Abstract
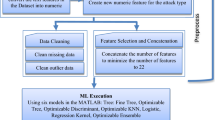
Internet of Things (IoT) is a significant area in the digital era for the purpose of data collection and transferring them on the network without the help of a human, which shows that the whole world is linked over a single system. It can also be seen as the powerful force that operates modern health systems, home automation, improved manufacturing, and smart cities. IoT increases the chances of cyber threats due to the extensive usage of IoT devices and services. Thus, there is a required to design a robust Intrusion Detection System (IDS) to obtain better network security. The conventional machine learning methods are not optimum for processing complex network data by various intrusion methods. Subsequently, the conventional deep learning approaches in intrusion detection show their efficiency in only one-dimensional feature data, and also they are insufficient for predicting the unknown intrusions. This paper focuses on proposing a novel High Ranking-based Optimized Ensemble Learning Model (HR-OELM) using three different classifiers for developing an intelligent IDS. The first phase is data collection, in which the benchmark datasets are gathered. As the features or attributes associated with the IoT devices from benchmark source datasets are more, it is required to extract the most relevant data that could be highly efficient for attaining the high detection rate. Thus, the accurate feature selection is developed to construct a powerful classification methgods and to decreases the data dimensionality. The major highlight of the optimal feature selection is to decreases the correlation between the features giving unique information. These features are subjected to the proposed HR-OELM, in which the Deep Neural Network (DNN), Random Forest, and Adaboost classifiers are used. The detection performance is finalized based on the high ranking of output from three classifiers. One of the main contributions of the proposed IDS is the development of Adaptive Frequency-based Electric Fish Optimization (AF-EFO) for the optimal feature selection and variable optimization of HR-OELM, thus ensuring superior performance. Finally, the suggested ensemble learning model holds a minimum false-positive range and a maximum detection range than the other conventional traditional methods.
















Similar content being viewed by others
References
Aloqaily M, Otoum S, Al Ridhawi I, Jararweh Y (2019) An intrusion detection system for connected vehicles in smart cities. Ad Hoc Netw
Al-Fuqaha A, Guizani M, Mohammadi M, Aledhari M, Ayyash M (2015) Internet of Things: A survey on enabling technologies, protocols, and applications. IEEE Commun Surv Tutor 2347–2376
Mosenia A, Jha NK (2017) A comprehensive study of security of internet-of-things. IEEE Trans Emerg Top Comput 5(4):586–602
Adat V, Gupta BB (2018) Security in Internet of Things: issues, challenges, taxonomy, and architecture. Telecommun Syst 423–441
Diro AA, Chilamkurti N (2018) Distributed attack detection scheme using deep learning approach for Internet of Things. Futur Gener Comput Syst 82:761–768
HaddadPajouh H, Dehghantanha A, Khayami R, Choo K (2018) A deep Recurrent Neural Network based approach for Internet of Things malware threat hunting. Future Gener Comput Syst 85:88–96
RandhirKumar PK, Tripathi R, Gupta GP, Garg S, Hassan MM (2022) A distributed intrusion detection system to detect DDoS attacks in blockchain-enabled IoT network. J Parallel Distrib Comput 164:55–68
Raghuvanshi A et al (2022) Intrusion detection using machine learning for risk mitigation in IoT-enabled smart irrigation in smart farming. J Food Qual
Geetha K, Brahmananda SH (2022) Network traffic analysis through deep learning for detection of an army of bots in health IoT network. Int J Pervasive Comput Commun
Balamurugan E, Mehbodniya A, Kariri E, Yadav K, Kumar A, AnulHaq M (2022) Network optimization using defender system in cloud computing security based intrusion detection system withgame theory deep neural network (IDSGT-DNN). Pattern Recognit Lett
Ziegeldorf JH, Morchon OG, Wehrle K (2014) Privacy in the Internet of Things: Threats and challenges. Secur Commun Netw 7(12):2728–2742
Eskandari M, Janjua ZH, Vecchio M, Antonelli F (2020) Passban IDS: An intelligent anomaly-based intrusion detection system for IoT edge devices. IEEE Internet Things J 7(8):6882–6897
Atzori L, Iera A, Morabito G (2010) The Internet of Things: A survey. Comput Netw 54(1):27872805
Rahman MA, Asyhari AT, Wen OW et al (2021) Effective combining of feature selection techniques for machine learning-enabled IoT intrusion detection. Multimed Tools Appl
Mavromatis A, Colman-Meixner C, Silva AP, Vasilakos X, Nejabati R, Simeonidou D (2020) A software-defined IoT device management framework for edge and cloud computing. IEEE Internet Things J 7(3):1718–1735
Elrawy M, Awad A, Hamed H (2018) Intrusion detection systems for IoT-based smart environments: a survey. J Cloud Comput. 7(21)
Zarpelao BB, Miani RS, Kawakani CT, Alvarenga SCD (2017) A survey of intrusion detection in internet of things. J Netw Comput Appl 84:25–37
