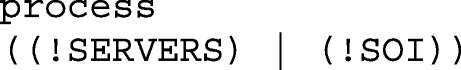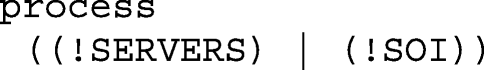Abstract
With the rapid advancement of heterogeneous wireless technologies and their proliferation in ambient connected objects, the Internet of Things (IoT) is a paradigm that revolutionizes communication between people/objects. Communication between connected objects is achieved via various communication modes, including Machine-to-Machine (M2M) and Machine-to-Cloud (M2C). In the medical field, monitoring devices help to collect, exchange and process patient health parameters, and are employed in open and unprotected environments, which expose them to various attacks. For this reason, providing high levels of security and privacy become crucial, and a first requirement to ensure this is authentication. In this paper, we propose three new lightweight, efficient authentication protocols for IoT-based healthcare applications. We formally verify them using AVISPA and ProVerif automated tools. For each protocol, we provide a security analysis and a performance evaluation that we compare to related existing proposals.











Similar content being viewed by others
References
Atzori L, Iera A, Morabito G (2017) Understanding the internet of things: definition, potentials, and societal role of a fast evolving paradigm. Ad Hoc Networks 56:122–140
Sathish Kumar J, Patel DR (2014) A survey on internet of things: security and privacy issues. Int J Comput Appl 90(11):20–26
Hail MA, Fischer S (2015) Iot for aal: an architecture via information-centric networking. In: Globecom workshops (GC Wkshps), 2015 IEEE. IEEE, pp 1–6
Sicari S, Rizzardi A, Grieco LA, Coen-Porisini A (2015) Security, privacy and trust in internet of things: the road ahead. Comput Netw 76:146–164
Lu R, Li X, Liang X, Shen X, Lin X (2011) Grs: the green, reliability, and security of emerging machine to machine communications. IEEE communications magazine 49(4):28–35
Saied YB, Olivereau A, Laurent M (2012) A distributed approach for secure m2m communications. In: 2012 5th international conference on new technologies, mobility and security (NTMS). IEEE, pp 1–7
Ren W, Yu L, Ma L, Ren Y (2013) Rise: a reliable and secure scheme for wireless machine to machine communications. Tsinghua Sci Technol 18(1):100–117
Domingo MC (2012) An overview of the internet of things for people with disabilities. J Netw Comput Appl 35(2):584–596
Porambage P, Braeken A, Gurtov A, Ylianttila M, Spinsante S (2015) Secure end-to-end communication for constrained devices in IoT-enabled ambient assisted living systems. In: IEEE 2nd world forum on internet of things (WF-IoT). IEEE, p 2015
Shamir A (1979) How to share a secret. Commun ACM 22(11):612–613
Nguyen KT, Oualha N, Laurent M (2016) Authenticated key agreement mediated by a proxy re-encryptor for the internet of things. In: European symposium on research in computer security. Springer, pp 339–358
Nuñez D, Agudo I, Lopez J (2016) Attacks to a proxy-mediated key agreement protocol based on symmetric encryption. IACR Cryptology ePrint Archive 2016:1081
Jin C, Xu C, Zhang X, Li F (2016) A secure ecc-based rfid mutual authentication protocol to enhance patient medication safety. J Med Syst 40(1):12
Zhao Z (2014) A secure rfid authentication protocol for healthcare environments using elliptic curve cryptosystem. J Med Syst 38(5):46
Alamr AA, Kausar F, Kim J, Seo C (2018) A secure ecc-based rfid mutual authentication protocol for internet of things. J Supercomput 74:4281–4294
Liao Y-P, Hsiao C-M (2013) A secure ecc-based rfid authentication scheme using hybrid protocols. In: Advances in intelligent systems and applications, vol 2. Springer, pp 1–13
