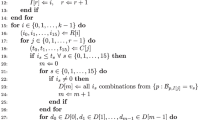Abstract
The algebraic immunity of cryptographic Boolean functions with odd number of variables is studied in this paper. Proper modifications of functions with maximum algebraic immunity are proved that yield new functions whose algebraic immunity is also maximum. Several results are provided for both the multivariate and univariate representation, and their applicability is shown on known classes of Boolean functions. Moreover, new efficient algorithms to produce functions of guaranteed maximum algebraic immunity are developed, which further extend and generalize well-known constructions in this area. It is shown that high nonlinearity as well as good behavior against fast algebraic attacks are also achievable in several cases.
Similar content being viewed by others
References
Armknecht, F., Carlet, C., Gaborit, P., Künzli, S., Meier, W., Ruatta, O.: Efficient computation of algebraic immunity for algebraic and fast algebraic attacks. In: Advances in Cryptology - Eurocrypt 2006. Lecture Notes in Computer Science, vol. 4004, pp. 147–164. Springer-Heidelberg (2006)
Braeken, A., Preneel, B.: On the algebraic immunity of symmetric Boolean functions. In: Advances in Cryptology - Indocrypt 2005. Lecture Notes in Computer Science, vol. 3797, pp. 35–48. Springer-Heidelberg (2005)
Canteaut, A.: Open problems related to algebraic attacks on stream ciphers. International Workshop on Coding and Cryptography (WCC), pp. 1–11 (2005)
Carlet, C., Dalai, D.K., Gupta, K.C., Maitra, S.: Algebraic immunity for cryptographically significant Boolean functions: analysis and construction. IEEE Trans. Inf. Theory 52, 3105–3121 (2006)
Carlet, C.: Constructing balanced functions with optimum algebraic immunity. In: Proc. IEEE Int. Symp. Inf. Theory (ISIT), pp. 451–455 (2007)
Carlet, C., Feng, K.: An infinite class of balanced functions with optimal algebraic immunity, good immunity to fast algebraic attacks and good nonlinearity. In: Asiacrypt 2008. Lecture Notes in Computer Science, vol. 5350, pp. 425–440. Springer-Heidelberg (2008)
Carlet, C., Gaborit, P.: On the construction of balanced Boolean functions with a good algebraic immunity. In: Proc. IEEE Int. Symp. Inf. Theory (ISIT), pp. 1101–1105 (2005)
Carlet, C., Zeng, X., Li, C., Hu, L.: Further properties of several classes of Boolean functions with optimum algebraic immunity. Designs Codes Cryptogr. 52, 303–338 (2009)
Carlet, C.: Comments on constructions of cryptographically significant Boolean functions using primitive polynomials. IEEE Trans. Inf. Theory 57, 4852–4853 (2011)
Chen, Y., Lu, P.: Two classes of symmetric Boolean functions with optimum algebraic immunity: construction and analysis. IEEE Trans. Inf. Theory 57, 2522–2538 (2011)
Cormen, T.H., Leiserson, C.E., Rivest, R.L.: Introduction to Algorithms. MIT Press (1990)
Courtois, N., Meier, W.: Algebraic attacks on stream ciphers with linear feedback. In: Advances in Cryptology - Eurocrypt 2003. Lecture Notes in Computer Science, vol. 2656, pp. 345–359. Springer-Heidelberg (2003)
Courtois, N.: Fast algebraic attacks on stream ciphers with linear feedback. In: Advances in Cryptology - Crypto 2003. Lecture Notes in Computer Science, vol. 2729, pp. 176–194. Springer-Heidelberg (2003)
Dalai, D.K., Maitra, S., Sarkar, S.: Basic theory in construction of Boolean functions with maximum possible annihilator immunity. Designs Codes Cryptogr. 40, 41–58 (2006)
Du, Y., Zhang, F.G.: Finding more Boolean functions with maximum algebraic immunity based on univariate polynomial representation. In: ACISP 2011. Lecture Notes in Computer Science, vol. 6812, pp. 47–60. Springer-Heidelberg (2011)
Du, Y., Zhang F.: On the existence of Boolean functions with optimal resistance against fast algebraic attacks. Cryptology ePrint Archive, Report 2012/210 (2012). Available http://eprint.iacr.org
