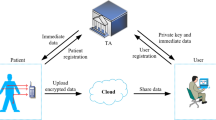
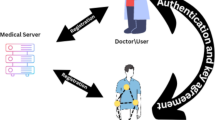
Abstract
Electronic healthcare based on medical sensors is now developing to incorporate a significant amount of the Internet of Things (IoT) to communicate between sensors and intended recipients. The key requirements in this domain are to exchange messages safely and to provide confidentiality during communication. Designing and implementing an authentication strategy is essential for resolving security concerns, but it is also challenging to work with constrained computing and processing resources during group communication. Standard one-to-one authentication models do not consider the scalability of resource-limited nodes, which is a vital factor to deal with. However, group authentication presents a unique concept for IoT nodes that verify group members concurrently. The conventional group authentication methods based on the IoT are vulnerable to security risks and cannot defend against attacks like replay attacks, forgery attacks, or unauthorized key distribution by the group manager. In this paper, we propose a dynamic and provable group authentication scheme (GAS) based on a secret sharing scheme that can withstand the dishonest behavior of group managers. We introduced a key updating scenario with a provable group authentication model for dynamic node leaving and joining. Our system complies with the requirements for secrecy and accuracy, and based on security analysis, it is resistant to attacks, as mentioned earlier. Performance analysis and security proof show that our approach performs well in terms of computation cost for group members while maintaining security.








Similar content being viewed by others
Data availibility statement
Not Applicable.
References
Rouhani S, Butterworth L, Simmons AD, Humphery DG, Deters R (2018) Medichain tm: a secure decentralized medical data asset management system. In: 2018 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), pp 1533–1538. IEEE
Darshan K, Anandakumar K (2015) A comprehensive review on usage of internet of things (iot) in healthcare system. In: 2015 International Conference on Emerging Research in Electronics, Computer Science and Technology (ICERECT), pp 132–136. IEEE
Trivedi C, Rao UP (2023) Secrecy aware key management scheme for internet of healthcare things. J Supercomput pp 1–31
Sengupta J, Ruj S, Bit SD (2020) A comprehensive survey on attacks, security issues and blockchain solutions for iot and iiot. J Netw Comput App 149
Yue X, Wang H, Jin D, Li M, Jiang W (2016) Healthcare data gateways: found healthcare intelligence on blockchain with novel privacy risk control. J Med Syst 40(10):218
Feroz Khan AB, Anandharaj G (2021) Ahkm: An improved class of hash based key management mechanism with combined solution for single hop and multi hop nodes in iot. Egypt Inform J 22(2):119–124. https://doi.org/10.1016/j.eij.2020.05.004
Gautam A, Kumar R (2021) A comprehensive study on key management, authentication and trust management techniques in wireless sensor networks. SN Appl Sci 3. https://doi.org/10.1007/s42452-020-04089-9
Lara E, Aguilar L, Sanchez MA, García JA (2020) Lightweight authentication protocol for m2m communications of resource-constrained devices in industrial internet of things. Sensors 20(2). https://doi.org/10.3390/s20020501
Fouda MM, Fadlullah ZM, Kato N, Lu R, Shen XS (2011) A lightweight message authentication scheme for smart grid communications. IEEE Trans Smart Grid 2(4):675–685
Shun Z, Hongli F, Hong Z, Miaomiao T (2018) Efficient and revocable certificateless remote anonymous authentication protocol in wireless body area network. J Commun 39(4):100–111
Fang W-D, Zhang W-X, Yang Y, Zhang C-L, Chen W (2018) Bth-uap: Biometric-based three-factor user authentication protocol for wireless sensor network. Acta Electon Sin 46(3):702
Zhang W-F, Lei L-T, Wang X-M, Wang Y (2020) Secure and efficient authentication and key agreement protocol using certificateless aggregate signature for cloud service oriented vanet. Acta Electon Sin 48(9):1814
Li T, Liu Y (2021) A double puf-based rfid authentication protocol. J Comput Res Dev 58(8):1801–1810
Bang AO, Rao UP, Visconti A, Brighente A, Conti M (2022) An iot inventory before deployment: A survey on iot protocols, communication technologies, vulnerabilities, attacks, and future research directions. Comput Sec 102914
