Abstract
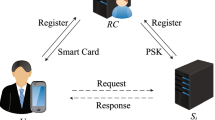
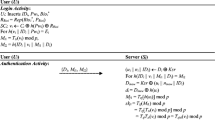
As service demands rise and expand single-server user authentication has become unable to satisfy actual application demand. At the same time identity and password based authentication schemes are no longer adequate because of the insecurity of user identity and password. As a result biometric user authentication has emerged as a more reliable and attractive method. However, existing biometric authentication schemes are vulnerable to some common attacks and provide no security proof, some of these biometric schemes are also either inefficient or lack sufficient concern for privacy. In this paper, we propose an anonymous and efficient remote biometric user authentication scheme for a multi-server architecture with provable security. Through theoretical mathematic deduction, simulation implementation, and comparison with related work, we demonstrate that our approach can remove the aforementioned weaknesses and is well suited for a multi-server environment.
Similar content being viewed by others
References
Lamport L. Password authentication with insecure communication. Communications of the ACM, 1981, 24(11): 770–772
He D B, Chen J H, Hu J. An ID-based client authentication with key agreement protocol for mobile client-server environment on ECC with provable security. Information Fusion, 2012, 13(3): 223–230
Li L H, Lin L C, Hwang M S. A remote password authentication scheme for multi-server architecture using neural networks. IEEE Transactions on Neural Networks, 2001, 12(6): 1498–1504
He D B. An efficient remote user authentication and key exchange protocol for mobile client-server environment from pairings. Ad Hoc Networks, 2012, 10(6): 1009–1016
Liao Y P, Wang S S. A secure dynamic ID based remote user authentication scheme for multi-server environment. Computer Standards & Interfaces, 2009, 31(1): 24–29
He D B, Chen J H, Chen Y T. A secure mutual authentication scheme for session initiation protocol using elliptic curve cryptography. Security and Communication Networks, 2012, 5(12): 1423–1429
Li X, Niu J W, Khan M K, Wang Z B. Applying LU decomposition of matrices to design anonymity bilateral remote user authentication scheme. Mathematical Problems in Engineering. 2013, Article ID 910409, 10 pages, DOI:10.1155/2013/910409
Chen T H, Chen Y C, Shih WK, Wei HW. An efficient anonymous authentication protocol for mobile pay-TV. Journal of Network and Computer Applications, 2011, 34(4): 1131–1137
He D B, Chen J H, Zhang R. A more secure authentication scheme for telecare medicine information systems. Journal of Medical Systems, 2012, 36(3): 1989–1995
Leung K C, Cheng L M, Fong A S, Chan C K. Cryptanalysis of a modified remote user authentication scheme using smart cards. IEEE Transactions on Consumer Electronics, 2003, 49(4): 1243–1245
Fan C I, Chan Y C, Zhang Z K. Robust remote authentication scheme with smart cards. Computers & Security, 2005, 24(8): 619–628
Lee SW, Kim H S, Yoo K Y. Efficient nonce-based remote user authentication scheme using smart cards. Applied Mathematics and Computation, 2005, 167(1): 355–361
Juang W S. Efficient multi-server password authenticated key agreement using smart cards. IEEE Transaction on Consumer Electronics, 2004, 50(1): 251–255
Tai J L. Efficient multi-server authentication scheme based on one-way hash function without verification table. Computers & Security, 2008, 27(3–4): 115–121
Hsiang H C, Shih W K. Improvement of the secure dynamic ID based remote user authentication scheme for multi-server environment. Computer Standards & Interfaces, 2009, 31(6): 1118–1123
Yoon E J, Yoo K Y. Robust biometrics-based multi-server authentication with key agreement scheme for smart cards on elliptic curve cryptosystem. Journal of Supercomputing, 2013, 63(1): 235–255
Lee C C, Lin T H, Chang R X. A secure dynamic ID based remote user authentication scheme for multi-server environment using smart cards. Expert Systems with Applications, 2011, 38: 13863–13870
Li X, Xiong Y P, Ma J, Wang W D. An efficient and security dynamic identity based authentication protocol for multi-server architecture using smart cards. Journal of Network and Computer Applications, 2012, 35: 763–769
Liao Y P, Hsiao C M. A novel multi-server remote user authentication scheme using self-certified public keys for mobile clients. Future Generation Computer Systems, 2013, 29(3): 886–900
Ratha N K, Connell J H, Bolle R M. Enhancing security and privacy in biometrics-based authentication systems. IBM Systems Journal, 2001, 40(3): 614–634
He D B, Chen J H, Hu J. Improvement on a smart card based password authentication scheme. Journal of Internet Technology, 2012, 13(3): 405–410
He D B, Chen J H, Hu J. Further improvement of Juang et al.’s password-authenticated key agreement scheme using smart cards. Kuwait Journal of Science & Engineering, 2011, 38(2A): 55–68
Li X, Niu J W, Liao J G, Liang W. Cryptanalysis of a dynamic identity based remote user authentication scheme with verifiable password update. International Journal of Communication Systems, 2013, DOI: 10.1002/dac.2676
He D B, Wang D, Wu S H. Cryptanalysis and improvement of a password-based remote user authentication scheme without smart cards. Information Technology and Control, 2013, 42(2): 170–177
Li X, Ma J, Wang W D, Xiong Y P, Zhang J S. A novel smart card and dynamic ID based remote user authentication scheme for multi-server environment. Mathematical and Computer Modelling, 2013, 58(1–2): 85–95
