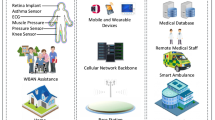
Abstract
Wireless body area network (WBAN) is an excellent platform to transfer crucial health data from a human body to the database over a public channel. Thus, it is essential to protect sensitive data, as an adversary can intercept communications. Besides, it is also vital to verify the user (sender and receiver) before providing data access for health information. To deal with these challenges, different message transmission protocols are designed to check the user legitimacy, data correctness, and secrecy of information. The Big data-Driven futuristic Fabric System(B- FFS) databases contain a lot of user data. B FFS is grouped into three categories: data collecting, data gathering, and error checking. By collecting useful user data from multiple sources, a smart B FFS enhances the business decision support process. The data comes from a variety of ways, including sensors that collect traffic, health, weather, and transfer data, as well as updates to various social networking sites. Researchers in this work have suggested different data transmission schemes for WBAN to enhance security while exchanging messages. They have discussed various features, limitations, and constructions of existing WBAN data transmission mechanisms to clearly understand the strengths and weaknesses of the existing work. To make it more clearly to readers, researchers in this study have described different essential security properties for WBAN communication. In addition, researchers have explained various security attacks, which can be launched during message transmission in WBAN. Moreover, possible countermeasures are discussed to resist the discussed attacks. Finally, while dealing with the WBAN system, this survey study presents a comprehensive discussion of the security properties, attacks, and countermeasures. Finally, this work aids researchers in developing WBAN data transfer techniques.











Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.References
Movassaghi S, Abolhasan M, Lipman J, Smith D, Jamalipour A (2014) Wireless body area networks: A survey. IEEE Commun Surv tutorials 16(3):1658–1686 Institute of Electrical and Electronics Engineers (IEEE). https://doi.org/10.1109/surv.2013.121313.00064
Chen M, Gonzalez S, Vasilakos A, Cao H, Leung VC (2011) Body area networks: A survey. Mob networks Appl 16(2):171–193
Latre B, Braem B, Moerman I, Blondia C, Demeester P (2011) A survey on wireless body area networks. Wireless Netw 17(1):1–18
Cao H, Leung V, Chow C, Chan H (2009) Enabling technologies for wireless body area networks: A survey and outlook. IEEE Commun Mag 47(12):84–93
Kwak KS, Ullah S, Ullah N (2010), November An overview of IEEE 802.15. 6 standard. In 2010 3rd International Symposium on Applied Sciences in Biomedical and Communication Technologies (ISABEL 2010) (pp. 1–6). IEEE
Toorani M (2015) On vulnerabilities of the security association in the IEEE 802.15. 6 standard. In International Conference on Financial Cryptography and Data Security (pp. 245–260). Springer, Berlin, Heidelberg
Ullah S, Higgins H, Braem B, Latre B, Blondia C, Moerman I, Saleem S, Rahman Z, Kwak KS (2012) A comprehensive survey of wireless body area networks. J Med Syst 36(3):1065–1094
Patel M, Wang J (2010) Applications, challenges, and prospective in emerging body area networking technologies. IEEE Wirel Commun 17(1):80–88
Negra R, Jemili I, Belghith A (2016) Wireless body area networks: Applications and technologies. Procedia Comput Sci 83:1274–1281
Islam SR, Kwak D, Kabir MH, Hossain M, Kwak KS (2015) The internet of things for health care: a comprehensive survey. IEEE Access 3:678–708
Bradai N, Fourati LC, Kamoun L (2015) WBAN data scheduling and aggregation under WBAN/WLAN healthcare network. Ad Hoc Netw 25:251–262
