Abstract
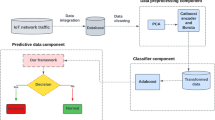
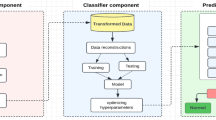
Smart cities leverage technologies such as Cloud computing, the Internet of Things (IoT), artificial intelligence (AI), and data analytics to collect and analyze data on various aspects of city life, including transportation, energy usage, public safety, and environmental factors. In such an environment, security is important to protect the data collected by various devices and systems from unauthorized access or misuse. Intrusion Detection Systems (IDS) are critical components of cyber security, designed to identify and prevent malicious activities on computer networks. Machine learning (ML) techniques have emerged as a promising approach to enhance IDS performance by automating the detection of anomalies and reducing false positives. This paper provides an overview of IDS systems and reviews some of the most popular ML algorithms used in IDS. A REPOStack model is proposed, which is a hybrid of Recursive Feature Elimination (RFE), Self-Adaptive Equilibrium Optimizer with Particle Swarm Optimization (SAEO_PSO), and Probabilistic Stacked Ensemble of Adaboost, Support Vector Machine (SVM), Deep Neural Network (DNN), and XGBoost. Adboost, SVM, and DNN are used as base learners, and XGboost is used as a meta-learner. REPOStack is tested on benchmark datasets NSLKDD, UNSW-NB15, and CICIDS. The results show improved accuracy, sensitivity, precision, specificity, and F1 score.











Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Data availability
The datasets generated and analyzed during the current study are publicly available at: NSLKDD- https://www.kaggle.com/datasets/hassan06/nslkdd UNSWNB-15- https://research.unsw.edu.au/projects/unsw-nb15-dataset CICIDS- https://www.kaggle.com/datasets/cicdataset/cicids2017
References
Ahmad Z, Shahid Khan A, Wai Shiang C, Abdullah J, Ahmad F (2021) Network intrusion detection system: a systematic study of machine learning and deep learning approaches. Trans Emerg Telecommun Technol 32(1):e4150
Ahmed HA, Hameed A, Bawany NZ (2022) Network intrusion detection using oversampling technique and machine learning algorithms. PeerJ Comput Sci 8:e820
Ali YA, Awwad EM, Al-Razgan M, Maarouf A (2023) Hyperparameter search for machine learning algorithms for optimizing the computational complexity. Processes 11(2):349
Alloghani M, Al-Jumeily D, Mustafina J, Hussain A, Aljaaf AJ (2020) A systematic review on supervised and unsupervised machine learning algorithms for data science. In: Supervised and unsupervised learning for data science, pp 3–21
Apruzzese G, Pajola L, Conti M (2022) The cross-evaluation of machine learning-based network intrusion detection systems. IEEE Trans Netw Serv Manag 19:5152–5169
Balakrishnan K, Dhanalakshmi R, Akila M, Sinha BB (2022) Improved equilibrium optimization based on levy flight approach for feature selection. Evol Syst 14:1–12
Bangui H, Ge M, Buhnova B (2022) A hybrid machine learning model for intrusion detection in VANET. Computing 104(3):503–531
Chen T, He T, Benesty M, Khotilovich V, Tang Y, Cho H, Chen K, Mitchell R, Cano I, Zhou T et al (2015) Xgboost: eXtreme gradient boosting. R package version 0.4-2 1(4):1–4
Choudhary S, Kesswani N (2020) Analysis of KDD-CUP’99, NSL-KDD and UNSW-NB15 datasets using deep learning in IoT. Procedia Comput Sci 167:1561–1573
Fan Q, Huang H, Yang K, Zhang S, Yao L, Xiong Q (2021) A modified equilibrium optimizer using opposition-based learning and novel update rules. Expert Syst Appl 170:114575
Faramarzi A, Heidarinejad M, Stephens B, Mirjalili S (2020) Equilibrium optimizer: a novel optimization algorithm. Knowl Based Syst 191:105190
Ghazal TM (2022) Data fusion-based machine learning architecture for intrusion detection. Comput Mater Contin 70(2):3399–3413
Gill KS, Saxena S, Sharma A (2020) GTM-CSec: game theoretic model for cloud security based on IDS and honeypot. Comput Secur 92:101732
Horchulhack P, Viegas EK, Santin AO (2022) Toward feasible machine learning model updates in network-based intrusion detection. Comput Netw 202:108618
