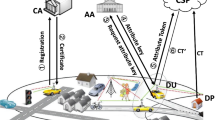
Abstract
With the rapid development of vehicular networks, the problem of data sharing in vehicular networks has attached much attention. However, existing data access control schemes in cloud computing cannot be applied to the scenario of vehicular networks, because cloud computing paradigm cannot satisfy the rigorous requirement posed by latency-sensitive mobile application. Fog Computing is a paradigm that extends Cloud computing and services to the edge of the network. The vehicular fog is the ideal platform to achieve data sharing in vehicular networks. In this paper, we propose a revocable data sharing scheme for vehicular fogs. We construct a new multi-authority ciphertext policy attribute-based encryption (CP-ABE) scheme with efficient decryption to realize data access control in vehicular network system, and design an efficient user and attribute revocation method for it. The analysis and the simulation results show that our scheme is secure and highly efficient.





Similar content being viewed by others
References
Zhu H, Chang S, Lu L, Zhang W (2016) RUPS: fixing relative distances among urban vehicles with context-aware trajectories. Proceedings of IPDPS 2016:123–131
Zhu H, Chang S, Li M, Naik K, Shen S (2011) Exploiting temporal dependency for opportunistic forwarding in urban vehicular networks. Proceedings of INFOCOM 2011:2192–2200
Gerla M, Kleinrock L (2011) Vehicular networks and the future of the mobile internet. Comput Netw 55(2):457–469
Luan T, Shen X, Bai F (2013, 2013) Integrity-oriented content transmission in highway vehicular ad hoc networks. Proceedings of INFOCOM:2562–2570
Fernando N, Loke S, Rahayu W (2013) Mobile cloud computing: a survey. Futur Gener Comput Syst 29(1):84–106
Tuli A, Hasteer N, Sharma M, Bansal A (2013) Exploring challenges in mobile cloud computing: An overview. Proceedings of Next Generation Information Technology Summit 2013:496–501
Bonomi F (2011) Connected vehicles, the internet of things, and fog computing. VANET 2011:13–15
Bonomi F, Milito R, Zhu J, Addepalli S (2012, 2012) Fog computing and its role in the internet of things. Proceedings of MCC:13–16
Aazam M, Huh E (2014) Fog computing and smart gateway based communication for cloud of things. Proceedings of FiCloud 2014:464–470
Aazam M, Huh E (2015) E-HAMC: leveraging fog computing for emergency alert service. Proceedings of PerCom 2015:518–523
Hong K, Lillethun D, Ramachandran U, Ottenwälder B, Koldehofe B (2013) Mobile fog: a programming model for large-scale applicationson the internet of things. Proceedings of MCC 2013:15–20
Ottenwalder B, Koldehofe B, Rothermel K, Ramachandran U (2013) Migcep: Operator migration for mobility driven distributed complexevent processing. Proceedings of DEBS 2013:183–194
Nishio T, Shinkuma R, Takahashi T, Mandayam N (2013) Service oriented heterogeneous resource sharing for optimizing service latency in mobile cloud. Proceedings of MobileCloud 2013:19–26
Dong M, Liu X, Qian Z, Liu A, Wang T (2015) QoE-ensured price competition model for emerging mobile networks. IEEE Wirel Commun 22(4):50–57
Wei K, Dong M, Ota K et al (2015) CAMF. Context-aware message forwarding in mobile social networks. IEEE Transactions on Parallel and Distributed Systems 26(8):2178–2187
Luo S, Dong M, Ota K et al (2015) A security assessment mechanism for software-defined networking-based mobile networks. Sensors 15(12):31843–31858
Ota K, Dong M, Chang S et al (2015) MMCD: cooperative downloading for highway VANETs. IEEE Trans Emerging Topics Comput 3(1):34–43
Ostrovsky R, Sahai A, Waters B (2007, 2007) Attribute-based encryption with non-monotonic access structures. Proceedings of CCS:195–203
Rafaeli S, Hutchison D (2003) A survey of key management for secure group communication. ACM Comput Surv 35(3):309–329
Boyen X, Waters B (2007, 2007) Full-domain subgroup hiding and constant-size group signatures. Proceedings of PKC:1–15
Liang X, Lu R, Lin X, Shen X (2010) Ciphertext policy attribute-based encryption with efficient revocation. IEEE symposium on security and privacy. Pp 321-334
Xie X, Ma H, Li J, Chen X (2013) New ciphertext-policy attribute-based access control with efficient revocation. Proceedings of ICT 2013:373–382
Hur J, Noh D (2010) Attribute-based access control with efficient revocation in data outsourcing systems. IEEE Transactions on Paralleland Distributed Systems 22(7):1214–1221
Beimel A (1996) Secure schemes for secret sharing and key distribution. Technion-Israel Institute of Technology, Faculty of Computer Science. pp 22–28
Dong M, Zheng L, Ota K, Guo S, Guo M, Li L (2009) A trade-off approach to optimal resource allocation algorithm with cache technology in ubiquitous computing environment. Proceedings of CSE 2009. Pp 9-15
Chang S, Qi Y, Zhu H et al (2012) Footprint: detecting Sybil attacks in urban vehicular networks. IEEE Transactions on Parallel & Distributed Systems 23(6):1103–1114
Stojmenovic I, Sheng W (2014, 2014) The fog computing paradigm: scenariosand security issues. Proceedings of FedCSIS:1–8
Chase M (2007) Multi-authority attribute based encryption. Proceedings of theory of cryptography. Pp 515-534
Lewko A, Waters B (2011, 2011) Decentralizing attribute-based encryption. Proceedings of advances in cryptology–EUROCRYPT:568–588
Ruj S, Nayak A, Stojmenovic I (2011) DACC: distributed access control in clouds. Proceedings of TrustCom 2011:91–98
Akinyele J, Garman C, Miers I et al (2013) Charm: a framework for rapidly prototyping cryptosystems. J Cryptogr Eng 3(2):111–128
Lynn B. PBC Library: The pairing-based cryptography library. http://crypto.stanford.edu/pbc. Accessed 26 Jul 2016
Charm: A tool for rapid cryptographic prototyping. http://www.charm-crypto.com. Accessed 26 Jul 2016
Acknowledgements
This work has been financially supported by the National Natural Science Foundation of China (No. 61303216, No. 61272457, No. U1401251, and No. 61373172), the National High Technology Research and Development Program of China (863 Program) (No. 2012AA013102), the Open Research Project of the State Key Laboratory of Industrial Control Technology, Zhejiang University, China (No. ICT170312), and National 111 Program of China B16037 and B08038.
Author information
Authors and Affiliations
Corresponding author
Additional information
This article is part of the Topical Collection: Special Issue on Fog Computing on Wheels
Guest Editors: Hongzi Zhu, Tom H. Luan, Mianxiong Dong, and Peng Cheng
Rights and permissions
About this article
Cite this article
Fan, K., Wang, J., Wang, X. et al. Secure, efficient and revocable data sharing scheme for vehicular fogs. Peer-to-Peer Netw. Appl. 11, 766–777 (2018). https://doi.org/10.1007/s12083-017-0562-8
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12083-017-0562-8