Dinarvand N, Barati H (2019) An efficient and secure rfid authentication protocol using elliptic curve cryptography. Wirel Netw 25(1):415–428
Sharma D, Jinwala D (2015) Functional encryption in IoT e-health care system. In: International conference on information systems security. Springer, pp 345–363
Li R, Shen C, He H, Xu Z, Xu C-Z (2017) A lightweight secure data sharing scheme for mobile cloud computing. IEEE Transactions on Cloud Computing 6:344–357
Porambage P, Braeken A, Kumar P, Gurtov A, Ylianttila M (2015) Proxy-based end-to-end key establishment protocol for the internet of things. In: IEEE international conference on communication workshop (ICCW). IEEE, p 2015
Amin R, Hafizul Islam SK, Biswas GP, Khan MK, Kumar N (2018) A robust and anonymous patient monitoring system using wireless medical sensor networks. Futur Gener Comput Syst 80:483–495
Jiang Q, Ma J, Yang C, Ma X, Shen J, Chaudhry SA (2017) Efficient end-to-end authentication protocol for wearable health monitoring systems. Comput Electr Eng 63:182–195
Tuna G, Kogias DG, Cagri Gungor V, Gezer C, Takn E, Ayday E (2017) A survey on information security threats and solutions for machine to machine (m2m) communications. J Parallel Distrib Comput 109:142–154
Saadeh M, Sleit A, Qatawneh M, Almobaideen W (2016) Authentication techniques for the internet of things: a survey. In: 2016 cybersecurity and cyberforensics conference (CCC), pp 28–34
Ferrag MA, Maglaras LA, Janicke H, Jiang J, Shu L (2017) Authentication protocols for internet of things: a comprehensive survey. Security and Communication Networks, 2017
Dolev D, Yao A (1983) On the security of public key protocols. IEEE Trans Inf Theory 29(2):198–208
TA Team et al (2006) Avispa v1. 1 user manual. Information society technologies programme (June 2006), http://avispa-project.org
Blanchet B (2014) Automatic verification of security protocols in the symbolic model: the verifier proverif. In: Foundations of security analysis and design VII. Springer, pp 54–87
Bonnefoi P-F, Dusart P, Sauveron D, Akram RN, Markantonakis K (2015) A set of efficient privacy protection enforcing lightweight authentication protocols for low-cost rfid tags. In: Trustcom/BigDataSE/ISPA, 2015 IEEE, vol 1. IEEE, pp 612–620
Zhuang Y, Yang A, Hancke GP, Wong DS, Yang G (2018) Energy-efficient distance-bounding with residual charge computation. IEEE Trans Emerg Top Comput, pp 1–1
Ong H, Schnorr C-P, Shamir A (1984) An efficient signature scheme based on quadratic equations. In: Proceedings of the sixteenth annual ACM symposium on theory of computing. ACM, pp 208–216
MULTOS Limited (2019) Multos Trust Anchor. https://www.multos.com/trust_anchor. Online; accessed 20 May 2019
Universal Smart Cards Limited (2019) Universal JCard. http://www.universaljcard.com/. Online; accessed 20 May 2019
MULTOS Limited (2019) Multos consortium. https://www.multos.com/consortium. Online; accessed 20 May 2019
Infineon Technologies AG (2019) SLE 78CLUFX5000PH. https://www.infineon.com/cms/en/product/security-smart-card-solutions/security-controllers-for-usb-tokens/sle-78clufx5000ph/. Online; accessed 20 May 2019
Infineon Technologies AG (2019) SLE 78CLFX4000P. https://www.infineon.com/cms/en/product/security-smart-card-solutions/security-controllers/sle-78/sle-78clfx4000p/. Online; accessed 20 May 2019
Van haver P (2019) Unveiling Java Card 3.1: new I/O and trusted peripherals. https://blogs.oracle.com/javaiot/unveiling-java-card-31%3a-new-io-and-trusted-peripherals, November 2018. Online; accessed 20 May 2019
Oracle Inc (2019) Oracle Java Card boosts security for IoT devices at the edge. https://www.oracle.com/corporate/pressrelease/oracle-java-card-boosts-security-011619.html, January 2019. Online; accessed 20 May 2019
