Abstract
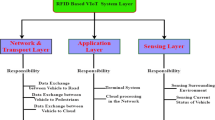
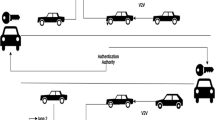
Transparent Computing (TC) has become a promising paradigm in the network computing era, the appearance of Transparent Computing have a real impact on the industry. A growing number of cars on the road, in order to reduce road congestion, improve efficiency, and increase travelers satisfaction, IoV (Internet of Vehicles) arises at the proper time. RFID as an excellent sensing equipment is widely used in the IoV. Tags can collect information separately. The surrounding readers transmit the information to the central processing unit by using the Transparent Computing technique. Data sharing is the premise of IoV, drivers can share their information, in the meantime, they do not want to expose their own privacy information, so anonymity and untraceability is very important. Unfortunately, current applicable or proposed protocols fail to satisfy the security, efficiency and usability. In this paper, we propose a mutual authentication protocol to protect driver’s privacy, TC is used in our protocol, so we can make full use of client hardware, improve the quality of user experience. The last but not least, because the existence of OS-level monitoring and attack tracing, system security increase greatly.




Similar content being viewed by others
Reference
Li L, Liu J, Yang Y (2012) Research and development of intelligent motor test system. Journal of Computers 7(9):2192–2199
Ying Lu, Wenqiang Chen, Xingmin Wei, Fuquan Zhao (2012) “On the application development of 3G technology in automobiles,” Proceedings of the FISITA 2012 World Automotive Congress, 311–325
Liu W (2012) Research on cloud computing security problem and strategy. Proceedings of CECNet 2012:1216–1219
Z. Wei, Y. Zhang, and J. Yang (2013) “Private assets protection system based on RFID and cloud computing,” Proceedings of CECNet ‘13, 196–198
Li T (2005) An immunity based network security risk estimation. Science in China 48(5):557–578
Shi H, Bai X, Ren C, Zhao C (1848-1853) Development of internet of Vehicle's information system based on cloud. Journal of Software 9(7):2014
Y. C. Lee, Y. C. Hsieh, P. S. You, et al (2009) “A new ultra-lightweight RFID protocol with mutual authentication,” Proceedings of Information Engineering-volume, 58–61
Catteddu D (2010) Cloud computing: benefits, risks and recommendations for information security. Web Application Security:17–17
Auto-ID Center (2002) “860MHz–960MHz Class I radio frequency identification tag radio frequency & logical communication interface specification proposed recommendation Version 1.0.0,” Technical Report MIT-AUTOID-TR-007
Lee S-M, Hwang YJ, Lee DH, Lim JI (2005) Efficient authentication for low-cost RFID systems. Proceedings of ICCSA 2005:619–627
Lee S, Asano T, Kim K (2006) RFID mutual authentication scheme based on synchronized secret information. Proceedings of SCIS 2006:98–98
Gildas Avoine and Philippe Oechslin (2005) “RFID traceability: a mulilayer problem,” Proceedings of Financial Cryptography-FC, 125–140
T. Li and G. Wang (2007) “Security analysis of two ultralightweight RFID authentication protocols,” Proceedings of the 22nd IFIP TC-11 International Information Security Conference, pp. 109–120
P. Peris-Lopez, J. C. Hernandez-Castro, J. M. Estevez-Tapiador, and A. Ribagorda (2006) “LMAP: a real Lightweight mutual authentication protocol for low-cost RFID tags,” Proceedings of RFID’06
P. Peris-Lopez, J. C. Hernandez-Castro, J. M. Estevez-Tapiador, and A. Ribagorda (2006) “EMAP: an efficient mutual authentication protocol for low cost RFID tags”, Proceedings of IS’06, 352–361
Y. Zhou (2012) “Transparent computing: From concept to implementation,” Proceedings of Information Technology in Medicine and Education, 5–5
Zhang Y, Zhou Y (2012) Trans OS: a transparent computing-based operating system for the cloud. International Journal of Cloud Computing 1(4):287–301
Y. Zhang, Y. Zhou (2006) “Transparent computing: a new paradigm for pervasive computing,” Proceedings of Ubiquitous Intelligence and Computing, pp. 1–11
