Abstract
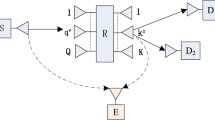
In the wireless channel state information (CSI)-assisted amplify-and-forward (AF) networks, an instantaneous CSI of the first hop is required to scale the amplification gain. However, the deployment of instantaneous CSI always remains difficult in real applications because it increases the CSI overhead and causes resources wastage such as power and bandwidth. In order to reduce the CSI overhead and the system complexity, we suggest the integration of semi-blind relay in secure non-orthogonal multiple access (NOMA) systems where only a statistical CSI of the first hop is used to generate the amplification gain. This paper addresses the performance analysis of the secure semi-blind AF-NOMA (S-SBAF-NOMA) schemes in which the base station communicates with a pair of users via a semi-blind relay node in the presence of one eavesdropper. First, we provide the expressions for the end-to-end signal-to-noise ratio (SNR) at each receiver node. We then derive new analytical and asymptotic expressions for strictly positive secrecy capacity (SPSC) and secrecy outage probability (SOP). To ensure the exactness and the tractability of mathematical analysis, we provide some numerical results obtained through simulation rounds in Matlab, and we compare them with those of secure CSI-assisted AF-NOMA (S-CSIAF-NOMA) networks. Our results show that the proposed S-SBAF-NOMA scheme achieves comparable secrecy performance/same performance bounds as compared to S-CSIAF-NOMA scheme at the gain of a decrease in processing complexity and system overhead. Numerical results also demonstrate that S-SBAF-NOMA networks achieve superior secrecy performance for lower values of target data rates and SNR of the illegal link.






Similar content being viewed by others
References
Hu S, Yu B, Qian C, Xiao Y, Xiong Q, Sun C, Gao Y (2018) Nonorthogonal interleave-grid multiple access scheme for industrial internet of things in 5G network. IEEE Trans Ind Inform 14(12):5436–5446
Islam SMR, Avazov N, Dobre OA, Kwak K-S (2017) Power-domain non-orthogonal multiple access (NOMA) in 5G systems: potentials and challenges. IEEE Commun Surv Tutor 19(2):721–742
Wu Q, Chen W, Ng DWK, Schober R (2018) Spectral and energy-efficient wireless powered IoT networks: NOMA or TDMA? IEEE Trans Veh Technol 67(7):6663–6667
Islam SMR, Zeng M, Dobre OA, Kwak K-S (2018) Resource allocation for downlink NOMA systems: key techniques and open issues. IEEE Trans Veh Technol 25(2):40–47
Ding Z, Yang Z, Fan P, Poor HV (2014) On the performance of non-orthogonal multiple access in 5G systems with randomly deployed users. IEEE Signal Process Lett 21(12):1501–1505
Li Y, Li T, Li Y, Pervaiz H, Ni Q (2022) Outage performance enhancement for NOMA-based cooperative relay sharing networks. IEEE Wirel Commun Lett 11(12):2665–2669
Mobini Z, Mohammadi M, Tsiftsis TA, Ding Z, Tellambura C (2022) New antenna selection schemes for full-duplex cooperative MIMO-NOMA systems. IEEE Trans Commun 70(7):4343–4358
Hamza AA, Dayoub I, Alouani I, Amrouche A (2022) On the error rate performance of full-duplex cooperative NOMA in wireless networks. IEEE Trans Commun 70(3):1742–1758
Huang R, Wan D, Ji F, Qing H, Li J, Yu H, Chen F (2020) Performance analysis of NOMA-based cooperative networks with relay selection. China Commun 17(11):111–119
Hadj Alouane W (2019) Power allocation for asymmetric two-way fixed-gain AF relaying networks. Telecommun Syst 71
Hadj Alouane W, Boujemaa H (2018) Multi-way semi-blind AF relaying networks over Rayleigh fading channels. Phys Commun 30:43–49
Hu C, Wang H, Song R (2021) Group successive interference cancellation assisted semi-blind channel estimation in multi-cell massive MIMO-NOMA systems. IEEE Commun Lett 25(9):3085–3089
Shaikh MA, Manzar A, Moinuddin M, Rehman SU, Mustafa H (2022) Semi-blind beamforming in beam space MIMO NOMA for mmWave communications. IEEE Access 10:120426–120435
Hadj Alouane W, Boujemaa H (2020) Cooperative jamming AF networks via Nakagami-m fading channels. Trans Emerg Telecommun 31(6):e3790