Davahli A, Shamsi M, Abaei G (2020) Hybridizing genetic algorithm and grey wolf optimizer to advance an intelligent and lightweight intrusion detection system for IoT wireless networks. J Ambient Intell Humaniz Comput 11:5581–5609
Hosseinpour F, Amoli PV, Plosila J, Hamalainen T (2016) An intrusion detection system for fog computing and IoT based logistic systems using a smart data approach. Int J Digit Content Technol Appl 10(5):34–46
Keserwani PK, Govil MC, Pilli ES et al (2021) A smart anomaly-based intrusion detection system for the Internet of Things (IoT) network using GWO–PSO–RF model. J Reliab Intell Environ 7:3–21
Gothawal DB, Nagaraj SV (2020) Anomaly-based intrusion detection system in RPL by applying stochastic and evolutionary game models over IoT environment. Wirel Pers Commun 110:1323–1344
Li D, Cai Z, Deng L et al (2019) Information security model of block chain based on intrusion sensing in the IoT environment. Clust Comput 22:451–468
Verma A, Ranga V (2019) Machine learning based intrusion detection systems for IoT applications. Wirel Pers Commun
Mandal K, Rajkumar M, Ezhumalai P, Jayakumar D, Yuvarani R (2020) Improved security using machine learning for IoT intrusion detection system. Mater Today Proc
Otoum Y, Liu D, Nayak A (2019) DL-IDS: a deep learning–based intrusion detection framework for securing IoT. Trans Emerg Telecommun Technol
Li W, Meng W, Au MH (2020) Enhancing collaborative intrusion detection via disagreement-based semi-supervised learning in IoT environments. J Netw Comput Appl 161
Almiani M, AbuGhazleh A, Al-Rahayfeh A, Atiewi A, Razaque A (2020) Deep recurrent neural network for IoT intrusion detection system. Simul Model Pract Theor 101
Li Y, Xu Y, Liu Z, Hou H, Zheng Y, Xin Y, Zhao Y, Cui L (2020) Robust detection for network intrusion of industrial IoT based on multi-CNN fusion. Measurement 154
Yahyaoui A, Abdellatif T, Yangui S, Attia R (2021) READ-IoT: Reliable event and anomaly detection framework for the Internet of Things. IEEE Access 9:24168–24186
Mishra N, Pandya S (2021) Internet of Things applications, security challenges, attacks, intrusion detection, and future visions: A systematic review. IEEE Access 9:59353–59377
Moustafa N, Turnbull B, Choo KR (2019) An ensemble intrusion detection technique based on proposed statistical flow features for protecting network traffic of internet of Things. IEEE Internet Things J 6(3):4815–4830
Attota DC, Mothukuri V, Parizi RM, Pouriyeh S (2021) An ensemble multi-view federated learning intrusion detection for IoT. IEEE Access 9:117734–117745
Siddiqui AJ, Boukerche A (2021) TempoCode-IoT: temporal codebook-based encoding of flow features for intrusion detection in Internet of Things. Cluster Comput 24:17–35
Lee JD, Cha HS, Rathore S, Park JH (2021) M-IDM: A multi-classication based intrusion detection model in healthcare IoT. Comput Mater Continua 67(2)
Yilmaz S, Sen S (2020) Electric fish optimization: a new heuristic algorithm inspired by electrolocation. Neural Comput Appl 32:11543–11578
Ali MH et al (2022) Threat analysis and Distributed Denial of Service (DDoS) attack recognition in the Internet of Things (IoT). Electroinics 11(3):494
Naseer S et al (2018) Enhanced network anomaly detection based on deep neural networks. IEEE Access 6:48231–48246
Lee S, Chen T, Yu L, Lai C (2018) Image classification based on the boost convolutional neural network. IEEE Access 6:12755–12768
Tesfahun A, Bhaskari DL (2013) Intrusion detection using random forests classifier with SMOTE and feature reduction. Int Conf Cloud Ubiquitous Comput Emerg Technol
Liu J, Yang D, Lian M, Li M (2021) Research on intrusion detection based on particle swarm optimization in IoT. IEEE Access 9:38254–38268
Guo MW, Wang JS, Zhu LF, Guo SS, Xie W (2020) An improved grey wolf optimizer based on tracking and seeking modes to solve function optimization problems. IEEE Access 8:69861–69893
Vijayanand R, Devaraj D (2020) A novel feature selection method using whale optimization algorithm and genetic operators for intrusion detection system in wireless mesh network. IEEE Access 8:56847–56854
Gao X, Shan C, Hu C, Niu Z, Liu Z (2019) An adaptive ensemble machine learning model for intrusion detection. IEEE Access 7:82512–82521
Tao P, Sun Z, Sun Z (2018) An improved intrusion detection algorithm based on GA and SVM. IEEE Access 6:13624–13631
Haghighat MH, Li J (2021) Intrusion detection system using voting-based neural network. Tsinghua Sci Technol 26(4):484–495
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of Interest
The Author declare No Conflict of Interest.
Additional information
Publisher's note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Gopalakrishnan, B., Purusothaman, P. A new design of intrusion detection in IoT sector using optimal feature selection and high ranking-based ensemble learning model. Peer-to-Peer Netw. Appl. 15, 2199–2226 (2022). https://doi.org/10.1007/s12083-022-01336-1
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12083-022-01336-1