Abstract
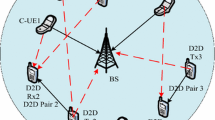
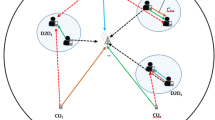
In cellular networks, proximity users establish device-to-device(D2D) links directly under the control of base stations (BSs) for data exchange, and no base station forwarding is required. For the advantages such as lower transmission power, higher data transmission rate, D2D communication has been paid more and more attention. However, the environmental impact of introducing D2D shared spectrum resources has become a major challenge. This paper studies a robust downlink power control scheme with imperfect channel state information (CSI) in D2D communication system. In order to improve the system sum rates, this paper optimizes the transmitting power of D2D users (DUEs) and the base stations through geometric analysis and convex optimization while guaranteeing the quality-of-service (QoS) requirements for both DUEs and cellular users (CUEs). Because of the dynamic characteristics of wireless channel, it is difficult and expensive to acquire CSI without direct communication with BS. On this account, we consider channel uncertainty rather than perfect or instantaneous known CSI. Aiming at enhancing the system robustness, we formulate an outage-based robust optimization problem. The original deterministic the signal-to-interference-noise-ratio (SINR) constraints are substituted with the transformed probability constraints, which transforms the random channel gain into a deterministic one with outage threshold. The simulation results show that the power allocation based on the proposed algorithm can adapt to the complex channel environment and are with better robustness.














Similar content being viewed by others
References
Bello O, Zeadally S (2014) Intelligent device-to-device communication in the internet of things. IEEE Systems Journal 10(3):1172–1182
Cisco T (2013) Cisco visual networking index: Global mobile data traffic forecast update, 2012-2017. Cisco Public Information 26:27
Liu Z, Gao L, Liu Y, Guan X, Ma K, Wang Y (2019) Efficient QoS support for robust resource allocation in blockchain-based femtocell networks. IEEE Transactions on Industrial Informatics 99:1–10. https://doi.org/10.1109/TII.2019.2939146
Phunchongharn P, Hossain E, Kim DI (2013) Resource allocation for device-to-device communications underlaying lte-advanced networks. IEEE Wireless Communications 20(4):91–100
Asadi A, Wang Q, Mancuso V (2014) A survey on device-to-device communication in cellular networks. IEEE Communications Surveys & Tutorials 16(4):1801–1819
Lin Y, Hsu Y (2000) Multihop cellular: A new architecture for wireless communications. In: Infocom nineteenth joint conference of the IEEE computer & communications societies IEEE, pp 1273–1282
Doppler K, Rinne M, Wijting C, Ribeiro C, Hugl K (2009) Device-to-device communication as an underlay to LTE-advanced networks. IEEE Commun Mag 47(12):42–49
Fodor G, Dahlman E, Mildh G, Parkvall S, Turanyi Z (2012) Design aspects of network assisted device-to-device communications. IEEE Commun Mag 50(3):170–177
Min H, Seo W, Lee J, Park S, Hong D (2011) Reliability improvement using receive mode selection in the device-to-device uplink period underlaying cellular networks. IEEE Trans Wireless Commun 10(2):413–418
Yu C, Tirkkonen O, Doppler K, Ribeiro C (2009) Power optimization of device-to-device communication underlaying cellular communication. In: IEEE international conference on communications, pp 1–5
Chen D, Tang Y, Zhang H, Wang L, Li X (2019) Incremental factorization of big time series data with blind factor approximation. IEEE Transactions on Knowledge and Data Engineering 99:1–16. https://doi.org/10.1109/TKDE.2019.2931687
Gu Y, Zhang Y, Miao P, Zhu H (2015) Matching and cheating in device to device communications underlying cellular networks. IEEE Journal on Selected Areas in Communications 33(10):2156–2166
Zhang R, Xiang C, Yang L, Jiao B (2013) Interference-aware graph based resource sharing for device-to-device communications underlaying cellular networks. In: Wireless communications & networking conference, pp 140–145
Dai Y, Sheng M, Liu J, Cheng N, Shen X, Yang Q (2019) Joint mode selection and resource allocation for D2D-enabled NOMA cellular networks. IEEE Trans Vehicular Technol 68(7):6721–6733
Xu S, Wang H, Tao C, Huang Q, Tao P (2010) Effective interference cancellation scheme for device-to-device communication underlaying cellular networks. In: Vehicular Technology Conference Fall, pp 1–5
Kusaladharma S, Zhang Z, Tellambura C (2019) Interference and outage analysis of random D2D networks underlaying millimeterwave cellular networks. IEEE Transactions on Communications 67(1):778–790