Khraisat A, Gondal I, Vamplew P, Kamruzzaman J (2019) Survey of intrusion detection systems: techniques, datasets and challenges. Cybersecurity 2(1):1–22
Kurani A, Doshi P, Vakharia A, Shah M (2023) A comprehensive comparative study of artificial neural network (ANN) and support vector machines (SVM) on stock forecasting. Ann Data Sci 10(1):183–208
Li Y, Liu Q (2021) A comprehensive review study of cyber-attacks and cyber security; emerging trends and recent developments. Energy Rep 7:8176–8186
Lian W, Nie G, Jia B, Shi D, Fan Q, Liang Y (2020) An intrusion detection method based on decision tree-recursive feature elimination in ensemble learning. Math Probl Eng 1–15:2020
Mittal S (2020) A survey on modeling and improving reliability of DNN algorithms and accelerators. J Syst Archit 104:101689
Moustafa N, Slay J, Creech G (2017) Novel geometric area analysis technique for anomaly detection using trapezoidal area estimation on large-scale networks. IEEE Trans Big Data 5(4):481–494
Osei-kwakye J, Han F, Amponsah AA, Ling Q, Abeo TA (2022) A hybrid optimization method by incorporating adaptive response strategy for feedforward neural network. Connect Sci 34(1):578–607
Saheed YK, Abiodun AI, Misra S, Holone MK, Colomo-Palacios R (2022) A machine learning-based intrusion detection for detecting internet of things network attacks. Alex Eng J 61(12):9395–9409
Schapire RE (2013) Explaining AdaBoost. In: Empirical inference: Festschrift in honor of Vladimir N. Vapnik, pp 37–52
Sengan S, Khalaf OI, Sharma DK, Hamad AA et al (2022) Secured and privacy-based ids for healthcare systems on e-medical data using machine learning approach. Int J Reliab Qual E-Healthc (IJRQEH) 11(3):1–11
Shami TM, El-Saleh AA, Alswaitti M, Al-Tashi Q, Summakieh MA, Mirjalili S (2022) Particle swarm optimization: a comprehensive survey. IEEE Access 10:10031–10061
Sharafaldin I, Lashkari AH, Ghorbani AA (2018) Toward generating a new intrusion detection dataset and intrusion traffic characterization. ICISSp 1:108–116
Shaukat K, Luo S, Varadharajan V, Hameed IA, Xu M (2020) A survey on machine learning techniques for cyber security in the last decade. IEEE Access 8:222310–222354
Singh A, Amutha J, Nagar J, Sharma S, Lee C-C (2002) AutoML-ID: automated machine learning model for intrusion detection using wireless sensor network. Sci Rep 12(1):9074
Tavallaee M, Bagheri E, Lu W, Ghorbani AA (2009) A detailed analysis of the KDD CUP 99 data set. In: 2009 IEEE symposium on computational intelligence for security and defense applications, IEEE. pp 1–6
Verkerken M, D’hooge L, Wauters T, Volckaert B, De Turck F (2022) Towards model generalization for intrusion detection: unsupervised machine learning techniques. J Netw Syst Manag 30:1–25
Yan X (2020) A review of cyber security risks of power systems: from static to dynamic false data attacks. Prot Control Mod Power Syst 5(1):19
Yao R, Wang N, Chen P, Ma D, Sheng X (2022) A CNN-transformer hybrid approach for an intrusion detection system in advanced metering infrastructure. Multimedia Tools Appl 82:19463–19486
Funding
This research received no specific grant from any funding agency in the public, commercial, or not-for-profit sectors.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
Authors declare that they have no conflict of interest.
Ethical approval
This article does not contain any study on human participants or animals performed by any of the authors
Research data policy
In conducting our research, we have utilized existing datasets obtained from https://www.kaggle.com/datasets/hassan06/nslkdd (NSLKDD), https://research.unsw.edu.au/projects/unsw-nb15-dataset (UNSWNB-15), and https://www.kaggle.com/datasets/cicdataset/cicids2017 (CICIDS). We are committed to upholding ethical standards, ensuring data integrity, and adhering to legal regulations governing the use of these datasets.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Gill, K.S., Dhillon, A. A hybrid machine learning framework for intrusion detection system in smart cities. Evolving Systems 15, 2005–2019 (2024). https://doi.org/10.1007/s12530-024-09603-7
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12530-024-09603-7