Abstract
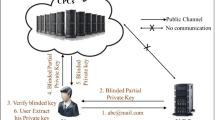
Identity-based threshold signature (IDTS) is a forceful primitive to protect identity and data privacy, in which parties can collaboratively sign a given message as a signer without reconstructing a signing key. Nevertheless, most IDTS schemes rely on a trusted key generation center (KGC). Recently, some IDTS schemes can achieve escrow-free security against corrupted KGC, but all of them are vulnerable to denial-of-service attacks in the dishonest majority setting, where cheaters may force the protocol to abort without providing any feedback. In this work, we present a fully decentralized IDTS scheme to resist corrupted KGC and denial-of-service attacks. To this end, we design threshold protocols to achieve distributed key generation, private key extraction, and signing generation which can withstand the collusion between KGCs and signers, and then we propose an identification mechanism that can detect the identity of cheaters during key generation, private key extraction and signing generation. Finally, we formally prove that the proposed scheme is threshold unforgeability against chosen message attacks. The experimental results show that the computation time of both key generation and signing generation is <1 s, and private key extraction is about 3 s, which is practical in the distributed environment.
Similar content being viewed by others
Explore related subjects
Discover the latest articles and news from researchers in related subjects, suggested using machine learning.References
Working Group on E-CNY Research and Development of the People’s Bank of China. Progress of research & development of E-CNY in China. See en.wikisource.org/wiki/Progress_on_Research_and_Development_of_E-CNY_in_China website, 2021
Nakamoto S. Bitcoin: a peer-to-peer electronic cash system. See bitcoin.org/bitcoin website, 2009
Mu Y H, Xu H X, Li P L, Ma T J. Secure two-party SM9 signing. Science China Information Sciences, 2020, 63(8): 189101
Yin H, Qin Z, Zhang J, Ou L, Li F, Li K. Secure conjunctive multi-keyword ranked search over encrypted cloud data for multiple data owners. Future Generation Computer Systems, 2019, 100: 689–700
Song F, Qin Z, Liu D, Zhang J, Lin X, Shen X. Privacy-preserving task matching with threshold similarity search via vehicular crowdsourcing. IEEE Transactions on Vehicular Technology, 2021, 70(7): 7161–7175
Lindell Y. Fast secure two-party ECDSA signing. In: Proceedings of the 37th Annual International Cryptology Conference. 2017, 613–644
Ou L, Yin H, Qin Z, Xiao S, Yang G, Hu Y. An efficient and privacy-preserving multiuser cloud-based LBS query scheme. Security and Communication Networks, 2018, 2018: 4724815
Brandão L T A N, Davidson M, Vassilev A. NIST roadmap toward criteria for threshold schemes for cryptographic primitives. See csrc.nist.gov/publications/detail/nistir/8214a/final website, 2020
Gennaro R, Jarecki S, Krawczyk H, Rabin T. Robust threshold DSS signatures. In: Proceedings of International Conference on the Theory and Applications of Cryptographic Techniques. 1996, 354–371
MacKenzie P, Reiter M K. Two-party generation of DSA signatures. In: Proceedings of the 21st Annual International Cryptology Conference. 2001, 137–154
Kate A, Goldberg I. Distributed private-key generators for identity-based cryptography. In: Proceedings of the 7th International Conference on Security and Cryptography for Networks. 2010, 436–453
Boneh D, Franklin M. Identity-based encryption from the Weil pairing. In: Proceedings of the 21st Annual International Cryptology Conference. 2001, 213–229
Gennaro R, Jarecki S, Krawczyk H, Rabin T. Secure distributed key generation for discrete-log based cryptosystems. In: Proceedings of the 17th International Conference on the Theory and Application of Cryptographic Techniques. 1999, 295–310
Hess F. Efficient identity based signature schemes based on pairings. In: Proceedings of the 9th Annual International Workshop on Selected Areas in Cryptography. 2002, 310–324
