Abstract
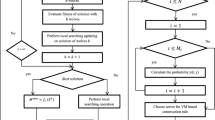
The problem of Virtual Machine (VM) placement is critical to the security and efficiency of the cloud infrastructure. Nowadays most research focuses on the influences caused by the deployed VM on the data center load, energy consumption, resource loss, etc. Few works consider the security and privacy issues of the tenant data on the VM. For instance, as the application of virtualization technology, the VM from different tenants may be placed on one physical host. Hence, attackers may steal secrets from other tenants by using the side-channel attack based on the shared physical resources, which will threat the data security of the tenants in the cloud computing. To address the above issues, this paper proposes an efficient and secure VM placement strategy. Firstly, we define the related security and efficiency indices in the cloud computing system. Then, we establish a multi-objective constraint optimization model for the VM placement considering the security and performance of the system, and find resolution towards this model based on the discrete firefly algorithm. The experimental results in OpenStack cloud platform indicates that the above strategy can effectively reduce the possibility of malicious tenants and targeted tenants on the same physical node, and reduce energy consumption and resource loss at the data center.










Similar content being viewed by others
References
Armbrust M, Fox A, Griffith R et al (2010) A view of cloud computing. Commun ACM 53(4):50–58
Kang C, Wei-Ming Z (2009) Cloud computing: system instances and current research. J Softw 20(5):1337–1348 (in Chinese)
The NIST Definition of Cloud Computing, http://csrc.nist.gov/publications/nistpubs/800-145/SP800-145.pdf, 2015, 9, 4
Ristenpart T (2009) Hey, you, get off of my cloud: exploring information leakage in third-party compute clouds. [C] CCS
Vattikonda B, Das S, Shacham H (2011) Eliminating fine grained timers in Xen. In: Proceedings of 3rd ACM workshop on cloud computing security workshop (CCSW 2011), pp 41–46
Wu J, Ding L, Lin Y, Min Allah N, Wang Y (2012) XenPump: a new method to mitigate timing channel in cloud computing. In: Proceedings of 5th IEEE international conference on cloud computing (CLOUD 2012), pp 678–685
Aviram A, Hu S, Ford B, Gummadi R (2010) Determinating timing channels in compute clouds. In: Proceedings of ACM workshop on cloud computing security workshop, pp 103–108
Shi J, Song X, Chen H, Zang B. (2011) Limiting cache-based side-channel in multi-tenant cloud using dynamic page coloring. In: Proceedings of 41st annual IEEE/IFIP international conference on dependable systems and networks workshops (DSN-W 2011), pp 194–199
Keller K, Szefer J, Rexford J, Lee RB (2010) NoHype: virtualized cloud infrastructure without the virtualization. In: Proceedings of 37th international symposium on computer architecture (ISCA’ 10). Saint-Malo, pp 350–361
Szefer J, Keller E, Lee RB, Rexford J (2011) Eliminating the hypervisor attack surface for a more secure cloud. In: Proceedings of 18th ACM conference on computer and communications security (CCS’ 11). Chicago, pp 401–412
Coffman J, Garey MR, Johnson DS (1997) Approximation algorithms for bin packing: a survey. Approximation algorithms for Np-Hard problems. PWS Publishing, Boston, pp 46–93
Shieh A, Kandula S, Greenberg A, Kim C (2010) Seawall, performance isolation for cloud datacenter networks. In: Proceedings 2nd USENIX conference on hot topics in cloud computing (HotCloud’ 10). Boston, pp 1–1
Raj H, Nathuji R, Singh A, England P (2009) Resource management for isolation enhanced cloud services. In: Proceedings of ACM workshop on cloud computing security (CCSW’ 09). Chicago, pp 77–84
Gupta D, Cherkasova L, Gardner R, Vahdat A (2006) Enforcing performance isolation across virtual machines in Xen. In: Proceedings of ACM/IFIP/USENIX international conference on middleware (Middleware’ 06). Melbourne, pp 342–362
Garfinkel T, Pfaff B, Chow J, Rosenblum M, Boneh D (2003) Terra: a virtual machine-based platform for trusted computing. In: Proceedings of 19th ACM symposium on operating systems principles (SOSP’ 03). Bolton Landing, pp 193–206
Sailer R, Jaeger T, Valdez E, Caceres R, Perez R, Berger S, Griffin J L (2005) Building a MAC-based security architecture for the Xen open-source hypervisor. In: Proceedings of the 21st annual computer security applications conferences. Tucson, pp 276– 285
