Abstract
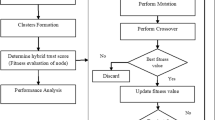
Designing a routing protocol that can against the attacks of malicious nodes is very essential because open wireless channels make a wireless ad hoc network (WAN) affected by different security attacks. To overcome this problem, Dual-Discriminator Conditional Generative Adversarial Network Optimized with Namib beetle optimization algorithm is proposed in this manuscript for cluster head based secure routing in Wireless Ad-hoc Networks (CH-SR-DDCGAN-NBOA-WAN). Here, the proposed CH-SR-DDCGAN-NBOA-WAN method consists of two phases: (i) to find the optimal CHs (ii) to find optimal trust path. At first, Dual-discriminator conditional generative adversarial network is utilized for selecting Cluster Head (CH) depending on the multi-objective fitness function. The multi-objective fitness function considers the factors, namely set of nodes, determining short security paths connecting sources and destinations, and links schedule with the routes that fulfills the request of all nodes to decrease the energy consumption of whole network, and also increase the defense against spiteful nodes. Therefore, in this work, proposed Namib beetle optimization algorithm (NBOA) is utilized for optimizing the Dual-discriminator conditional generative adversarial network, which selects the CH accurately. After CH selection, Nomadic People Optimization Algorithm (NPOA) is used to identify the trust path from that are confirmed by using trust parameters, such as integrity, consistency, forwarding rate, availability factor. The proposed CH-SR-DDCGAN-NBOA-WAN approach is activated in network stimulator NS-2 and its performance is examined under performance metrics, such as drop, normalized network energy, network lifetime, delay, throughput, energy consumption, Packet Delivery Ratio. The proposed CH-SR-DDCGAN-NBOA-WAN approach attains 23.31%, 24.5%, and 30.01% lower packet drop, 12.45%, 17.34% and 24.67% higher network life time and 11.45%, 17.34% and 29.56% lower average delay time compared with existing methods, such as FCO-fuzzy constraints applied cluster optimization technique for wireless ad-hoc networks (CH-SR-FCO-WAN), trust-based secure routing and the prevention of attack in WAN (CH-SR-KID-SASR-WAN) and a secure routing scheme to mitigate attack in wireless ad-hoc sensor network CH-SR-BSCSRP-WAN respectively.








Similar content being viewed by others
Data availability
Data sharing does not apply to this article as no new data has been created or analyzed in this study.
References
Boulaiche M (2020) Survey of secure routing protocols for wireless ad hoc networks. Wirel Pers Commun 114(1):483–517
Kumar KV, Jayasankar T, Eswaramoorthy V, Nivedhitha V (2020) SDARP: Security based Data Aware Routing Protocol for ad hoc sensor networks. Int J Intell Net 1:36–42
Mahapatra SN, Singh BK (2023) An efficient and secure cluster-based cooperative data transmission for wireless ad hoc networks IOT environment. In: Machine vision and augmented intelligence: Select proceedings of MAI 2022. Springer Nature Singapore, Singapore, pp 651–663
Kumar PP, Bai V, Amala M, Krish RP (2023) Krill herd optimization algorithm with deep convolutional neural network fostered breast cancer classification using mammogram images. CONCURR COMP-PRACT E 35(7)
Hu F, Chen B, Shi D, Zhang X, Pan HZ (2020) Secure routing protocol in wireless ad hoc networks via deep learning. In: 2020 IEEE Wireless Communications and Networking Conference (WCNC). IEEE, pp 1–6
Hosmani S, Mathapati B (2023) R2SCDT: robust and reliable secure clustering and data transmission in vehicular ad hoc network using weight evaluation. J Ambient Intell Humaniz Comput 14(3):2029–2046
Azhdari MS, Barati A, Barati H (2022) A cluster-based routing method with authentication capability in Vehicular Ad hoc Networks (VANETs). J Parallel Distrib Comput 169:1–23
Abdulhae OT, Mandeep JS, Islam M (2022) Cluster-based routing protocols for flying ad hoc networks (FANETs). IEEE Access 10:32981–33004
Thirunavukkarasu V, Senthil Kumar A, Prakasam P (2022) Cluster and angular based energy proficient trusted routing protocol for mobile ad-hoc network. Peer-to-Peer Netw Appl 15(5):2240–2252