Huang S, Wu M, Xiong Y (2014) Mobile transparent computing to enable ubiquitous operating systems and applications. Journal of Advanced Computational Intelligence & Intelligent Informatics 18(1):32–39
Zhang Y, Yang L, Zhou Y et al (2010) Information security underlying transparent computing: impacts, visions and challenges. Web Intelligence & Agent Systems 8(2):203–217
G. Li, P. Yang, H. Zhang (2015) “Application of internet of vehicle (IoV) in the Smart City,” Office Informatization
Gebremeskel G, Chai Y, Yang Z (2014) The paradigm of big data for augmenting internet of vehicle into the intelligent cloud computing systems. Internet of Vehicles – Technologies and Services 247-261. doi:10.1007/978-3-319-11167-4_25
H. Lin, X. Huang (2014) “Survey on internet of vehicle technology,” Journal of Mechanical & Electrical Engineering
Duan X, Wang X, Duan X et al (2012) Design of school bus safety regulation system based on the internet of vehicle technology. Applied Mechanics & Materials 263:2911–2914
Xie W, Xie L, Zhang C et al (2013) Cloud-based RFID authentication. Proceedings of RFID 2013:168–175
Lin I, Hsu H, Cheng C (2015) A cloud-based authentication protocol for RFID supply chain systems. Journal of Network & Systems Management 23(4):978–997
Fan K, Li J, Li H, Liang X, Shen X, Yang Y (2014) RSEL: revocable secure efficient lightweight RFID authentication scheme. Concurrency and Computation: Practice and Experience 26(5):1084–1096
Li H, Lin X, Yang H, Liang X, Lu R, Shen X (2053-2064) EPPDR: an efficient privacy-preserving demand response scheme with adaptive key evolution in smart grid. IEEE Transactions on Parallel and Distributed Systems 25(8):2014
Chu L, Wu S (2011) An integrated building fire evacuation system with RFID and cloud computing. Proceedings of IIHMSP 2011:17–20
Fan K, Gong Y, Liang C, Li H, Yang Y (2015) Lightweight and ultralightweight RFID mutual authentication protocol with cache in the reader for IoT in 5G. Security and Communication Networks. doi:10.1002/sec.1314
Ma D, Prasad A (2011) A context-aware approach for enhanced security and privacy in RFID electronic toll collection systems. Proceedings of ICCCN 2011:1–6
S. Abughazalah, K. Markantonakis, K. Mayes (2015) “Secure improved cloud-based RFID authentication protocol”. Data Privacy Management, Autonomous Spontaneous Security, and Security Assurance, 147–164. doi:10.1007/978-3-319-17016-9_10
Bhaskar P, Ahamed S (2007) Privacy in pervasive computing and open issues. Proceedings of Ares 2007:147–154
Li H, Liu D, Dai Y, Luan T (2015) Engineering searchable encryption of mobile cloud networks: when QoE meets QoP. IEEE Wirel Commun 22(4):74–80
Li H, Yang Y, Luan T, Liang X, Zhou L, Shen X (2016) Enabling fine-grained multi-keyword search supporting classified sub-dictionaries over encrypted cloud data. IEEE Transactions on Dependable and Secure Computing 13(3):312–325
Chien H, Chen C (2007) Mutual authentication protocol for RFID conforming to EPC class 1 generation 2 standards. Computer Standards and Interfaces 29:254–259
Tan C et al (2008) Secure and serverless RFID authentication and search protocols. IEEE Trans Wirel Commun 7:1400–1407
Z. Shen, Sh. Liu, (2012) “Security threats and security policy in wireless sensor networks,” Advances in Information Sciences & Service Sciences, 4, 10, 166.
Acknowledgements
This work has been financially supported by the National Natural Science Foundation of China (No. 61303216, No. 61272457, No. U1401251, and No. 61373172), the National High Technology Research and Development Program of China (863 Program) (No. 2012AA013102), and National 111 Program of China B16037 and B08038.
Author information
Authors and Affiliations
Corresponding author
Additional information
This article is part of the Topical Collection: Special Issue on Transparent Computing
Guest Editors: Jiannong Cao, Jingde Cheng, Jianhua Ma, and Ju Ren
Rights and permissions
About this article
Cite this article
Fan, K., Wang, W., Jiang, W. et al. Secure ultra-lightweight RFID mutual authentication protocol based on transparent computing for IoV. Peer-to-Peer Netw. Appl. 11, 723–734 (2018). https://doi.org/10.1007/s12083-017-0553-9
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12083-017-0553-9