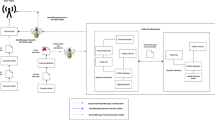
Abstract
Wireless Sensor Networks (WSNs) consist of numerous sensor nodes, each sensor nodes are equipped with limited resources. WSNs are strategically distributed throughout an environment to continuously monitor, and measure physical and natural parameters such as temperature, humidity, and motion. In the deployed environment, gathered data from the sensor nodes are transmitted to a remote server or Base Station (BS) using multi-hop communication. WSNs are applied in diverse domains such as agriculture, healthcare monitoring, environmental monitoring, and target tracking. However, the sensor nodes, being tiny and deployed in harsh environments, face energy constraints due to limited battery life and the difficulty of recharging or replacing batteries. Therefore, enhancing the energy efficiency and providing security in WSNs is a critical challenge. In the proposed work, Honey Badger Optimization Algorithm (HBO) is employed to provide to elect cluster head (CH) to optimize the energy consumption of network. Remora optimization Algorithm (RO) is employed to discover optimal path during routing in the network. Moreover, the proposed protocol employs Identity based Digital Signature with Conditional Privacy Preservation Algorithm (IDS-CPPA) to provide efficient authentication among the nodes in the networks. The effectiveness of the proposed protocol is implemented by using the NS3 simulator. The simulation results shows that proposed protocol improves average energy efficiency by 13%, packet delivery ratio by 10%, end to end delay by 15%, network lifetime by 17% and network throughput by 13% when it is compared with other existing protocols. Moreover, the proposed protocol improves the Quality of Service (QoS) parameters such as energy efficiency, throughput, packet delivery ratio, network lifetime, and latency and provides better security to the nodes which can withstand various types of attacks in the network.

















Similar content being viewed by others
Data availability
No datasets were generated or analysed during the current study.
References
Babu N, Kumar SVN (2022) Comprehensive analysis on sensor node fault management schemes in wireless sensor networks. Int J Commun Syst 35(18):e5342
Kandris D, Nakas C, Vomvas D, Koulouras G (2020) Applications of wireless sensor networks: an up-to-date survey. Appl Syst Innov 3(1):14
Haseeb K, Ud Din I, Almogren A, Islam N (2020) An energy efficient and secure IoT-based WSN framework: an application to smart agriculture. Sensors 20(7):2081
Gao Q, Gadekallu TR (2022) Design of telemedicine information query system based on wireless sensor network. EAI Endorsed Trans Pervasive Health Technol 8(4)
Salim A, Osamy W, Aziz A, Khedr AM (2022) SEEDGT: secure and energy efficient data gathering technique for IoT applications based WSNs. J Netw Comput Appl 202:103353
Narayan V, Daniel AK, Chaturvedi P (2023) E-FEERP: enhanced fuzzy based energy efficient routing protocol for wireless sensor network. Wireless Pers Commun 1–28
Balamurugan A, Janakiraman S, Priya MD, Malar ACJ (2022) Hybrid Marine predators optimization and improved particle swarm optimization-based optimal cluster routing in wireless sensor networks (WSNs). China Commun 19(6):219–247
Lakshmanna K, Subramani N, Alotaibi Y, Alghamdi S, Khalafand OI, Nanda AK (2022) Improved metaheuristic-driven energy-aware cluster-based routing scheme for IoT-assisted wireless sensor networks. Sustainability 14(13):7712
Sankar S, Somula R, Parvathala B, Kolli S, Pulipati S (2022) SOA-EACR: Seagull optimization algorithm based energy aware cluster routing protocol for wireless sensor networks in the livestock industry. Sustain Comput: Inf Syst 33:100645
Hao S, Hong Y, He Y (2022) An energy-efficient routing algorithm based on greedy strategy for energy harvesting wireless sensor networks. Sensors 22(4):1645
Kumar A, Webber JL, Haq MA, Gola KK, Singh P, Karupusamy S, Alazzam MB (2022) Optimal cluster head selection for energy efficient wireless sensor network using hybrid competitive swarm optimization and harmony search algorithm. Sustain Energy Technol Assess 52:102243
Maivizhi R, Yogesh P (2022) Fuzzy routing for in-network aggregation in wireless sensor networks. Peer Peer Netw Appl 15(1):592–611
Logambigai R, Kannan A (2016) Fuzzy logic based unequal clustering for wireless sensor networks. Wireless Netw 22:945–957
Rami Reddy M, Ravi Chandra ML, Venkatramana P, Dilli R (2023) Energy-efficient cluster head selection in wireless sensor networks using an improved grey wolf optimization algorithm. Computers 12(2):35
Dattatraya KN, Ananthakumaran S (2022) Energy and trust efficient cluster head selection in wireless sensor networks under meta-heuristic model. In: Expert Clouds and Applications: Proceedings of ICOECA 2022. Springer Nature Singapore, Singapore, pp 715–735
Behera TM, Samal UC, Mohapatra SK, Khan MS, Appasani B, Bizon N, Thounthong P (2022) Energy-efficient routing protocols for wireless sensor networks: architectures, strategies, and performance. Electronics 11(15):2282
Thahniyath G, Jayaprasad M (2022) Secure and load balanced routing model for wireless sensor networks. J King Saud Univ-Comput Inform Sci 34(7):4209–4218