Choon J C, Hee Cheon J. An identity-based signature from gap Diffie-Hellman groups. In: Proceedings of the 6th International Workshop on Theory and Practice in Public Key Cryptography. 2003, 18–30
Paterson K G, Schuldt J C N. Efficient identity-based signatures secure in the standard model. In: Proceedings of the 11th Australasian Conference on Information Security and Privacy. 2006, 207–222
Barreto P S L M, Libert B, McCullagh N, Quisquater J J. Efficient and provably-secure identity-based signatures and signcryption from bilinear maps. In: Proceedings of the 11th International Conference on the Theory and Application of Cryptology and Information Security. 2005, 515–532
Ishai Y, Ostrovsky R, Zikas V. Secure multi-party computation with identifiable abort. In: Proceedings of the 34th Annual Cryptology Conference on Advances in Cryptology. 2014, 369–386
Baek J, Zheng Y. Identity-based threshold signature scheme from the bilinear pairings. In: Proceedings of International Conference on Information Technology: Coding and Computing. 2004, 124–128
Chen X, Zhang F, Konidala D M, Kim K. New ID-based threshold signature scheme from bilinear pairings. In: Proceedings of the 5th International Conference on Cryptology in India. 2004, 371–383
Shao J, Cao Z, Wang L. Efficient ID-based threshold signature schemes without pairings. See eprint.iacr.org website, 2006
Gao W, Wang G, Wang X, Yang Z. One-round ID-based threshold signature scheme from bilinear pairings. Informatica, 2009, 20(4): 461–476
Xiong H, Li F, Qin Z. Provably secure identity based threshold signature withoutrandom oracles. International Journal of Computers and Applications, 2009, 31(4): 290–295
Xiong H, Qin Z, Li F. Identity-based threshold signature secure in the standard model. International Journal of Network Security, 2010, 10(1): 75–80
Li F, Gao W, Wang G L, Chen K F, Wang X L. Efficient identity-based threshold signature scheme from bilinear pairings in standard model. International Journal of Internet Protocol Technology, 2014, 8(2–3): 107–115
Zhang Y, He D, Zeadally S, Wang D, Choo K K R. Efficient and provably secure distributed signing protocol for mobile devices in wireless networks. IEEE Internet of Things Journal, 2018, 5(6): 5271–5280
He D, Zhang Y, Wang D, Choo K K R. Secure and efficient two-party signing protocol for the identity-based signature scheme in the IEEE P1363 standard for public key cryptography. IEEE Transactions on Dependable and Secure Computing, 2020, 17(5): 1124–1132
Feng Q, He D, Wang H, Wang D, Huang X. Multi-party key generation protocol for the identity-based signature scheme in the IEEE P1363 standard for public key cryptography. IET Information Security, 2020, 14(6): 724–732
Feng Q, He D, Liu Z, Wang D, Choo K K R. Distributed signing protocol for IEEE P1363-compliant identity-based signature scheme. IET Information Security, 2020, 14(4): 443–451
Desmedt Y G. Threshold cryptography. European Transactions on Telecommunications, 1994, 5(4): 449–458
Gennaro R, Goldfeder S. One round threshold ECDSA with identifiable abort. See eprint.iacr.org website, 2020
Canetti R, Gennaro R, Goldfeder S, Makriyannis N, Peled U. UC non-interactive, proactive, threshold ECDSA with identifiable aborts. In: Proceedings of 2020 ACM SIGSAC Conference on Computer and Communications Security. 2020, 1769–1787
Zhang F, Zhang J. Efficient and information-theoretical secure verifiable secret sharing over bilinear groups. Chinese Journal of Electronics, 2014, 23(1): 13–17
Feldman P. A practical scheme for non-interactive verifiable secret sharing. In: Proceedings of the 28th Annual Symposium on Foundations of Computer Science. 1987, 427–438
Gennaro R, Goldfeder S. Fast multiparty threshold ECDSA with fast trustless setup. In: Proceedings of 2018 ACM SIGSAC Conference on Computer and Communications Security. 2018, 1179–1194
Paillier P. Public-key cryptosystems based on composite degree residuosity classes. In: Proceedings of International Conference on the Theory and Application of Cryptographic Techniques. 1999, 223–238
