
Wang L M, Wu C K. Authenticated group key agreement for multicast. In: Proceedings of CANS 2006. LNCS, 2006, 4301: 55–72
Fan H, Feng D G. Theory and Methodology of Security Protocols. Beijing: Science Press, 2003
Feng D G. Principle and Technology of Network Security. Beijing: Science Press, 2003
Zhang Y Q, Dai Z F. Secure Scan Technology. Beijing: Tsinghua University Press, 2004
Lian Y F, Wang H. Principle and Technology of Network Attacks. Beijing: Science Press, 2004
Dai Y X, Lian Y F, Wang H. System Security and Intrusion Detection. Beijing: Tsinghua University Press, 2002
Dai Y X, Xu J Z, Zhai Q B, et al. Computer Network Security. Beijing: Tsinghua University Press, 2005
Li D Q, Su P R. Emergency Response of Information Systems. Beijing: Science Press, 2005
Hu Z Y, Liu Z Q, Su P R, et al. Blocking MSN: A case study of preventing the abuse of IM. In: Proceedings of APCC 2005. IEEE, 2005, 1112–1116
Liu Z Q, Feng D G. Incremental fuzzy decision tree-based network forensic system. In: Proceedings of. CIS 2005. IEEE, LNCS, 2005, 3802(2): 995–1002
Su P R, Li D Q, Qu H P, et al. Detecting the deviations of privileged process execution. In: Proceedings of ICN 2005. LNCS, 2005, 3421: 980–988
Qu H P, Li D Q, Su P R, et al. A packet marking scheme for IP traceback. In: Proceedings of ICN 2005. LNCS, 2005, 3421: 964–971
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Feng, D., Wu, C. Advances in cryptography and information security—introduction of 2002–2006 progress of SKLOIS. Front. Comput. Sc. China 1, 385–396 (2007). https://doi.org/10.1007/s11704-007-0037-9
Received:
Accepted:
Issue Date:
DOI: https://doi.org/10.1007/s11704-007-0037-9