Min H, Jemin L, Sungsoo P, Daesik H (2011) Capacity enhancement using an interference limited area for device-to-device uplink underlaying cellular networks. IEEE Trans Wireless Commun 10(12):3995–4000
Feng D, Lu L, Yi Y, Li GY, Feng G, Li S (2013) Device-to-device communications underlaying cellular networks. IEEE Transactions on Communications 61(8):3541–3551
Kai Y, Wang J, Zhu H, Wang J (2019) Resource allocation and performance analysis of cellular-assisted OFDMA device-to-device communications. IEEE Trans Wireless Commun 18(1):416–431
Rim M, Kang CG (2019) Carrier sensing for ofdma-based D2D group-casting systems. IEEE Trans Vehicular Technol 66(3):2301–2310
Lee N, Lin X, Andrews J et al (2015) Power control for D2D underlaid cellular networks: Modeling, algorithms, and analysis. IEEE Journal on Selected Areas in Communications 33(1):1–13
Liu Z, Wang J, Xia Y, Fan R, Jiang H, Yang H (2016) Power allocation robust to time-varying wireless channels in femtocell networks. IEEE Transactions on Vichicular Technology 65(4):2806–2815
Liu Z, Wang S, Liu Y, Wang Y (2018) Secrecy transmission for femtocell networks against external eavesdropper. IEEE Trans Wireless Commun 17(8):5016–5028
Liu Z, Xie Y, Chan K, Ma K, Guan X (2019) Chance-constrained optimization in D2D-based vehicular communication network. IEEE Trans Vehicular Technol 68(5):5045–5058
Gong S, Wu S, So A, Huang X (2017) Distributionally robust collaborative beamforming in D2D relay networks with interference constraints. IEEE Trans Wireless Commun 16(8):5048–5060
Rezk Z, Alouini M (2012) Ergodic capacity of cognitive radio under imperfect channel state information. IEEE Trans Vehicular Technol 61(5):2108–2119
Liu Z, Liang C, Yuan Y, Guan X (2019) Energy efficient resource allocation based on relay selection and subcarrier pairing with channel uncertainty in cognitive radio network. Computer Networks 161:82–92
Liu Z, Wang J, Xia Y, Yang H (2013) Robust optimisation of power control for femtocell networks. IET Signal Processing 7(5):360–367
Yu C, Doppler K, Ribeiro C, Tirkkonen O (2009) Performance impact of fading interference to device-to-device communication underlaying cellular networks. In: IEEE International Symposium on Personal, pp 858–862
Janis P, Koivunen V, Ribeiro C, Korhonen J (2009) Interference-aware resource allocation for device-to-device radio underlaying cellular networks. In: IEEE Vehicular Technology Conference, pp 1–5
Chandrasekhar V, Andrews J, Muharemovic T, Shen Z, Gatherer A (2008) Power control in two-tier femtocell networks. IEEE Trans Wireless Commun 8(8):4316–4328
Memmi A, Rezki Z, Alouini M (2017) Device-to-device underlay cellular networks with uncertain channel state information. IEEE Trans Wireless Commun 16(2):1330–1343
Gjendemsjo A, Gesbert D, Oien GE, Kiani SG (2015) Optimal power allocation and scheduling for two-cell capacity maximization. In: International symposium on modeling & optimization in mobile, pp 1–6
Zulhasnine M, Huang C, Srinivasan A (2010) Efficient resource allocation for device-to-device communication underlaying LTE network. In: IEEE international conference on wireless & mobile computing, pp 368–375
Acknowledgments
This work is partly supported by National Natural Science Foundation of China under grant 61873223 and 61803328, the Natural Science Foundation of Hebei Province under grant F2019203095, F2017203140 and F2017203084.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendices
Appendix A: Proof of (11)
The detailed proof process of Eq. 11 is given as follows. Considering the constraint (10b),
Let \(Y_{1}=\gamma _{B}\alpha L_{ji}^{-\delta }\tilde {h}_{ji}^{2}\), where \(\tilde {h}_{ji}^{2}\ \thicksim E(1)\). Based on the conclusion from Appendix B of [24], we can conclude that the probability density function of Y1 is
Then the constraint (10b) is equivalent to the following form,
According to Eq. 35, it is obtained
Then, it holds that
That is
Finally,
The proof is completed.
Appendix B: Proof of (13)
The proof process of Eq. 13 is similar to Appendix A. Let \(Y_{2}=\alpha L_{jj}^{-\rho }\tilde {h}_{jj}^{2}\), where \(\tilde {h}_{jj}^{2}\ \thicksim E(1)\). The density function of Y2 is \(f(y_{2})=\frac {L_{jj}^{\rho }}{\alpha }e^{-\frac {L_{jj}^{\rho }}{\alpha }y_{2}}\). Then the constraint (10c),
can be transform to the deterministic form as follows,
That is,
Finally,
The proof is completed.
Rights and permissions
About this article
Cite this article
Liu, Z., Li, X., Yuan, Y. et al. Power control of D2D communication based on quality of service assurance under imperfect channel information. Peer-to-Peer Netw. Appl. 13, 1327–1339 (2020). https://doi.org/10.1007/s12083-019-00864-7
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12083-019-00864-7