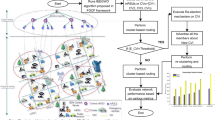
Abstract
Fog-based vehicular communication has received a huge interest due to rise in vehicular traffic and numerous services, like transferring messages among vehicles in an emergency and other scenarios. Secure storage, password protection, authorization, accessibility, and an authentic summary of the data flow are required in existing centralized approach. Conventional approaches process data at the servers, which affects network latency and throughput. Transferring data from edge devices to a centralized server increases the risk of being hacked, which results in corrupted data and data destruction. Nonetheless, conventional fog-based protocols are susceptible to various threats and proved inefficient in terms of computation and communication cost. In this article, we propose a secure and robust authentication protocol for fog-based vehicular communication. Moreover, the formal security verification using Random Oracle Model and commonly used software, Automated Validation of Internet Security Protocols and Applications and informal analysis represent that our proposed protocol is secure against man-in-the-middle and replay attacks. The performance comparison shows that the protocol addresses added security features with the least possible latency, computation, communication, and storage cost compared to the state-of-the-art protocols. As a result, our proposed protocol’s high-security features indicate its robustness and make it feasible for practical application.







Similar content being viewed by others
Data availability
There is no data or any other material associated with this manuscript.
Code availability
Not Applicable.
References
Kesavan R, Loganathan V, Shankar T, Periasamy J (2022) Fog-computing: a novel approach for cloud-based devices using perceptual cloning manifestation-percolnif taxonomy by energy optimization. In: Energy Conservation Solutions for Fog-Edge Computing Paradigms. Springer, pp 107–128
Bhanu C (2021) Challenges, benefits and issues: future emerging VANETs and cloud approaches. Cloud and IoT-Based Vehicular Ad Hoc Networks, pp 233–267
Yi S, Qin Z, Li Q (2015) Security and privacy issues of fog computing: a survey. In: International conference on wireless algorithms, systems, and applications. Springer, pp 685–695
Zhang J, Cui J, Zhong H, Bolodurina I, Liu L (2020) Intelligent drone-assisted anonymous authentication and key agreement for 5g/b5g vehicular ad-hoc networks. IEEE Trans Netw Sci Eng
Yazdinejad A, Parizi RM, Dehghantanha A, Choo K-KR (2019) Blockchain-enabled authentication handover with efficient privacy protection in SDN-based 5G networks. IEEE Trans Netw Sci Eng
Ma M, He D, Wang H, Kumar N, Choo K-KR (2019) An efficient and provably secure authenticated key agreement protocol for fog-based vehicular ad-hoc networks. IEEE Internet Things J 6(5):8065–8075
Eftekhari SA, Nikooghadam M, Rafighi M (2021) Security-enhanced three-party pairwise secret key agreement protocol for fog-based vehicular Ad-Hoc communications. Veh Commun 28:100306
Srinivas J, Das AK, Kumar N, Rodrigues JJ (2018) Cloud centric authentication for wearable healthcare monitoring system. IEEE Trans Dependable Secure Comput 17(5):942–956
Wazid M, Das AK, Hussain R, Succi G, Rodrigues JJ (2019) Authentication in cloud-driven IoT-based big data environment: survey and outlook. J Syst Archit 97:185–196
Guo Y, Zhang Z, Guo Y (2021) Anonymous authenticated key agreement and group proof protocol for wearable computing. IEEE Trans Mob Comput
Bellavista P, Berrocal J, Corradi A, Das SK, Foschini L, Zanni A (2019) A survey on fog computing for the internet of things. Pervasive Mob Comput 52:71–99
Ibrahim MH (2016) Octopus: an edge-fog mutual authentication scheme. IJ Network Security 18(6):1089–1101