Bhanumathi V, Sangeetha CP (2017) A guide for the selection of routing protocols in WBAN for healthcare applications. Human-centric Comput Inform Sci 7(1):24
Yessad N, Omar M, Tari A, Bouabdallah A (2018) QoS-based routing in Wireless Body Area Networks: A survey and taxonomy. Computing 100(3):245–275
Seyedi M, Kibret B, Lai DT, Faulkner M (2013) A survey on intrabody communications for body area network applications. IEEE Trans Biomed Eng 60(8):2067–2079
Tobon DP, Falk TH, Maier M (2013) Context awareness in WBANs: a survey on medical and non-medical applications. IEEE Wirel Commun 20(4):30–37
Chakraborty C, Gupta B, Ghosh SK (2013) A review on telemedicine based WBAN framework for patient monitoring. Telemedicine and e-Health 19(8):619–626
Cavallari R, Martelli F, Rosini R, Buratti C, Verdone R (2014) A survey on wireless body area networks: Technologies and design challenges. IEEE Commun Surv Tutorials 16(3):1635–1657
Meharouech A, Elias J, Mehaoua A (2015) Future body-to-body networks for ubiquitous healthcare: a survey, taxonomy and challenges. In 2015 2nd International Symposium on Future Information and Communication Technologies for Ubiquitous HealthCare (Ubi-HealthTech) (pp. 1–6). IEEE
Salayma M, Al-Dubai A, Romdhani I, Nasser Y (2017) Wireless Body Area Network (WBAN) A Survey on Reliability, Fault Tolerance, and Technologies Coexistence. ACM Comput Surv (CSUR) 50(1):1–38
Li M, Lou W, Ren K (2010) Data security and privacy in wireless body area networks. IEEE Wirel Commun 17(1):51–58
Al Ameen M, Liu J, Kwak K (2012) Security and privacy issues in wireless sensor networks for healthcare applications. J Med Syst 36(1):93–101
Hayajneh T, Almashaqbeh G, Ullah S, Vasilakos AV (2014) A survey of wireless technologies coexistence in WBAN: analysis and open research issues. Wireless Netw 20(8):2165–2199
Mainanwal V, Gupta M, Upadhayay SK (2015) A survey on wireless body area network: Security technology and its design methodology issue. In 2015 international conference on innovations in information, embedded and communication systems (ICIIECS) (pp. 1–5). IEEE
Chin CA, Crosby GV, Ghosh T, Murimi R (2012) Advances and challenges of wireless body area networks for healthcare applications. In 2012 International Conference on Computing, Networking and Communications (ICNC) (pp. 99–103). IEEE
Ali A, Khan FA (2015) Key agreement schemes in wireless body area networks: Taxonomy and state-of-the-Art. J Med Syst 39(10):115
Masdari M, Ahmadzadeh S, Bidaki M (2017) Key management in wireless body area network: Challenges and issues. J Netw Comput Appl 91:36–51
Al-Janabi S, Al-Shourbaji I, Shojafar M, Shamshirband S (2017) Survey of main challenges (security and privacy) in wireless body area networks for healthcare applications. Egypt Inf J 18(2):113–122
Barakah DM, Ammad-uddin M (2012) A survey of challenges and applications of wireless body area network (WBAN) and role of a virtual doctor server in existing architecture. In 2012 Third International Conference on Intelligent Systems Modelling and Simulation (pp. 214–219). IEEE
Ghamari M, Janko B, Sherratt RS, Harwin W, Piechockic R, Soltanpur C (2016) A survey on wireless body area networks for ehealthcare systems in residential environments. Sensors 16(6):831
Javadi SS, Razzaque MA (2013) Security and privacy in wireless body area networks for health care applications. Wireless networks and security. Springer, Berlin, Heidelberg, pp 165–187
Touati F, Tabish R (2013) U-healthcare system: State-of-the-art review and challenges. J Med Syst 37(3):9949
Singh DK, Kaushik P (2018) Framework for fuzzy rule based automatic intrusion response selection system (frairss) using fuzzy analytic hierarchy process and fuzzy topsis. J Intell Fuzzy Syst 35(2):2559–2571