Han Y, Hu H, Guo Y (2022) Energy-aware and trust-based secure routing protocol for wireless sensor networks using adaptive genetic algorithm. IEEE Access 10:11538–11550
Chander B, Kumaravelan G (2023) An improved 2-Factor authentication scheme for WSN based on ECC. IETE Tech Rev 40(2):167–178
Teng Z, Du C, Li M, Zhang H, Zhu W (2022) A wormhole attack detection algorithm integrated with the node trust optimization model in WSNs. IEEE Sens J 22(7):7361–7370
Lata S, Mehfuz S, Urooj S, Alrowais F (2020) Fuzzy clustering algorithm for enhancing reliability and network lifetime of wireless sensor networks. IEEE Access 8:66013–66024
Rai AK, Daniel AK (2023) FEEC: fuzzy based energy efficient clustering protocol for WSN. Int J Syst Assur Eng Manag 14(1):297–307
Santhosh Kumar SVN, Palanichamy Y, Selvi M, Ganapathy S, Kannan A, Perumal SP (2021) Energy efficient secured K means based unequal fuzzy clustering algorithm for efficient reprogramming in wireless sensor networks. Wireless Netw 27:3873–3894
Sekaran K, Rajakumar R, Dinesh K, Rajkumar Y, Latchoumi TP, Kadry S, Lim S (2020) An energy-efficient cluster head selection in wireless sensor network using grey wolf optimization algorithm. TELKOMNIKA (Telecommunication Comput Electron Control) 18(6):2822–2833
Selvi M, Santhosh Kumar SVN, Ganapathy S, Ayyanar A, Khanna Nehemiah H, Kannan A (2021) An energy efficient clustered gravitational and fuzzy based routing algorithm in WSNs. Wireless Pers Commun 116:61–90
Wang C (2023) A distributed particle-swarm-optimization-based fuzzy clustering protocol for wireless sensor networks. Sensors 23(15):6699
Goumiri S, Riahla MA, Hamadouche MH (2023) A novel approach for enhancing routing in wireless sensor networks using ACO algorithm. Emirates J Eng Res 28(3):1
Poonguzhali PK, Ananthamoorthy NP (2020) Improved energy efficient WSN using ACO based HSA for optimal cluster head selection. Peer Peer Netw Appl 13:1102–1108
Hosseinzadeh M, Ahmed OH, Lansky J, Mildeova S, Yousefpoor MS, Yousefpoor E, Yoo J, Tightiz L, Rahmani AM (2023) A cluster-tree-based trusted routing algorithm using grasshopper optimization algorithm (GOA) in wireless sensor networks (WSNs). PLoS ONE 18(9):e0289173
Selvi M, Thangaramya K, Ganapathy S, Kulothungan K, Khannah Nehemiah H, Kannan A (2019) An energy aware trust based secure routing algorithm for effective communication in wireless sensor networks. Wireless Pers Commun 105:1475–1490
Shende DK, Sonavane SS (2020) CrowWhale-ETR: CrowWhale optimization algorithm for energy and trust aware multicast routing in WSN for IoT applications. Wireless Netw 26:4011–4029
Altuwairiqi M (2023) An optimized multi-hop routing protocol for wireless sensor network using improved honey badger optimization algorithm for efficient and secure QoS. Comput Commun 214:244–259
Qureshi SG, Shandilya SK (2021) Novel fuzzy based crow search optimization algorithm for secure node-to-node data transmission in WSN. Wireless Pers Commun 127(1):577–597
Dinarvand N, Barati H (2019) An efficient and secure RFID authentication protocol using elliptic curve cryptography. Wireless Netw 25(1):415–428
Shah S, Munir A, Waheed A, Alabrah A, Mukred M, Amin F, Salam A (2023) Enhancing security and efficiency in underwater wireless sensor networks: a lightweight key management framework. Symmetry 15(8):1484
Dai C, Xu Z (2022) A secure three-factor authentication scheme for multigateway wireless sensor networks based on elliptic curve cryptography. Ad Hoc Netw 127:102768
Kumar V, Ray S (2022) Pairing-free identity-based digital signature algorithm for broadcast authentication based on modified ECC using battle royal optimization algorithm. Wireless Pers Commun 123(3):2341–2365
Hashim FA, Houssein EH, Hussain K, Mabrouk MS, Al-Atabany W (2022) Honey badger algorithm: new metaheuristic algorithm for solving optimization problems. Math Comput Simul 192:84–110
Pointcheval D, Stern J (2000) Security arguments for digital signatures and blind signatures. J Cryptol 13(3):361–396
Alghamdi WY, Wu H, Kanhere SS (2017) Reliable and secure end-to-end data aggregation using secret sharing in wsns. In: 2017 IEEE Wireless Communications andNetworking Conference (WCNC). IEEE, pp 1–6
Dinesh K, Santhosh Kumar SVN (2024) Energy-efficient trust-aware secured neuro-fuzzy clustering with sparrow search optimization in wireless sensor network. Int J Inf Secur 23:199–223. https://doi.org/10.1007/s10207-023-00737-4
Funding
None.
Author information
Authors and Affiliations
Contributions
All the authors have contributed in equal manner.
Corresponding author
Ethics declarations
Ethics approval
Authors provide the ethical approval for the given manuscript.
Consent to publish
All the authors gave permission for consent to publish.
Competing interest
The authors declare no competing interests.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This article is part of Topical Collection: Special Issue on 2 - Track on Security and Privacy
Guest Editor: Rongxing Lu
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Dinesh, K., Santhosh Kumar, S.V.N. HBO-SROA: Honey Badger optimization based clustering with secured remora optimization based routing algorithm in wireless sensor networks. Peer-to-Peer Netw. Appl. 17, 2609–2636 (2024). https://doi.org/10.1007/s12083-024-01708-9
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12083-024-01708-9