Oracle Inc. (2019) Java Card 3.1 documentation. https://docs.oracle.com/en/java/javacard/3.1/, January 2019. Online; accessed 20 May 2019
Infineon Technologies AG (2019) Integrity guard. https://www.infineon.com/dgdl/infineon-integrity_guard_the_smartest_digital_security_technology_in_the_industry_06.18-WP-v01_01-EN.pdf?fileid=5546d46255dd933d0155e31c46fa03fb, June 2018. Online; accessed 20 May 2019
Infineon Technologies AG (2019) SOLID FLASH chip card controllers. https://www.infineon.com/dgdl/infineon-SOLID_FLASH_chip_card_controllers-PB-v04_12-EN.pdf?fileid=5546d46255dd933d0155e31d0ac105d9, May 2012. Online; accessed 20 May 2019
MULTOS Limited (2019) Multos IoT Trust Anchor Developer Boards. https://www.multos.com/dev_boards. Online; accessed 20 May 2019
MULTOS Limited (2019) ML5-P22 and MC5-p22 on INFINEON SLE78 PLATFORM. https://www.multos.com/products/approved_platforms/MIR/multos_international/m5-p22, Online; accessed 20 May 2019
MULTOS Limited (2019) ML5-P19 and MC5-p19 on INFINEON SLE78 PLATFORM. https://www.multos.com/products/approved_platforms/MIR/multos_international/m5_p19. Online; accessed 20 May 2019
MULTOS Limited (2019) Smartdeck. https://www.multos.com/software, Online; accessed 20 May 2019
Oracle Inc. (2019) Java Card technology. https://www.oracle.com/technetwork/java/embedded/javacard/overview/index.html. Online; accessed 20 May 2019
Sauveron D (2009) Multiapplication smart card: towards an open smart card? Inf Secur Tech Rep 14(2):70–78. Smart Card Applications and Security
Infineon Technologies AG (2019) Java Card IDE. https://www.infineon.com/cms/en/product/promopages/devkit4ID/. Online; accessed 20 May 2019
Oracle Inc. (2019) Java Card Development Kit. https://www.oracle.com/technetwork/java/embedded/javacard/downloads/javacard-sdk-2043229.html. Online; accessed 20 May 2019
Acknowledgements
This work is supported by the ex-Région Limousin, under grant for project “IoTSec”, by the MIRES research federation under grants for projects “SCOPE”, “SPOCK” and “SPOCK2”, by the Région Nouvelle-Aquitaine under the grant for project “SVP-IoT” and by the ID-Fix project, an ANR funded project (ANR-16-CE39-0004).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This article is part of the Topical Collection: Special Issue on IoT System Technologies based on Quality of Experience
Guest Editors: Cho Jaeik, Naveen Chilamkurti, and SJ Wang
Appendix: AVISPA and ProVerif specifications for protocols
Appendix: AVISPA and ProVerif specifications for protocols
1.1 A.1 AVISPA
1.1.1 A.1.1 Jin et al.’s authentication protocol improvements
There are two basic roles, S and T, which explain the activity of Server and Ti.
There are two agents T, S and they both use a hash function H, a modular multiplication function MULT, a scalar multiplication function MECC, a modular addition function ADD, a points addition function ADDP and a curve generator P, and a smart object T identity Idt, its identity hash result HidT and server public key Ps, to compute the authentication message AUTHI and AUTHS.
Secrecy of identity of smart object T Idt, its identity hash result HidT, the server’s secret key Xs and secret random numbers Ri, Rs is modeled using the goal predicates secret(Idt, sec_idt, T), secret(Idt, sec_idt, S), secret(HidT, sec_hidt, T), secret(HidT, sec_hidt, S), secret (Xs, sec_xs , S), secret(Ri', sec_ri, T), secret(Rs', sec_rs, S) which are maintained by the protocol_id: sec_idt, sec_hidt, sec_xs, sec_ri and sec_rs respectively. The parameters Idt, HidT, Xs and Ri, Rs are kept secret to T and S.
