Abstract
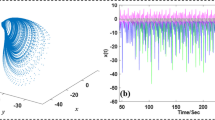
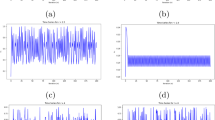
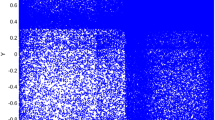
To strengthen contemporary image encryption techniques and make them more secure, a new image encryption algorithm was proposed using a one-dimensional improved discrete cosine fractional chaotic map (1D-IDCF). To evaluate the randomness and ergodicity of the chaotic map, its behaviour was analysed through bifurcation diagram, Lyapunov exponent, NIST test, key sensitivity, and key space analysis. The results demonstrate that the proposed chaotic map has high unpredictability and a large Lyapunov exponent, which defines initial sensitivity. Additionally, an encryption algorithm was developed that involves pixel-level scrambling, binary bit-plane extraction, simultaneous confusion of bit planes, binary-to-gray conversion, and bit-XOR operations with a chaotic key matrix generated using the one-dimensional improved cosine fractional chaotic map (1D-IDCF). Experimental results based on various performance metrics, including information entropy, correlation coefficient, chi-square (\(\chi ^2\)) test, histogram variance, Number of Pixels Change Rate (NPCR), and Unified Average Changing Intensity (UACI), demonstrate that the proposed encryption scheme provides a significant level of unpredictability. Additionally, the proposed algorithm exhibits robustness against various attacks, including noise, data loss, and differential attacks. Furthermore, the low Peak Signal to Noise Ratio (PSNR) (8.3615 dB) indicates good encryption capability and robustness against cryptographic attacks.












Similar content being viewed by others
Data availibility statement
No datasets were generated or analysed during the current study.
References
Youssef, M., Gabr, M., Alexan, W., Mansour, M.B.M., Kamal, K., Hosny, H., El-Damak, D.: Enhancing satellite image security through multiple image encryption via hyperchaos, svd, rc5, and dynamic s-box generation. IEEE Access (2024)
El-Damak, D., Alexan, W., Mamdouh, E., El-Aasser, M., Fathy, A., Gabr, M.: Fibonacci q-matrix, hyperchaos, and galois field (2 8) for augmented medical image encryption. IEEE Access (2024)
Alexan, W., Aly, L., Korayem, Y., Gabr, M., El-Damak, D., Fathy, A., Mansour, H.A.: Secure communication of military reconnaissance images over uav-assisted relay networks. IEEE Access (2024)
Gabr, M., Diab, A., Elshoush, H.T., Chen, Y.-L., Por, L.Y., Ku, C.S., Alexan, W.: Data security utilizing a memristive coupled neural network in 3d models. IEEE Access (2024). https://doi.org/10.1109/ACCESS.2024.3447075
Alexan, W., Mamdouh, E., Aboshousha, A., Alsahafi, Y.S., Gabr, M., Hosny, K.M.: Stegocrypt: A robust tri-stage spatial steganography algorithm using tlm encryption and dna coding for securing digital images. IET Image Processing (2024)
Coppersmith, D.: The data encryption standard (des) and its strength against attacks. IBM J. Res. Dev. 38(3), 243–250 (1994)
Rijmen, V., Daemen, J.: Advanced encryption standard. In: Proceedings of Federal Information Processing Standards Publications, pp. 19–22 (2001). National Institute of Standards and Technology
Rivest, R.L., Shamir, A., Adleman, L.: A method for obtaining digital signatures and public-key cryptosystems. Commun. ACM 21(2), 120–126 (1978)
Dong, W., Li, Q., Tang, Y., Hu, M., Zeng, R.: A robust and multi chaotic dna image encryption with pixel-value pseudorandom substitution scheme. Opt. Commun. 499, 127211 (2021)
Guo, Z., Sun, P.: Improved reverse zigzag transform and dna diffusion chaotic image encryption method. Multimed. Tools Appl. 81(8), 11301–11323 (2022)
Shao, Z., Liu, X., Yao, Q., Qi, N., Shang, Y., Zhang, J.: Multiple image encryption based on chaotic phase mask and equal modulus decomposition in quaternion gyrator domain. Sig. Process. Image Commun. 80, 115662 (2020)
Liang, Q., Zhu, C.: A new one-dimensional chaotic map for image encryption scheme based on random dna coding. Opt. & Laser Technol. 160, 109033 (2023)
Liao, X., Li, K., Yin, J.: Separable data hiding in encrypted image based on compressive sensing and discrete fourier transform. Multimed. Tools Appl. 76, 20739–20753 (2017)
Alexan, W., Gabr, M., Mamdouh, E., Elias, R., Aboshousha, A.: Color image cryptosystem based on sine chaotic map, 4d chen hyperchaotic map of fractional-order and hybrid dna coding. IEEE Access 11, 54928–54956 (2023)
Gabr, M., Elias, R., Hosny, K.M., Papakostas, G.A., Alexan, W.: Image encryption via base-n prngs and parallel base-n s-boxes. IEEE Access 11, 85002–85030 (2023)
Kong, X., Yu, F., Yao, W., Xu, C., Zhang, J., Cai, S., Wang, C.: A class of 2n+ 1 dimensional simplest hamiltonian conservative chaotic systems and fast image encryption schemes. Appl. Math. Model. 125, 351–374 (2024)
Patro, K.A.K., Acharya, B.: An efficient colour image encryption scheme based on 1-d chaotic maps. J. Inf. Secur. Appl. 46, 23–41 (2019)