Singh DK, Kaushik P (2019) Intrusion response prioritization based on fuzzy ELECTRE multiple criteria decision-making technique. J Inform Secur Appl 48:102359
Antonescu B, Basagni S (2013) Wireless body area networks: challenges, trends and emerging technologies. In Proceedings of the 8th international conference on body area networks (pp. 1–7)
Poon CC, Zhang YT, Bao SD (2006) A novel biometrics method to secure wireless body area sensor networks for telemedicine and m-health. IEEE Commun Mag 44(4):73–81
Singh K, Muthukkumarasamy V (2007) Authenticated key establishment protocols for a home health care system. In Intelligent Sensors, Sensor Networks and Information, 2007. ISSNIP 2007. 3rd International Conference on (pp. 353–358). IEEE
Venkatasubramanian KK, Banerjee A, Gupta SKS (2010) PSKA: Usable and secure key agreement scheme for body area networks. IEEE Trans Inf Technol Biomed 14(1):60–68
Venkatasubramanian KK, Gupta SK (2010) Physiological value-based efficient usable security solutions for body sensor networks. ACM Trans Sens Networks (TOSN) 6(4):31
Shi L, Li M, Yu S, Yuan J (2013) BANA: body area network authentication exploiting channel characteristics. IEEE J Sel Areas Commun 31(9):1803–1816
Shi L, Yuan J, Yu S, Li M (2013) ASK-BAN: authenticated secret key extraction utilizing channel characteristics for body area networks. In Proceedings of the sixth ACM conference on Security and privacy in wireless and mobile networks (pp. 155–166). ACM
Liu J, Zhang Z, Chen X, Kwak KS (2014) Certificateless remote anonymous authentication schemes for wireless body area networks. IEEE Trans Parallel Distrib Syst 25(2):332–342
He D, Zeadally S, Kumar N, Lee JH (2016) Anonymous authentication for wireless body area networks with provable security. IEEE Syst J 11(4):2590–2601
Liu J, Zhang L, Sun R (2016) 1-RAAP: An efficient 1-round anonymous authentication protocol for wireless body area networks. Sensors 16(5):728
Li X, Peng J, Kumari S, Wu F, Karuppiah M, Choo KKR (2017) An enhanced 1-round authentication protocol for wireless body area networks with user anonymity. Comput Electr Eng 61:238–249
Li X, Ibrahim MH, Kumari S, Sangaiah AK, Gupta V, Choo KKR (2017) Anonymous mutual authentication and key agreement scheme for wearable sensors in wireless body area networks. Comput Netw 129:429–443
Bilal M, Shahid S, Khan Y, Rauf Z, Wagan RA, Butt MA, Khonina SN, Kazanskiy NL (2022) A Miniaturized FSS-Based Eight-Element MIMO Antenna Array for Off/On-Body WBAN Telemetry Applications. In Electronics. MDPI AG 11(4):522. https://doi.org/10.3390/electronics11040522
Boga J, & V., D. K (2022) Human activity recognition in WBAN using ensemble model. Int J Pervasive Comput Commun Emerald. https://doi.org/10.1108/ijpcc-12-2021-0314
Koya AM, Deepthi PP (2018) Anonymous hybrid mutual authentication and key agreement scheme for wireless body area network. Comput Netw 140:138–151
Kompara M, Islam SH, Holbl M (2019) A robust and efficient mutual authentication and key agreement scheme with untraceability for WBANs. Comput Netw 148:196–213
Sowjanya K, Dasgupta M, Ray S (2020) An elliptic curve cryptography based enhanced anonymous authentication protocol for wearable health monitoring systems.International Journal of Information Security,1–18
Limbasiya T, Shivam S (2017) A two-factor key verification system focused on remote user for medical applications. Int J Crit Infrastruct 13(2–3):133–151
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Soni, M., Singh, D.K. New directions for security attacks, privacy, and malware detection in WBAN. Evol. Intel. 16, 1917–1934 (2023). https://doi.org/10.1007/s12065-022-00759-2
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12065-022-00759-2