Mutual authentication is achieved via witness and request goals, i.e. witness(T, S, auth_i, AUTHI'), request(S, T, auth_i, AUTHI'), witness(S, T, auth_s, AUTHS'), request(T, S, auth_s, AUTHS'). witness(T, S, auth_i, AUTHI') declares that agent T claims to be the peer of agent S, agreeing on the value AUTHI'. auth_i is the name of AUTHI' authentication shown in the goal section, whereas request(S, T, auth_i, AUTHI') declares that agent S accepts the value AUTHI' and now relies on the guarantee that agent T exists and agrees with it on this value.
The environment contains the global constants and the composition of one or more sessions. The intruder participates as a concrete session in the execution protocol.

1.1.2 A.1.2 Hash-based authentication protocol
There are two basic roles, S and T, which explain the activity of Server and Ti.
There are two agents T, S and they both use a hash function H, a scalar multiplication function MECC, a curve generator P, and a smart object T identity Idt and its identity hash result HidT respectively to compute the authentication message AUTHI and AUTHS.
Secrecy of identity of smart object T Idt, its identity hash result HidT and secret random numbers Ri, Rs are modeled using the goal predicates secret(Idt, sec_idt, T), secret(Idt, sec_idt, S), secret(HidT, sec_hidt, T), secret(HidT, sec_hidt, S), secret(Ri', sec_ri, T), secret(Rs', sec_rs, S) , which are maintained by the protocol_id: sec_idt, sec_hidt, sec_ri, sec_rs respectively. The parameters Idt, HidT and Ri, Rs are kept secret to T and S.
Mutual authentication is achieved via witness and request goals; i.e., witness(T, S, auth_i, AUTHI'), request(S, T, auth_i, AUTHI'), witness (S, T, auth_s, AUTHS'), request (T, S, auth_s, AUTHS'). witness(T, S, auth_i, AUTHI') declares that agent T claims to be the peer of agent S, agreeing on the value AUTHI'. auth_i is the name of AUTHI' authentication shown in the goal section whereas request(S, T, auth_i, AUTHI') declares that agent S accepts the value AUTHI' and now relies on the guarantee that agent T exists and agrees with it on this value.
The environment contains the global constants and the composition of one or more sessions. The intruder participates as a concrete session in the execution protocol.

1.1.3 A.1.3 ECC-based authentication protocol
There are two basic roles, A and B, which explain the activity of Ti and Tj nodes.
There are two agents A, B and they both use a hash function H, a modular multiplication function MULT, a scalar multiplication function MECC, a points addition function ADDP, an initialization function INITVAR and a curve generator P, server public key Ps, private/public keys Xa/Pa, Xb/Pb, and public key Schnorr signature (Ppa, Za), (Ppb, Zb) respectively to compute the authentication messages AUTHA and AUTHB.
Secrecy of private keys Xa, Xb and secret random numbers Ra, Rb is modeled using the goal predicates secret(Xa, sec_xa, A), secret(Xb, sec_ xb, B), secret(Ra', sec_ra, A), secret(Rb', sec_rb, B), which are maintained by the protocol_id: sec_xa, sec_xb, sec_ra, sec_rb respectively. The parameters (Xa, Ra) and (Xb, Rb) are kept secret to A and B respectively.
Mutual authentication is achieved via witness and request goals i.e. witness(A, B, auth_a, AUTHA'), request(B, A, auth_a, AUTHA'), witness(B, A, auth_b, AUTHB'), request(A, B, auth_b, AUTHB'). witness(A, B, auth_a, AUTHA') declares that agent A claims to be the peer of agent B, agreeing on the value AUTHA'. auth_a is the name of AUTHA' authentication shown in the goal section whereas request(B, A, auth_a, AUTHA') declares that agent B accepts the value AUTHA' and now relies on the guarantee that agent A exists and agrees with it on this value.
The environment contains the global constants and the composition of one or more sessions. The intruder participates as a concrete session in the execution protocol.

