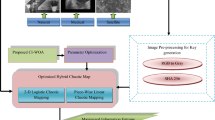
Abstract
The development of encryption and decryption plays a vital role in the field of security. Recently, Chaos-based security has suggested the reliable and efficient way of securing the images. In this paper, Self-Adaptive Grey Wolf Optimization (GWO) is proposed for optimizing 2-dimensional Logistic Chaotic Mapping (2DCM). Further, the security analysis of the proposed method is performed using different comparison such as key sensitivity, histogram analysis, adjacent pixel autocorrelation, information entropy, attacks, quality of encryption, Chi square test etc. Moreover, analytical outcomes are compared with the conventional algorithms like standard encryption and decryption, Genetic Algorithm (GA) and GWO. The experimental result stated that the proposed method is key sensitive and opposed to the general attacks during the encryption and decryption of images.









Similar content being viewed by others
References
Zhou N, Pan S, Cheng S, Zhou Z (2016) Image compression—encryption scheme based on hyper-chaotic system and 2D compressive sensing. Opt Laser Technol 82:121–133
Liu W, Sun K, Zhu C (2016) A fast image encryption algorithm based on chaotic map. Opt Lasers Eng 84:26–36
Murugan B, Nanjappa Gounder AG (2016) Image encryption scheme based on block-based confusion and multiple levels of diffusion. IET Comput Vision 10(6):593–602
Giovannozzi M (1993) Analysis of the stability domain for the Henon map. Phys Lett A 182(2–3):255–260
Wadi SM, Zainal N (2015) Decomposition by binary codes-based speedy image encryption algorithm for multiple applications. IET Image Proc 9(5):413–423
Sun Y, Xu R, Chen L, Hu X (2015) Image compression and encryption scheme using fractal dictionary and Julia set. IET Image Proc 9(3):173–183
Belazi A, Abd El-Latif AA, Belghith S (2016) A novel image encryption scheme based on substitution-permutation network and chaos. Sig Process 128:155–170
Li J, Liu H (2013) Colour image encryption based on advanced encryption standard algorithm with two-dimensional chaotic map. IET Inf Secur 7(4):265–270
Hua Z, Zhou Y, Pun CM, Philip Chen CL (2015) 2D Sine Logistic modulation map for image encryption. Inf Sci 297:80–94
Cheddad A, Condell J, Curran K, McKevitt P (2010) Digital image steganography: survey and analysis of current methods. Sig Process 90(3):727–752
Tseng YC, Chen YY, Pan HK (2002) A secure data hiding scheme for binary images. IEEE Trans Commun 50(8):1227–1231
Zope-Chaudhari S, Venkatachalam P, Buddhiraju KM (2015) Secure dissemination and protection of multispectral images using crypto-watermarking. IEEE J Select Topics Appl Earth Observations Remote Sens 8(11):5388–5394
Philip A (2013) A generalized pseudo-knight? s tour algorithm for encryption of an image. IEEE Potentials 32(6):10–16
Yang M, Bourbakis N, Li S (2004) Data-image-video encryption. IEEE Potentials 23(3):28–34
Wu X, Wang D, Kurths J, Kan H (2016) A novel lossless color image encryption scheme using 2D DWT and 6D hyperchaotic system. Inf Sci 349–350:137–153
Sudharsanan S (2005) Shared key encryption of JPEG color images. IEEE Trans Consum Electron 51(4):1204–1211
Zhang X, Li W, Hu H, Dutta NK (2015) High-speed all-optical encryption and decryption based on two-photon absorption in semiconductor optical amplifiers. IEEE/OSA J Opt Commun Netw 7(4):276–285
Wagh AM, Todmal SR (2015) Eyelids, eyelashes detection algorithm and Hough transform method for noise removal in iris recognition. Int J Comput Appl 112(3)
Sunil Kumar BS, Manjunath AS, Christopher S (2018) Improved entropy encoding for high efficient video coding standard. Alex Eng J 57(1):1–9
Kota PN, Gaikwad AN (2017) Optimized scrambling sequence to reduce papr in space frequency block codes based MIMO-OFDM system. J Adv Res Dyn Control Syst 502–525
Bhatnagar K, Gupta S (2017) Extending the neural model to study the impact of effective area of optical fiber on laser intensity. Int J Intell Eng Syst 10(4):274–283
Balaji GN, Subashini TS, Chidambaram N (2015) Detection of heart muscle damage from automated analysis of echocardiogram video. IETE J Res 61(3):236–243
Bramhe SS, Dalal A, Tajne D, Marotkar D (2015) Glass shaped antenna with defected ground structure for cognitive radio application. In: International Conference on Computing Communication Control and Automation, Pune, pp 330–333
Yarrapragada KSSR, Krishna BB (2017) Impact of tamanu oil-diesel blend on combustion, performance and emissions of diesel engine and its prediction methodology. J Braz Soc Mech Sci Eng 1–15
Sreedharan NPN, Ganesan B, Raveendran R, Sarala P, Dennis B, Boothalingam R (2018) Grey Wolf optimisation-based feature selection and classification for facial emotion recognition. IET Biometrics