Gennaro R, Goldfeder S, Ithurburn B. Fully distributed group signatures. See orbs.com/white-papers/fully-distributed-group-signatures/ website, 2019
Fiat A, Shamir A. How to prove yourself: practical solutions to identification and signature problems. In: Proceedings of Annual International Cryptology Conference. 1986, 186–194
Schnorr C P. Efficient signature generation by smart cards. Journal of Cryptology, 1991, 4(3): 161–174
Goldberg S, Reyzin L, Sagga O, Baldimtsi F. Efficient noninteractive certification of RSA moduli and beyond. In: Proceedings of the 25th International Conference on the Theory and Application of Cryptology and Information Security. 2019, 700–727
Lindell Y, Nof A. Fast secure multiparty ECDSA with practical distributed key generation and applications to cryptocurrency custody. In: Proceedings of 2018 ACM SIGSAC Conference on Computer and Communications Security. 2018, 1837–1854
Castagnos G, Catalano D, Laguillaumie F, Savasta F, Tucker I. Bandwidth-efficient threshold EC-DSA revisited: online/offline extensions, identifiable aborts proactive and adaptive security. Theoretical Computer Science, 2022, doi: https://doi.org/10.1016/j.tcs.2022.10.016
Acknowledgements
This work was support by the National Key R&D Program of China (No. 2021YFB3100400), the National Natural Science Foundation of China (Grant Nos. 62172216, U20A201092), the Jiangsu Provincial Key Research and Development Program (Nos. BE2022068, BE2022068-2), the Key R&D Program of Guangdong Province (No. 2020B0101090002), the Natural Science Foundation of Jiangsu Province (No. BK20211180), the Research Fund of Guangxi Key Laboratory of Trusted Software (No. KX202034), the Research Fund of State Key Laboratory of Integrated Services Networks (Xidian University) (No. ISN23-20), the Fund of Prospective Layout of Scientific Research for NUAA (Nanjing University of Aeronautics and Astronautics), and JSPS Postdoctoral Fellowships (No. P21073).
Author information
Authors and Affiliations
Corresponding author
Additional information
Yan Jiang is currently working toward the PhD degree at the College of Computer Science and Technology, Nanjing University of Aeronautics and Astronautics, China. His research interests include privacy-preserving protocols in network systems and clouds.
Youwen Zhu received his BE degree and PhD degree in Computer Science from University of Science and Technology of China, China in 2007 and 2012, respectively. From 2012 to 2014, he is a JSPS postdoc in Kyushu University, Japan. He is currently a professor at the College of Computer Science and Technology, Nanjing University of Aeronautics and Astronautics, China. He has published more than 40 papers in refereed international conferences and journals, and has served as program committee member in several international conferences. His research interests include identity authentication, information security and data privacy.
Jian Wang received the PhD degrees in Nanjing University, China in 1998. He is currently a Professor at the College of Computer Science and Technology, Nanjing University of Aeronautics and Astronautics, China. His research interests include cryptographic protocol and malicious tracking.
Xingxin Li received the PhD degree in Computer Science and Technology from Nanjing University of Aeronautics and Astronautics, China. He is currently a postdoc at Department of Mathematical Informatics, University of Tokyo, Japan. His research interests include secure outsourcing computation and privacy-preserving machine learning.
Electronic supplementary material
Rights and permissions
About this article
Cite this article
Jiang, Y., Zhu, Y., Wang, J. et al. Fully distributed identity-based threshold signatures with identifiable aborts. Front. Comput. Sci. 17, 175813 (2023). https://doi.org/10.1007/s11704-022-2370-4
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11704-022-2370-4