1.2 A.2 ProVerif
1.2.1 A.2.1 Applied Pi calculus specification script of Jin et al.’s authentication protocol improvements
Explanations of the applied pi calculus scripts are the following:
The secrets xs, idt and hidt are declared as secret to the attacker using the word [private]. ch is the public channel where SERVERS and SOI exchange their messages. The one-way hash function is modeled by H1, H2 and H3, for hashing one, two and three elements respectively. mult, mecc, add, addp, concat and xor represent modular multiplication, scalar multiplication, modular addition, points addition, concatenation and xor functions respectively.
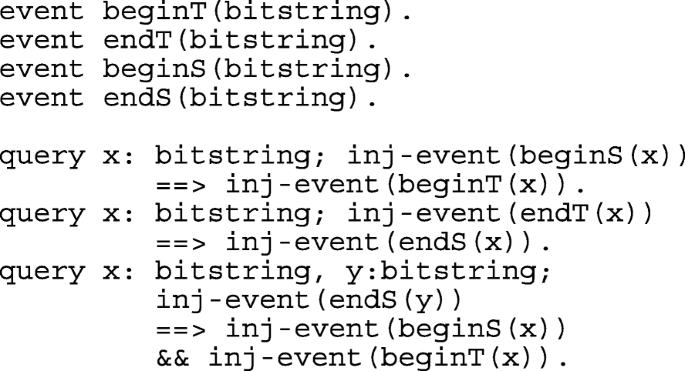
Secrecy of idt, hidt, xs, ri and rs is verified with queries query attacker(idt), query attacker(hidt), query attacker(xs), query attacker(new ri) and query attacker(new rs).
Mutual authentication between the Ti and Server is modeled with the definition of four events that are mapped in the SOI and SERVERS sub-processes and the following queries:
In the main process, SERVERS and SOI sub-processes are running in parallel. ! indicates an unlimited number of processes:
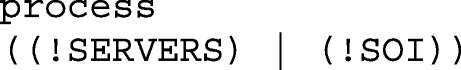
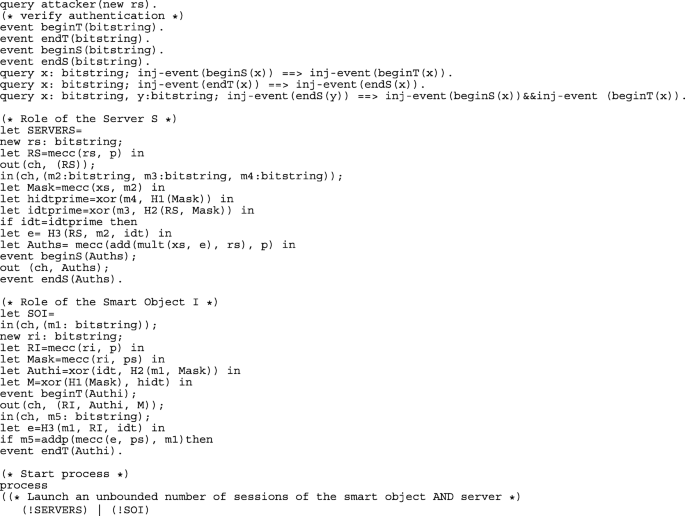
1.2.2 A.2.2 ProVerif results of Jin et al.’s authentication protocol improvements
1.2.3 A.2.3 Applied Pi calculus specification script of hash-based authentication protocol
Explanations of the applied pi calculus scripts are the following:
The secrets idt, hidt are declared as secret to the attacker using the word [private]. ch is the public channel where SERVERS and SOI exchange their messages and h, mecc, concat, xor represent hash, scalar multiplication, concatenation and xor functions respectively.
Secrecy of idt, hidt, ri and rs is verified with queries query attacker(idt), query attacker(hidt), query attacker(new ri) and query attacker(new rs).