Sarkar A, Murugan TS (2017) Cluster head selection for energy efficient and delay-less routing in wireless sensor network. Wireless Netw 1–18
Kumar M, Vaish A (2017) Encryption of color images using MSVD in DCST domain. Opt Lasers Eng 88:51–59
Hofbauer H, Uhl A (2016) Identifying deficits of visual security metrics for images. Sig Process Image Commun 46:60–75
Dang PP, Chau PM (2000) Image encryption for secure Internet multimedia applications. IEEE Trans Consum Electron 46(3):395–403
Satish K, Jayakar T, Tobin C, Madhavi K, Murali K (2004) Chaos based spread spectrum image steganography. IEEE Trans Consum Electron 50(2):587–590
Mirjalili S, Mirjalili SM, Lewis A (2014) Grey wolf optimizer. Adv Eng Softw 69:46–61
Iyapparaja M, Tiwari M (2017) Security policy speculation of user uploaded images on content sharing sites. IOP Conf Ser Mater Sci Eng 263(4):042019
Jain M, Lenka SK, Vasistha SK (2016) Adaptive circular queue image steganography with RSA cryptosystem. Perspect Sci 8:417–420
Sun S (2016) A novel edge based image steganography with 2 k correction and Huffman encoding. Inf Process Lett 116(2):93–99
Zhang D, Zhang F (2014) Chaotic encryption and decryption of JPEG image. Optik Int Light Electron Opt 125(2):717–720
Ye G, Huang X (2016) An image encryption algorithm based on autoblocking and electrocardiography. IEEE MultiMedia 23(2):64–71
Candido R, Soriano DC, Silva MTM, Eisencraft M (2015) Do chaos-based communication systems really transmit chaotic signals? Sig Process 108:412–420
Yang YG, Tian J, Lei H, Zhou YH, Shi WM (2016) Novel quantum image encryption using one-dimensional quantum cellular automata. Inf Sci 345:257–270
Liu Y et al (2016) Light encryption scheme using light-emitting diode and camera image sensor. IEEE Photon J 8(1):1–7
Wu HC, Wu NI, Tsai CS, Hwang MS (2005) Image steganographic scheme based on pixel-value differencing and LSB replacement methods. IEEE Proc Vis Image Signal Process 152(5):611–615
Dzwonkowski M, Papaj M, Rykaczewski R (2015) A new quaternion-based encryption method for DICOM images. IEEE Trans Image Process 24(11):4614–4622
Ge A, Zhang J, Zhang R, Ma C, Zhang Z (2013) Security analysis of a privacy-preserving decentralized key-policy attribute-based encryption scheme. IEEE Trans Parallel Distrib Syst 24(11):2319–2321
Zhang Y, Zhang LY (2015) Exploiting random convolution and random subsampling for image encryption and compression. Electron Lett 51(20):1572–1574
Jolfaei A, Wu XW, Muthukkumarasamy V (2016) On the security of permutation-only image encryption schemes. IEEE Trans Inf Forensics Secur 11(2):235–246
Elshamy AM et al (2013) Optical image encryption based on chaotic baker map and double random phase encoding. J Lightwave Technol 31(15):2533–2539
Cheng H, Li X (2000) Partial encryption of compressed images and videos. IEEE Trans Signal Process 48(8):2439–2451
Abd-El-Hafiz SK, Radwan AG, Abdel Haleem SH, Barakat ML (2014) A fractal-based image encryption system. IET Image Proc 8(12):742–752
Zhou J, Liu X, Au OC, Tang YY (2014) Designing an efficient image encryption-then-compression system via prediction error clustering and random permutation. IEEE Trans Inf Forensics Secur 9(1):39–50
Abdullah AH, Enayatifar R, Leeb M (2012) A hybrid genetic algorithm and chaotic function model for image encryption. Int J Electron Commun (AEU) 66:806–816
Enayatifar R, Abdullah AH, FauziIsnin I (2014) Chaos-based image encryption using a hybrid genetic algorithm and aDNAsequence. Opt Lasers Eng 56:83–93
Wang X, Xu D (2014) Image encryption using genetic operators and intertwining logistic map. Nonlinear Dyn 78(4):2975–2984
Pareek NK, Patidar V (2016) Medical image protection using genetic algorithm operations. Soft Comput 20(2):763–772
Das S, Mandal S, Ghoshal N (2015) Multiple-image encryption using genetic algorithm. Intell Comput Appl 343:145–153
Shankar K, Eswaran P (2016) An efficient image encryption technique based on optimized key generation in ECC using genetic algorithm. Artif Intell Evol Comput Eng Syst 394:705–714
Su Y, Tang C, Chen X, Li B, Xu W, Lei Z (2017) Cascaded Fresnel holographic image encryption scheme based on a constrained optimization algorithm and Henon map. Opt Lasers Eng 88:20–27
Zhang W, Wang H, Hou D, Yu N (2016) Reversible data hiding in encrypted images by reversible image transformation. IEEE Trans Multimed 18(8):1469–1479
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Koppu, S., Viswanatham, V.M. Medical image security enhancement using two dimensional chaotic mapping optimized by self-adaptive grey wolf algorithm. Evol. Intel. 11, 53–71 (2018). https://doi.org/10.1007/s12065-018-0159-z
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12065-018-0159-z