Jiang P, Wen Q Y, Li W M, Jin Z P, Zhang H. An anonymous user authentication with key agreement scheme without pairings for multi server architecture using SCPKs. The Scientific World Journal, 2013, DOI:10.1155/2013/419592
Li X, Niu J W, Khan M K, Liao J G. An enhanced smart card based remote user password authentication scheme. Journal of Network and Computer Applications, 2013, 36(5): 1365–1371
Lee J K, Ryu S R, Yoo K Y. Fingerprint-based remote user authentication scheme using smart cards. Electronics Letters, 2002, 38(12): 554–555
Lin C H, Lai Y Y. A flexible biometrics remote user authentication scheme. Computer Standards and Interfaces, 2004, 27(1): 19–23
Chang C C, Lin I C. Remarks on fingerprint-based remote user authentication scheme using smart cards. ACM SIGOPS Operating Systems Review, 2004, 38(4): 91–96
Kim H S, Lee SW, Yoo K Y. ID-based password authentication scheme using smart cards and fingerprints. ACM SIGOPS Operating Systems Review, 2003, 37(4): 32–41
Scott M. Cryptanalysis of an ID-based password authentication scheme using smart cards and fingerprints. ACM SIGOPS Operating Systems Review, 2004, 38(2): 73–75
Khan M K, Zhang J S. Improving the security of a flexible biometrics remote user authentication scheme. Computer Standards & Interfaces, 2007, 29(1): 82–85
Li C T, Hwang M S. An efficient biometrics-based remote user authentication scheme using smart cards. Journal of Network and Computer Applications, 2010, 33(1): 1–5
Li X, Niu J W, Ma J, Wang W D, Liu C L. Cryptanalysis and improvement of a biometric-based remote authentication scheme using smart cards. Journal of Network and Computer Applications, 2011, 34(1): 73–79
Das A K. Analysis and improvement on an efficient biometric-based remote user authentication scheme using smart cards. IET Information Security, 2011, 5(3): 145–151
Kim H H, Jeon W R, Lee K W, Lee Y H, Won D H. Cryptanalysis and improvement of a biometrics-based multi-server authentication with key agreement scheme. In: Proceedings of Computational Science and its Applications. 2012, 7335: 391–406
Li X, Niu JW, Wang Z B, Chen C. Applying biometrics to design threefactor remote user authentication scheme with key agreement. Security and Communication Networks, 2013, DOI: 10.1002/sec.767
Lee C C, Hsu C W. A secure biometric-based remote user authentication with key agreement scheme using extended chaotic maps. Nonlinear Dynamics, 2013, 71(1–2): 201–211
Chen J, Yang Y. Activity completion duration based checkpoint selection for dynamic verification of temporal constraints in grid work-flow systems. International Journal of High Performance Applications, 2008, 22(3): 319–329
Jain A K, Nandakumar K, Nagar A. Biometric template security. EURASIP Journal on Advances in Signal Processing, 2008, 1–17
Dodis Y, Reyzin L, Smith A. Fuzzy extractors: How to generate strong keys from biometrics and other noisy data. In advances in Cryptology-EUROCRYPT, 2005, 3027: 523–540
Abdalla M, Fouque P A, Pointcheval D. Password-based authenticated key exchange in the three-party setting. In: Procedings of the 8th International Workshop on Theory and Practice in Public Key Cryptography (PKC 2005). 2005, 3386: 65–84
Hankerson D, Menezes A, Vanstone S. Guide to elliptic curve cryptography. New York: Springer-Verlag, 2004
Author information
Authors and Affiliations
Corresponding author
Additional information
Peng Jiang received her BS in mathematics and applied mathematics from Southeast University, China in 2010. She is currently a PhD candidate in the Department of State Key Laboratory of Networking and Switch Technology, Beijing University of Posts and Telecommunications, China. Her research interests include information security and privacy concerns.
Qiaoyan Wen received her BS and MS in mathematics from Shaanxi normal University, China, in 1981 and 1984, respectively, and her PhD in Cryptography from Xidian University, China in 1997. She is a professor of Beijing University of Posts and Telecommunications. Her research interests include coding theory, cryptography, information security, Internet security, and applied mathematics.
Wenmin Li received the BS and MS in mathematics and applied mathematics from Shaanxi Normal University, China in 2004 and 2007, respectively, and her PhD in Cryptology from Beijing University of Posts and Telecommunications, China in 2012. She is currently a lecturer in Beijing University of Posts and Telecommunications, China. Her research interests include cryptography and information security.
Zhengping Jin received his BS in mathematics and applied mathematics, and his MS in applied mathematics from Anhui Normal University, China in 2004 and 2007 respectively, and his PhD in Cryptography from Beijing University of Posts and Telecommunications, China in 2010. Now he is a lecturer of Beijing University of Posts and Telecommunications. His research interests include cryptography, information security, Internet security, and applied mathematics.
Hua Zhang received her BS in telecommunications engineering in 1998, and her MS in cryptology in 2005, both from Xidian University, China and her PhD in cryptology from Beijing University of Posts and Telecommunications, China in 2008. Now she is an associate professor of Beijing University of Posts and Telecommunications. Her research interests include cryptography, information security, and network security.
Rights and permissions
About this article
Cite this article
Jiang, P., Wen, Q., Li, W. et al. An anonymous and efficient remote biometrics user authentication scheme in a multi server environment. Front. Comput. Sci. 9, 142–156 (2015). https://doi.org/10.1007/s11704-014-3125-7
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11704-014-3125-7