Abstract
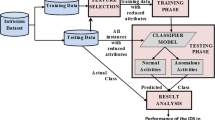
The rapid evolution of cloud computing technology has enabled seamless connection of devices on a broad spectrum. Also, it enables storage of massive quantity of data in the form of data centers. This suggests a shared pool of resources where users situated all over the world have access to the aforementioned data centers. Such a framework has cyber-security based challenges where it becomes vulnerable to external attacks. There arises a need for an Intrusion Detection System (IDS) to prevent the system from unwanted and malicious attacks. However, the existing IDS have not been able to efficiently combinehigh accuracy with low complexity and time efficiency. In order to overcome these challenges an Enhanced Intrusion Detection System via Agent Clustering and Classification based on Outlier Detection (EIDS-ACC-OD) is proposed. At first, preprocessing is performed to remove unwanted spaces using outlier detection. Then modified K-means clustering algorithm is developed for data segmentation. Further, K-Nearest Neighbor (KNN) is utilized for categorization of the attacks.







Similar content being viewed by others
References
Ali M et al (2015) Security in cloud computing: opportunities and challenges. Inf Sci 305:357–383
Javaid A et al (2016) A deep learning approach for network intrusion detection system. In: Proceedings of the 9th EAI international conference on bio-inspired information and communications technologies (formerly BIONETICS), pp. 21–26
Aljawarneh S et al (2018) Anomaly-based intrusion detection system through feature selection analysis and building hybrid efficient model. J Comput Sci 25:152–160
Faisal MA et al (2015) Data-stream-based intrusion detection system for advanced metering infrastructure in smart grid: a feasibility study. IEEE Syst J 9:31–44
Rajendran PK et al (2015) Hybrid intrusion detection system for private cloud: a systematic approach. Procedia Comput Sci 48:325–329
Narudin FA et al (2016) Evaluation of machine learning classifiers for mobile malware detection. Soft Comput 20:343–357
Shimna KM (2015) Continuous outlier detection based on sliding window on continuous data streams. Int J Sci Res 4
Sadiq AS et al (2018) An efficient IDS using hybrid magnetic swarm optimization in WANETs. IEEE Access 6:29041–29053
Pandeeswari N, Kumar G (2016) Anomaly detection system in cloud environment using fuzzy clustering based ANN. Mobile Netw Appl 21:494–505
Rousseeuw PJ, Hubert M (2018) Anomaly detection by robust statistics. Wiley Interdiscip Rev Data Min Knowl Disc 8:e1236
Hu W et al (2018) Anomaly detection using local kernel density estimation and context-based regression. IEEE Trans Knowl Data Eng
Jabez J, Muthukumar B (2015) Intrusion detection system (IDS): anomaly detection using outlier detection approach. Procedia Comput Sci 48:338–346
Ravale U et al (2015) Feature selection based hybrid anomaly intrusion detection system using K means and RBF kernel function. Procedia Comput Sci 45:428–435
Muda Z et al (2016) K-means clustering and naive bayes classification for intrusion detection. J IT Asia 4:13–25
Mohamad Tahir H et al (2015) Hybrid machine learning technique for intrusion detection system. International Conference on Computing and Informatics, 2015
Puri A, Sharma N (2017) A novel technique for intrusion detection system for network security using hybrid SVM-cart. International Journal of Engineering Development and Research (IJEDR) 5:155–161
Kumar A et al (2018) A novel hybrid K-means and artificial bee colony algorithm approach for data clustering. Decis Sci Lett 7:65–76
Shi Y et al (2018) Malicious domain name detection based on extreme machine learning. Neural Process Lett 48:1347–1357
Abozinadah EA et al (2015) Detection of abusive accounts with Arabic tweets. Int J Knowl Eng IACSIT 1:113–119
Veni RH et al (2018) Identifying malicious web links and their attack types in social networks, ed: IJSRCSEIT
Anfilofiev A et al (2014) Algorithm for tuning fuzzy network attack classifiers based on invasive weed optimization. In: 2014 dynamics of systems, mechanisms and machines (dynamics), pp. 1–4
Meti N et al (2017) Detection of distributed denial of service attacks using machine learning algorithms in software defined networks. In: 2017 international conference on advances in computing, communications and informatics (ICACCI), pp. 1366–1371
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Sandosh, S., Govindasamy, V. & Akila, G. Enhanced intrusion detection system via agent clustering and classification based on outlier detection. Peer-to-Peer Netw. Appl. 13, 1038–1045 (2020). https://doi.org/10.1007/s12083-019-00822-3
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12083-019-00822-3