Hosseinzadeh M, Mohammed AH, Alenizi FA, Malik MH, Yousefpoor E, Yousefpoor MS, Ahmed OH, Rahmani AM, Tightiz L (2023) A novel fuzzy trust-based secure routing scheme in flying ad hoc networks. Veh Commun 100665
Shakya DS (2020) The robust routing protocol with authentication for wireless adhoc networks. Journal of IoT in Social, Mobile, Analytics, and Cloud 2(2):83–95
Namdev M, Goyal S, Agarwal R (2021) An optimized communication scheme for energy efficient and secure flying ad-hoc network (FANET). Wirel Pers Commun 120(2):1291–1312
Prithi S, Sumathi S (2020) LD2FA-PSO: A novel learning dynamic deterministic finite automata with PSO algorithm for secured energy efficient routing in wireless sensor network. Ad Hoc Netw 97:102024
Krishnasamy B, Muthaiah L, Kamali Pushparaj JE, Pandey PS (2023) DIWGAN optimized with Namib Beetle Optimization Algorithm for intrusion detection in mobile ad hoc networks. IETE J Res 1–20
Arivubrakan P, Kanagachidambaresan GR (2023) Multi-objective cluster head-based energy-aware routing protocol using hybrid woodpecker and flamingo search optimization algorithm for Internet of Things environment. Int J Inf Technol Decis Mak 1–20
Devi VB, Elma KJ, Rooban S, Shajin FH (2023) Self-attention based progressive generative adversarial network optimized with arithmetic optimization algorithm for kidney stone detection. CONCURR COMP-PRACT E 35(6)
Ma J, Xu H, Jiang J, Mei X, Zhang X (2020) PDDcGAN: A dual-discriminator conditional generative adversarial network for multi-resolution image fusion. IEEE Trans Image Process 29:4980–4995
Chahardoli M, Eraghi NO, Nazari S (2022) Namib beetle optimization algorithm: a new meta-heuristic method for feature selection and dimension reduction. Concurr Comput: Practice and Experience 34(1):e6524
Mohamadi S, Sammen SS, Panahi F, Ehteram M, Kisi O, Mosavi A, Ahmed AN, El-Shafie A, Al-Ansari N (2020) Zoning map for drought prediction using integrated machine learning models with a nomadic people optimization algorithm. Nat Hazards 104(1):537–579
Mohammed AS, Basha S, Asha PN, Venkatachalam K (2020) FCO—fuzzy constraints applied cluster optimization technique for wireless adhoc networks. Comput Commun 154:501–508
Isaac Sajan R, Jasper J (2020) Trust-based secure routing and the prevention of vampire attack in wireless ad hoc sensor network. Int J Commun Syst 33(8):e4341
Jasper J (2021) A secure routing scheme to mitigate attack in wireless adhoc sensor network. Comput Sec 103:102197
Hu S, Chen X, Ni W, Hossain E, Wang X (2021) Distributed machine learning for wireless communication networks: Techniques, architectures, and applications. IEEE Commun Surveys and Tutorials 23(3):1458–1493
Kumar KV, Jayasankar T, Eswaramoorthy V, Nivedhitha VS (2020) DARP: Security based Data Aware Routing Protocol for ad hoc sensor networks. Int J Intell Net 1:36–42
Gomathy V, Padhy N, Samanta D, Sivaram M, Jain V, Amiri IS (2020) Malicious node detection using heterogeneous cluster based secure routing protocol (HCBS) in wireless adhoc sensor networks. J Ambient Intell Humanized Comput 11(11):4995–5001
Acknowledgements
Not Applicable.
Funding
This research did not receive any specific grant from funding agencies in the public, commercial, or not-for-profit sectors.
Author information
Authors and Affiliations
Contributions
R. Prabha - (Corresponding Author) - Conceptualization Methodology, Original draft preparation. G.A. Senthil – Supervision. SU. Suganthi – Supervision.
Corresponding author
Ethics declarations
Ethical approval and consent to participate
This article does not contain any studies with human participants performed by any of the authors.
Consent for publication
Not Applicable
Competing interests
Not Applicable.
Human and animal ethics
Not Applicable
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Prabha, R., Senthil, G.A. & Suganthi, S. Cluster head based secure routing using optimized dual-discriminator conditional generative adversarial network in wireless ad-hoc networks. Peer-to-Peer Netw. Appl. 16, 2747–2760 (2023). https://doi.org/10.1007/s12083-023-01545-2
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12083-023-01545-2