Shamir A (1979) How to share a secret. Commun ACM 22(11):612–613
Harn L (2012) Group authentication. IEEE Trans Comput 62(9):1893–1898
Ahmadian Z, Jamshidpour S (2017) Linear subspace cryptanalysis of harn’s secret sharing-based group authentication scheme. IEEE Trans Inf Forensics Secur 13(2):502–510
Chien H-Y (2017) Group authentication with multiple trials and multiple authentications. Secur Commun Netw 2017
Xia Z, Liu Y, Hsu C-F, Chang C-C (2020) Cryptanalysis and improvement of a group authentication scheme with multiple trials and multiple authentications. Secur Commun Netw 2020
Aydin Y, Kurt GK, Ozdemir E, Yanikomeroglu H (2020) A flexible and lightweight group authentication scheme. IEEE Internet Things J 7(10):10277–10287
Park Y, Park Y (2017) A selective group authentication scheme for iot-based medical information system. J Med Syst 41(4):1–8. https://doi.org/10.1007/s10916-017-0692-9
Lee D-H, Lee I-Y (2018) Dynamic group authentication and key exchange scheme based on threshold secret sharing for iot smart metering environments. Sensors 18(10). https://doi.org/10.3390/s18103534
Wang A, Shen J, Yan L, Ren Y, Liu Q (2018) A practical group authentication scheme for smart devices in iot. EAI Endorsed Trans Internet Things 4(15). https://doi.org/10.4108/eai.5-3-2019.156719
Tan H, Chung I (2019) Secure authentication and group key distribution scheme for wbans based on smartphone ecg sensor. IEEE Access 7:151459–151474. https://doi.org/10.1109/ACCESS.2019.2948207
Khatoon S, Rahman SMM, Alrubaian M, Alamri A (2019) Privacy-preserved, provable secure, mutually authenticated key agreement protocol for healthcare in a smart city environment. IEEE Access 7:47962–47971. https://doi.org/10.1109/ACCESS.2019.2909556
Xiong H, Qin Z (2015) Revocable and scalable certificateless remote authentication protocol with anonymity for wireless body area networks. IEEE Trans Inf Forensics Secur 10(7):1442–1455
Trnka M, Cerny T, Stickney N (2018) Survey of authentication and authorization for the internet of things. Secur Commun Netw 2018
Forouzan BA (2007) Cryptography and Network Security. McGraw-Hill, Inc
Neshenko N, Bou-Harb E, Crichigno J, Kaddoum G, Ghani N (2019) Demystifying iot security: an exhaustive survey on iot vulnerabilities and a first empirical look on internet-scale iot exploitations. IEEE Commun Surv Tutorials
Kabra A, Kumar S, Kasbekar GS (2020) Efficient, flexible and secure group key management protocol for dynamic iot settings. arXiv preprint arXiv:2008.06890
Hassan WH et al (2019) Current research on internet of things (iot) security: A survey. Comput Netw 148:283–294
Ahanger TA, Aljumah A (2018) Internet of things: A comprehensive study of security issues and defense mechanisms. IEEE Access 7:11020–11028
Zhang L, Zhang F, Huang X (2009) A secure and effcient certificateless signature scheme using bilinear pairing. Chin J Electron 18(1):145–148
Koblitz N (1987) Elliptic curve cryptosystems. Math Comput 48(177):203–209
Wang F, Chang C-C, Chou Y-C (2015) Group authentication and group key distribution for ad hoc networks. Int J Netw Secur 17(2):199–207
Choksy P, Chaurasia A, Rao UP, Kumar S (2023) Attribute based access control (abac) scheme with a fully flexible delegation mechanism for iot healthcare. Peer-to-Peer Netw App pp 1–23
Mahmood K, Chaudhry SA, Naqvi H, Kumari S, Li X, Sangaiah AK (2018) An elliptic curve cryptography based lightweight authentication scheme for smart grid communication. Futur Gener Comput Syst 81:557–565
Funding
No funds, grants, or other support was received.
Author information
Authors and Affiliations
Contributions
Chandan Trivedi wrote the main manuscript and carried out a literature survey, design scheme, mathematical proof, and security analysis. Keyur Parmar and Udai Pratap Rao have verified and edited mathematical proof, proposed scheme and performance analysis, and reviewed the paper.
Corresponding author
Ethics declarations
Ethics approval
Yes.
Consent to participate
Yes.
Consent to publication
Yes.
Competing interests
The authors declare no competing interests.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Trivedi, C., Parmar, K. & Rao, U.P. PGASH: Provable group-based authentication scheme for Internet of Healthcare Things. Peer-to-Peer Netw. Appl. 17, 665–684 (2024). https://doi.org/10.1007/s12083-023-01611-9
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12083-023-01611-9