Han Y, Chan J, Alpcan T, Leckie C (2014) Virtual machine allocation policies against co-resident attacks in cloud computing. In: Proceedings IEEE international conference on communications (ICC 2014), pp 786–792
Han Y, Chan J, Alpcan T, Leckie C (2015) Using virtual machine allocation policies to defend against co-resident attacks in cloud computing. Proc IEEE Trans Dependable Secure Comput
Dian S (2012) Research and implementation of virtual machine security placement mechanism in cloud computing. [D]. South East University, Nan Jing
Beloglazov A, Abawajy J, Buyya R (2012) Energy-aware resource allocation heuristics for efficient management of data centers for cloud computing. Futur Gener Comput Syst 28(5):755– 768
Mao-Lin T, Shen-chen P (2015) A hybrid genetic algorithm for the energy-efficient virtual machine placement problem in data centers. Neural Process Lett 41(2):211–221
Jamali S, Malektaji S (2014) Improving grouping genetic algorithm for virtual machine placement in cloud data centers. In: Proceedings of 4th international conference on computer and knowledge engineering (ICCKE). Mashhad, pp 328– 333
Liu C, Chen-Yang S, Si-Tian L et al (2014) A new evolutionary multi-objective algorithm to virtual machine placement in virtualized data center. In: Proceedings of 5th IEEE international conference on software engineering and service science (ICSESS). Beijing, pp 272–275
Hendtlass T, Moser I, Randall M. (2009) Dynamic problems and nature inspired meta-heuristics. Springer, Heidelberg
Yong-Qiang G, Hai-Bing G, Zheng-Wei Q et al (2013) A multi-objective ant colony system algorithm for virtual machine placement in cloud computing. J Comput Syst Sci 79(8):1230– 1242
Xu B, Zhi-Ping P, Fang-Xiong X et al (2015) Dynamic deployment of virtual machines in cloud computing using multi-objective optimization. Soft Comput 19(8):2265–2273
Jian-Kang D, Hong-Bo W, Yang-Yang L et al (2014) Virtual machine placement optimizing to improve network performance in cloud data centers. J China Univ Posts Telecommun 21(3):62–70
Yang XS (2008) Nature-inspired metaheuristic algorithms. Luniver Press, UK
Yang XS (2009) Firefly algorithms for multimodal optimization [C]//International Symposium on Stochastic Algorithms. Springer, Berlin Heidelberg, pp 169–178
Yang X-S (2010) Nature-inspired metaheuristic algorithms, 2nd edn. Luniver Press, Frome
Yang XS, He X (2013) Firefly algorithm: recent advances and applications. Int J Swarm Intell 1(1):36–50. doi:10.1504/IJSI.2013.055801
Fan X, Weber WD, Barroso LA (2007) Power provisioning for a warehouse-sized computer. In: Proceedings of 34th annual international symposium on computer architecture. New York, pp 13–23
Hu L, Jin H, Liao X, et al. (2008) Magnet: a novel scheduling policy for power reduction in cluster with virtual machines. In: Proceedings of 2008 IEEE international conference on cluster computing. Tsukuba, pp 13–22
Augkulanon P, Chai-ead N, Luangpaiboon P (2011) Bees and firefly algorithms for noisy nonlinear optimisation problems[A]. In: The international multiconference of engineers and computer scientists, p 2
Marichelvam M K, Prabaharan T, Yang X-S (2014) A discrete firefly algorithm for the multi-objective hybrid flowshop scheduling problems. IEEE Trans Evol Comput 18(2):301– 305
Sayadi MK, Hafezalkotob A, Naini SGJ (2013) Firefly-inspired algorithm for discrete optimization problems: an application to manufacturing cell formation. J Manuf Syst 32(1):78– 84
Lu K, Sun J (2016) Convergence analysis of firefly algorithm. J Front Comput Sci Technol 10(02)
OpenStack, http://docs.openstack.org
Jansen R, Brenner PR (2011) Energy efficient virtual machine allocation in the coud: an analysis of cloud allocation policies. In: Proceedings of international green computing conference and workshops (IGCC 2011), pp 1–8
Acknowledgments
This work is supported by the National Natural Science Foundation of China (Grant NO. 61472139).
Author information
Authors and Affiliations
Corresponding author
Additional information
This work is supported by the National Natural Science Foundation of China (Grant NO.61472139).
Rights and permissions
About this article
Cite this article
Ding, W., Gu, C., Luo, F. et al. DFA-VMP: An efficient and secure virtual machine placement strategy under cloud environment. Peer-to-Peer Netw. Appl. 11, 318–333 (2018). https://doi.org/10.1007/s12083-016-0502-z
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12083-016-0502-z