Gope P (2019) Laap: lightweight anonymous authentication protocol for D2D-aided fog computing paradigm. Comput Secur 86:223–237
Jia X, He D, Kumar N, Choo K-KR (2019) Authenticated key agreement scheme for fog-driven IoT healthcare system. Wirel Netw 25(8):4737–4750
Wu T-Y, Wang T, Lee Y-Q, Zheng W, Kumari S, Kumar S (2021) Improved authenticated key agreement scheme for fog-driven IoT healthcare system. Secur Commun Netw
Wazid M, Das AK, Kumar N, Vasilakos AV (2019) Design of secure key management and user authentication scheme for fog computing services. Futur Gener Comput Syst 91:475–492
Guo Y, Zhang Z, Guo Y (2020) Fog-centric authenticated key agreement scheme without trusted parties. IEEE Syst J
He D, Zeadally S, Xu B, Huang X (2015) An efficient identity-based conditional privacy-preserving authentication scheme for vehicular ad hoc networks. IEEE Trans Inf Forensics Secur 10(12):2681–2691
Shao J, Lin X, Lu R, Zuo C (2015) A threshold anonymous authentication protocol for vanets. IEEE Trans Veh Technol 65(3):1711–1720
Wang H, Wang Q, He D, Li Q, Liu Z (2019) BBARS: Blockchain-based anonymous rewarding scheme for V2G networks. IEEE Internet Things J 6(2):3676–3687
Zhao Z, Chen J, Zhang Y, Dang L (2015) An efficient revocable group signature scheme in vehicular ad hoc networks. KSII Trans Internet Inf Syst (TIIS) 9(10):4250–4267
Wazid M, Bagga P, Das AK, Shetty S, Rodrigues JJ, Park Y (2019) AKM-IoV: authenticated key management protocol in fog computing-based internet of vehicles deployment. IEEE Internet Things J 6(5):8804–8817
Saleem MA, Mahmood K, Kumari S (2020) Comments on AKM-IoV: authenticated key management protocol in fog computing-based internet of vehicles deployment. IEEE Internet Things J 7(5):4671–4675
Chen C-M, Huang Y, Wang K-H, Kumari S, Wu M-E (2020) A secure authenticated and key exchange scheme for fog computing. Enterp Inf Syst 1–16
Navdeti CP, Banerjee I, Giri C (2021) Privacy preservation and secure data sharing scheme in fog based vehicular ad-hoc network. J Inf Secur Appl 63:103014
Alotaibi J, Alazzawi L (2021) A lightweight and fog-based authentication scheme for internet-of-vehicles. In: IEEE 12th Annual Ubiquitous Computing, Electronics & Mobile Communication Conference (UEMCON). IEEE 2021:0197–0203
Dolev D, Yao A (1983) On the security of public key protocols. IEEE Trans Inf Theory 29(2):198–208
Canetti R, Krawczyk H (2001) Analysis of key-exchange protocols and their use for building secure channels. In: International Conference on the Theory and Applications of Cryptographic Techniques. Springer, pp 453–474
Bellare M, Rogaway P (1993) Random oracles are practical: a paradigm for designing efficient protocols. In: Proceedings of the 1st ACM conference on Computer and communications security. ACM, pp 62–73
Viganò L (2006) Automated security protocol analysis with the AVISPA tool. Electron Notes Theor Comput Sci 155:61–86
Cui J, Zhang X, Zhong H, Ying Z, Liu L (2019) RSMA: Reputation system-based lightweight message authentication framework and protocol for 5G-enabled vehicular networks. IEEE Internet Things J 6(4):6417–6428
Acknowledgements
Saru Kumari is supported by the State Government of Uttar Pradesh, India under the “Research and Development” scheme grant sanctioned vide the Government order no. -89/2022/1585/sattar-4-2022/001-4-32-2022 dated 10/11/2022.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Competing interests
The authors proclaim that they have no competing interests.
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Akram, M.A., Mian, A.N. & Kumari, S. Fog-based low latency and lightweight authentication protocol for vehicular communication. Peer-to-Peer Netw. Appl. 16, 629–643 (2023). https://doi.org/10.1007/s12083-022-01425-1
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12083-022-01425-1