Mutual authentication between the Ti and Server is modeled with definition of four events that are mapped in the SOI and SERVERS sub-processes and the following queries:
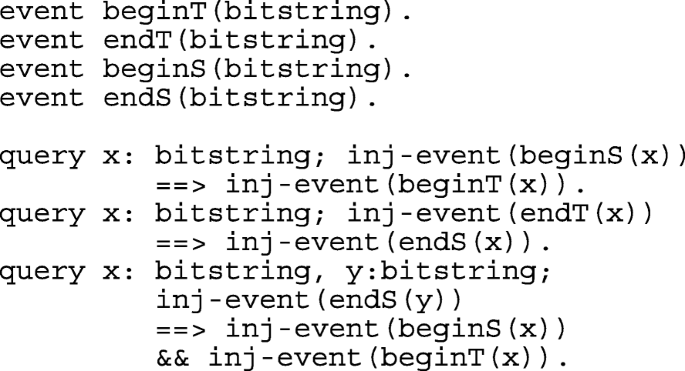
In the main process, SERVERS and SOI sub-processes are running in parallel. ! indicates an unlimited number of processes:
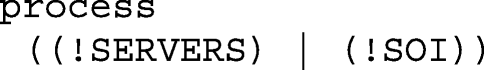
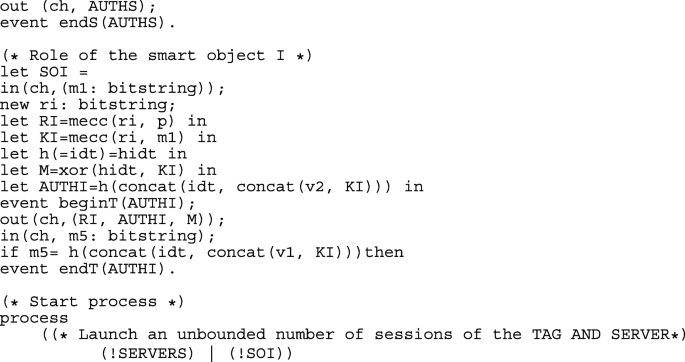
1.2.4 A.2.4 ProVerif results of hash-based authentication protocol
1.2.5 A.2.5 Applied Pi calculus specification script of ECC-based authentication protocol
Explanations of the applied pi calculus scripts are the following:
The secrets xa, xb are declared as secret to the attacker using the word [private]. ch is the public channel where SOA and SOB exchange their messages and h, mult, mecc, addp represent hash, multiplication, scalar multiplication and points addition functions respectively.
Secrecy of xa, xb, ra and rb is verified with query attacker(xa), query attacker(xb), query attacker(new ra) and query attacker(new rb).
Mutual authentication between Ti and Tj is modeled with the definition of four events that are mapped in the SOA and SOB sub-processes and the following queries:
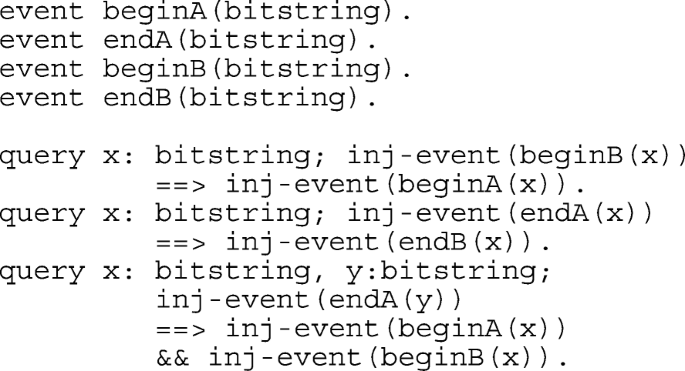
In the main process, SOA and SOB sub-processes are running in parallel. ! indicates an unlimited number of processes:


1.2.6 A.2.6 ProVerif results of ECC-based authentication protocol
Rights and permissions
About this article
Cite this article
Merabet, F., Cherif, A., Belkadi, M. et al. New efficient M2C and M2M mutual authentication protocols for IoT-based healthcare applications. Peer-to-Peer Netw. Appl. 13, 439–474 (2020). https://doi.org/10.1007/s12083-019-00782-8
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12083-019-00782-8