Abstract
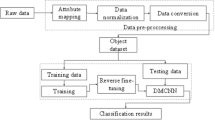
The sample data of the existing intrusion detection models of the Internet of Things has defects such as class imbalance and insufficient feature extraction, which leads to low accuracy. Therefore, an intrusion detection model based on Gated Recurrent Unit (GRU) and Residual Network (ResNet) is proposed. Firstly, the deep convolutional generative adversarial network is used to generate a few sample data in the class imbalance data to make the sample data reach balance. Then, GRU is used to learn the data features, extract time series features of the sample data, classify the sample data features with the ResNet, and finally normalize the classification results with the softmax function. The proposed model is verified on NSL-KDD dataset, simulation experiments on NSL-KDD dataset show that the accuracy and detection rate of the proposed intrusion detection model reach 96.12% and 97.85% respectively, which are 1.86% and 2.59% higher than those of LSTM-ResNet method. And compared with GRU, LSTM and SVM, the validity of the model was verified.











Similar content being viewed by others
Data availability
The data on which the study is based were accessed from a repository and are available for downloading through the following link https://www.unb.ca/cic/datasets/nsl.html.
References
Kolias C, Kambourakis G, Stavrou A, Voas J (2017) DDoS in the IoT: Mirai and other botnets. Computer 50(7):80–84
Li D, Deng L, Lee M, Wang H (2019) IoT data feature extraction and intrusion detection system for smart cities based on deep migration learning. Int J Inf Manage 49(10):533–545
Tian L, Lu Y (2021) An intrusion detection model based on SMOTE and convolutional neural network ensemble. In: Journal of Physics: Conference Series, IOP Publishing, pp 1–9
Li J, Zhu Q, Wu Q et al (2021) A novel oversampling technique for class-imbalanced learning based on SMOTE and natural neighbors. Inf Sci 565:438–455
Alshamy R, Ghurab M, Othman S et al (2021) Intrusion Detection Model for Imbalanced Dataset Using SMOTE and Random Forest Algorithm. In: International Conference on Advances in Cyber Security, Springer, pp 361–378
Lee JH, Park KH (2019) GAN-based imbalanced data intrusion detection system. Pers Ubiquit Comput 25(9):1–8
Yu Y, Gong Z, Zhong P, Shan J (2017) Unsupervised representation learning with deep convolutional neural network for remote sensing images. In: International Conference on Image and Graphics, Springer, pp 97–108
Mo K, Wang N, Li H, Li C, Li J (2019) Network instrusion detection system model based on LightGBM. J Inf Secur Res 5(2):152–156
Riyaz B, Ganapathy S (2020) A deep learning approach for effective intrusion detection in wireless networks using CNN. Soft Comput 24(22):17265–17278
Xiao Z, Luktarhan N (2021) Webshell detection with byte-level features based on deep learning. J Intell Fuzzy Syst 40(1):1585–1596
Smys S, Basar A, Wang H (2020) Hybrid intrusion detection system for internet of Things (IoT). J ISMAC 2(04):190–199
Shone N, Ngoc TN, Phai VD et al (2018) A Deep Learning Approach to Network Intrusion Detection. IEEE Trans Emerg Top Comput Intell 2(1):41–50
Li Y, Xu Y, Liu Z, Hou H (2019) Robust detection for network intrusion of industrial IoT based on multi-CNN fusion. Measurement 154:1561–1573
Javaid JY, Niyaz Q, Sun W, Alam M (2016) A deep learning approach for network intrusion detection system. In: The 9th EAI International Conference on Bio-inspired Information and Communications Technologies, ICST, pp 21–26
Kim S, Jo W, Shon T (2020) APAD: Autoencoder-based payload anomaly detection for industrial IoE. Appl Soft Comput 88(5):1–9
Zhang Y, Zhang N, Xiao M (2020) A network intrusion detection method based on deep learning with higher accuracy. Procedia Comput Sci 174:50–54
Kumar G (2020) An improved ensemble approach for effective intrusion detection. J Supercomput 76(1):275–291
Assis MVO, Carvalho LF, Lloret J et al (2021) A GRU deep learning system against attacks in software defined networks. J Netw Comput Appl 177:1–13
Gupta N, Jindal V, Bedi P (2021) LIO-IDS: Handling class imbalance using LSTM and improved one-vs-one technique in intrusion detection system. Comput Netw 192:1–19
Shaikh A, Gupta P (2022) Real-time intrusion detection based on residual learning through ResNet algorithm. Int J Syst Assur Eng Manag 1(13):1–15
Acknowledgements
This present research work was supported by the National Natural Science Foundation of China (No.61202458, 61403109), the Natural Science Foundation of Heilongjiang Province of China (No.LH2020F034, F2017021) and the Harbin Science and Technology Innovation Research Funds (No.2016RAQXJ036).
Funding
The National Natural Science Foundation of China, 61202458, Guosheng Zhao, 61403109, Guosheng Zhao, Natural Science Foundation of heilongjiang Province, LH2020F034, Jian Wang, F2017021, Jian Wang, Harbin Science and Technology Innovation Research Funds, 2016RAQXJ036,Guosheng Zhao.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Competing interests
The authors have no competing interests to declare that are relevant to the content of this article.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Zhao, G., Ren, C., Wang, J. et al. IoT intrusion detection model based on gated recurrent unit and residual network. Peer-to-Peer Netw. Appl. 16, 1887–1899 (2023). https://doi.org/10.1007/s12083-023-01510-z
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12083-023-01510-z