Zhou, Y., Bao, L., Chen, C.P.: A new 1d chaotic system for image encryption. Signal Process. 97, 172–182 (2014)
Talhaoui, M.Z., Wang, X., Talhaoui, A.: A new one-dimensional chaotic map and its application in a novel permutation-less image encryption scheme. Vis. Comput. 37(7), 1757–1768 (2021)
Wang, X., Wang, Q., Zhang, Y.: A fast image algorithm based on rows and columns switch. Nonlinear Dyn. 79, 1141–1149 (2015)
Hua, Z., Yi, S., Zhou, Y.: Medical image encryption using high-speed scrambling and pixel adaptive diffusion. Signal Process. 144, 134–144 (2018)
Xu, L., Li, Z., Li, J., Hua, W.: A novel bit-level image encryption algorithm based on chaotic maps. Opt. Lasers Eng. 78, 17–25 (2016)
Pak, C., An, K., Jang, P., Kim, J., Kim, S.: A novel bit-level color image encryption using improved 1d chaotic map. Multimed. Tools Appl. 78(9), 12027–12042 (2019)
Li, M., Wang, P., Liu, Y., Fan, H.: Cryptanalysis of a novel bit-level color image encryption using improved 1d chaotic map. IEEE Access 7, 145798–145806 (2019)
Wang, X., Liu, P.: A new image encryption scheme based on a novel one-dimensional chaotic system. IEEE Access 8, 174463–174479 (2020)
Zheng, J., Lv, T.: Image encryption algorithm based on cascaded chaotic map and improved zigzag transform. IET Image Process. 16(14), 3863–3875 (2022)
Wen, H., Lin, Y., Kang, S., Zhang, X., Zou, K.: Secure image encryption algorithm using chaos-based block permutation and weighted bit planes chain diffusion. IScience 27(1) (2024)
Liu, H., Kadir, A., Xu, C.: Cryptanalysis and constructing s-box based on chaotic map and backtracking. Appl. Math. Comput. 376, 125153 (2020)
Liu, R., Liu, H., Zhao, M.: Cryptanalysis and construction of keyed strong s-box based on random affine transformation matrix and 2d hyper chaotic map. Expert. Syst. Appl. 252, 124238 (2024)
Xu, D., Liu, H.: Constructing a nondegenerate m-dimensional integer-domain chaotic map model over gf (2 n) with application in prng. Int. J. Bifurc. Chaos 34(13), 2450160 (2024)
Xu, D., Liu, H.: A non-degenerate m-dimensional integer domain chaotic map model over gf (2 n). Nonlinear Dyn. (2024). https://doi.org/10.1007/s11071-024-09517-8
Liu, R., Liu, H., Zhao, M.: Reveal the correlation between randomness and lyapunov exponent of n-dimensional non-degenerate hyper chaotic map. Integration 93, 102071 (2023)
Liu, H., Kadir, A., Xu, C.: Color image encryption with cipher feedback and coupling chaotic map. Int. J. Bifurc. Chaos 30(12), 2050173 (2020)
Midoun, M.A., Wang, X., Talhaoui, M.Z.: A sensitive dynamic mutual encryption system based on a new 1d chaotic map. Opt. Lasers Eng. 139, 106485 (2021)
Mansouri, A., Wang, X.: A novel one-dimensional sine powered chaotic map and its application in a new image encryption scheme. Inf. Sci. 520, 46–62 (2020)
L’ecuyer, P., Simard, R.: Testu01: Ac library for empirical testing of random number generators. ACM Trans. Math. Softw. (TOMS) 33(4), 1–40 (2007)
Liu, H., Niu, Y., Zhao, M.: Constructing a non-degeneracy nd chaotic map model and counteracting dynamic degradation through adaptive impulsive perturbation. Expert. Syst. Appl. 251, 123933 (2024)
Wang, X., Sun, H.: A chaotic image encryption algorithm based on zigzag-like transform and dna-like coding. Multimed. Tools Appl. 78(24), 34981–34997 (2019)
Liu, G., Jiang, T., et al.: Color image scrambling based on zigzag transformation. Comput. Eng. & Sci. 35(5), 106 (2013)
Zhou, Y., Panetta, K., Agaian, S., Chen, C.P.: (n, k, p)-gray code for image systems. IEEE Trans. Cybern. 43(2), 515–529 (2013)
Database, U.-S.I.: USC-SIPI Image Database. http://sipi.usc.edu/database/ (1977)
Gui, X., Huang, J., Li, L., Li, S., Cao, J.: A novel hyperchaotic image encryption algorithm with simultaneous shuffling and diffusion. Multimed. Tools Appl. 81(15), 21975–21994 (2022)
Zarei Zefreh, E., Abdali, M.: Lsie: a fast and secure latin square-based image encryption scheme. Multimed. Tools Appl. 83(3), 7939–7979 (2024)
Wu, Y., Noonan, J.P., Agaian, S., et al.: Npcr and uaci randomness tests for image encryption. Cyber journals: multidisciplinary journals in science and technology. J. Sel. Areas Telecommun. (JSAT) 1(2), 31–38 (2011)
Author information
Authors and Affiliations
Contributions
Maram Kumar, conceptualized the study, conducted the experiments, performed the analysis,wrote the original draft; Deepak. Ch, Conceptualization, supervision, validation, review and editing.
Corresponding author
Ethics declarations
Conflict of interest
The authors declare no Conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Kumar, M., Ch, D. Enhancing image security through a fusion of chaotic map and multi-level scrambling techniques. SIViP 19, 235 (2025). https://doi.org/10.1007/s11760-025-03814-4
Received:
Revised:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11760-025-03814-4