Nguyen TN, Tran D-H, Van Chien T, Phan V-D, Nguyen N-T, Voznak M, Chatzinotas S, Ottersten B, Poor HV (2023) Physical layer security in AF-based cooperative SWIPT sensor networks. IEEE Sens J 23(1):689–705
Amin I, Mishra D, Saini R, Aïssa S (2022) Secrecy rate maximization in relay-assisted NOMA with untrusted users. In: 2022 IEEE 33rd Annual International Symposium on Personal, Indoor and Mobile Radio Communications (PIMRC). pp 1134–1138
Cao K, Wang B, Ding H, Li T, Gong F (2020) Optimal relay selection for secure NOMA systems under untrusted users. IEEE Trans Veh Technol 69(2):1942–1955
Hadj Alouane W (2021) Physical layer security for cooperative NOMA networks via Nakagami-m fading channels. Telecomm Syst
Yu C, Ko H-L, Peng X, Xie W (2019) Secrecy outage performance analysis for cooperative NOMA over Nakagami- \(m\) channel. IEEE Access 7:79866–79876
Alouane WH (2019) Secure semi-blind AF relaying networks using multiple eavesdroppers. In: 2019 15th International Wireless Communications and Mobile Computing Conference (IWCMC). pp 549–554
Chen J, Yang L, Alouini M-S (2018) Physical layer security for cooperative NOMA systems. IEEE Trans Veh Technol 67(5):4645–4649
Saito Y, Kishiyama Y, Benjebbour A, Nakamura T, Li A, Higuchi K (2013) Non-orthogonal multiple access (NOMA) for cellular future radio access. In: 2013 IEEE 77th Vehicular Technology Conference (VTC Spring). pp 1–5
Ding Z, Liu Y, Choi J, Sun Q, Elkashlan M, Chih-Lin I, Poor HV (2017) Application of non-orthogonal multiple access in LTE and 5G networks. IEEE Commun Mag 55(2):185–191
Ding Z, Dai L, Poor HV (2016) MIMO-NOMA design for small packet transmission in the internet of things. IEEE Access 4:1393–1405
Patel CS, Stuber GL, Pratt TG (2006) Statistical properties of amplify and forward relay fading channels. IEEE Trans Veh Technol 55(1):1–9
Ding Z, Liu Y, Choi J, Sun Q, Elkashlan M, Chih-Lin I, Poor HV (2017) Application of non-orthogonal multiple access in LTE and 5G networks. IEEE Commun Mag 55(2):185–191
Liu Y, Qin Z, Elkashlan M, Gao Y, Hanzo L (2017) Enhancing the physical layer security of non-orthogonal multiple access in large-scale networks. IEEE Trans Wirel Commun 16(3):1656–1672
Qin Z, Liu Y, Ding Z, Gao Y, Elkashlan M (2016) Physical layer security for 5G non-orthogonal multiple access in large-scale networks, In: 2016 IEEE International Conference on Communications (ICC). pp 1–6
Hasna M, Alouini M-S (2004) A performance study of dual-hop transmissions with fixed gain relays. IEEE Trans Wirel Commun 3(6):1963–1968
Abramowitz M, Stegun IA (eds) (1970) Handbook of mathematical functions with formulas, graphs, and mathematical tables, 9th edn. U.S. Government Printing Office, New York, Dover
Leung-Yan-Cheong S, Hellman M (1978) The Gaussian wire-tap channel. IEEE Trans Inform Theory 24(4):451–456
Roy SD, Kundu S, Kumar A, Sharma S (2016) Secrecy outage probability with destination assisted jamming in presence of an untrusted relay. 2016 IEEE Annual India Conference (INDICON), pp 1–5
Liu X (2013) Probability of strictly positive secrecy capacity of the Rician-Rician fading channel. IEEE Wireless Commun Lett 2(1):50–53
Hayat B (2020) Bodacious-instance coverage mechanism for wireless sensor network. Wireless Commun Mobile Comput 2020:11
Ashraf S, Ahmad A, Ullah A, Feng C, Khan M, Adnan M, Nazir S, Khan H (2020) Towards an improved energy efficient and end-to-end secure protocol for IoT healthcare applications. Secur Commun Netw 2020
Ashraf S, Ahmed T, Saleem S (2021) NRSM: node redeployment shrewd mechanism for wireless sensor network. Iran J Comput Sci 4:1–13
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The author declares no competing interests.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Hadj Alouane, W. Semi-blind AF transmission in secure NOMA systems. Ann. Telecommun. 79, 315–325 (2024). https://doi.org/10.1007/s12243-023-00989-0
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12243-023-00989-0