ECRYPT. D. STVL.9, Ongoing research areas in symmetric cryptography, ECRYPT Deliverable (2008)
Li, N., Qi, W.: Construction and analysis of Boolean functions of 2t + 1 variables with maximum algebraic immunity. In: Advances in Cryptology - Asiacrypt 2006. Lecture Notes in Computer Science, vol. 4284, pp. 84–98. Springer-Heidelberg (2006)
Li, N., Qu, L., Qi, W., Feng, G., Li, C., Xie, D.: On the construction of Boolean functions with optimal algebraic immunity. IEEE Trans. Inf. Theory 54, 1330–1334 (2008)
Liu, M., Zhang, Y., Lin, D.: Perfect algebraic immune functions. Cryptology ePrint Archive, Report 2012/212 (2012). Available http://eprint.iacr.org
MacWilliams, F.J., Sloane, N.J.A.: The Theory of Error Correcting Codes. North-Holland, Amsterdam (1977)
Meier, W., Pasalic, E., Carlet, C.: Algebraic attacks and decomposition of Boolean functions. In: Advances in Cryptology - Eurocrypt 2004. Lecture Notes in Computer Science, vol. 3027, pp. 474–491. Springer-Heidelberg (2004)
Pasalic, E.: Almost fully optimized infinitive classes of Boolean functions resistant to (fast) algebraic cryptanalysis. In: ICISC 2008. Lecture Notes in Computer Science, vol. 5461, pp. 399–414. Springer-Heidelberg (2008)
Pasalic, E.: A design of Boolean functions resistant to (fast) algebraic cryptanalysis with efficient implementation. Cryptogr. Commun. 4, 25–45 (2012)
Qu, L., Li, C., Feng, K.: A note on symmetric Boolean functions with maximum algebraic immunity in odd number of variables. IEEE Trans. Inf. Theory 53, 2908–2910 (2007)
Qu, L., Feng, K., Liu, F., Wang, L.: Constructing symmetric Boolean functions with maximum algebraic immunity. IEEE Trans. Inf. Theory 55, 2406–2412 (2009)
Rizomiliotis, P.: On the resistance of Boolean functions against algebraic attacks using univariate polynomial representation. IEEE Trans. Inf. Theory 56, 4014–4024 (2010)
Sarkar, S., Maitra, S.: Construction of rotation symmetric Boolean functions on odd number of variables with maximum algebraic immunity. In: AAECC 2007. Lecture Notes in Computer Science, vol. 4851, pp. 271–280. Springer-Heidelberg (2007)
Siegenthaler, T.: Correlation-immunity of nonlinear combining functions for cryptographic applications. IEEE Trans. Inf. Theory 30, 776–780 (1984)
Wang, C., Chen, X.: On extended algebraic immunity. Designs Codes Cryptogr. 57, 271–281 (2010)
Wang, Q., Peng, J., Kan, H.: Constructions of cryptographically significant Boolean functions using primitive polynomials. IEEE Trans. Inf. Theory 56, 3048–3053 (2010)
Zeng, X., Carlet, C., Shan, J., Hu, L.: More balanced Boolean functions with optimal algebraic immunity and good nonlinearity and resistance to fast algebraic attacks. IEEE Trans. Inf. Theory 57, 6310–6320 (2011)
Acknowledgements
This research has been co-financed by the European Union (European Social Fund – ESF) and Greek national funds through the Operational Program “Education and Lifelong Learning” of the National Strategic Reference Framework (NSRF) - Research Funding Program THALIS: Secure wireless nonlinear communications at the physical layer.
Author information
Authors and Affiliations
Corresponding author
Additional information
Part of this work has been presented at the IEEE Int’l Symp. Inform. Theory (ISIT), St. Petersburg, Russia, July 31–August 6, 2011. A new section with constructions of functions based on their univariate representation has been added, whereas the results based on the multivariate representation have been extended. Moreover, the behavior of the constructions against fast algebraic attacks is also discussed in a new section.
Rights and permissions
About this article
Cite this article
Limniotis, K., Kolokotronis, N. & Kalouptsidis, N. Secondary constructions of Boolean functions with maximum algebraic immunity. Cryptogr. Commun. 5, 179–199 (2013). https://doi.org/10.1007/s12095-013-0081-2
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12095-013-0081-2