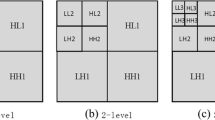
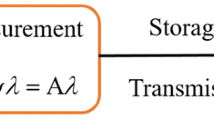
Abstract
As an important tool for protecting multimedia contents, scrambling and randomizing of original messages is used in generating digital watermark for satisfying security requirements. Based on the neural perception of high-dimensional data, compressed sensing (CS) is proposed as a new technique in watermarking for improved security and reduced computational complexity. In our proposed methodology, watermark signal is extracted from the CS of the Hadamard measurement matrix. Through construction of the scrambled block Hadamard matrix utilizing a cryptographic key, encrypting the watermark signal in CS domain is achieved without any additional computation required. The extensive experiments have shown that the neural inspired CS mechanism can generate watermark signal of higher security, yet it still maintains a better trade-off between transparency and robustness.
















Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.References
Miller ML, Doerr GJ, Cox IJ. Applying informed coding and embedding to design a robust high-capacity watermark. IEEE Trans Image Process. 2004;13(6):792–807.
Biswas S, Das R, Petriu M. An adaptive compressed MPEG-2 video watermarking scheme. IEEE Trans Instrum Meas. 2005;54(5):1853–61.
Cox IJ, Kiliam I, Leighton FT, Shamoon T. Secure spread spectrum watermarking for multimedia. IEEE Transaction on Image Processing. 1997;6(12):1673–87.
Voyatzis G, Pitas I. Chaotic watermarks f or embedding in the spatial domain. In Proceedings of ICIP’98, Chicago, IL, Oct. 1997, pp. 432–436.
Huang HY, Yang CH, Hsu WH. A Video Watermarking Technique Based on Pseudo-3-D DCT and Quantization Index Modulation. IEEE Trans Inf Forensics Secur. 2010;5(4):625–7.
Gao X, Deng C, Li X, Tao D. Local Feature Based Geometric-Resistant Image Information Hiding. Cognitive Computation. 2010;2(2):68–77.
Cayre F, Fontaine C, Furon T. Watermarking security: theory and practice. IEEE Transaction on Signal Processing. 2005;53(10):3976–87.
Fallahpour M, Shirmohammadi S, Semsarzadeh M, Zhao J. Tampering detection in compressed digital video using watermarking. IEEE Transaction on Instrumentation and Measurement. 2014;63(5):1057–72.
Ganguli S, Sompolinsky H. Compressed sensing, sparsity and dimensionality in neuronal information processing and data analysis. Annu Rev Neurosci. 2012;35:485–508.
Olshausen BA, Field DJ. Emergence of simple-cell receptive field properties by learning a sparse code for natural images. Nature. 1996;381:607–8.
Aghagolzadeh M, Oweiss K. Compressed and distributed sensing of neuronal activity for real time spike train decoding. IEEE Trans. Neural System Rehability Engineering. 2009;17(2):116–28.
Eldawlatly S, Jin R, Oweiss KG. Identifying functional connectivity in large-scale neural ensemble recordings: a multiscale data mining approach. Neural Comput. 2009;21(2):450–77.
Kim S, Kwon S, Kweon IS. A perceptual visual feature extraction method achieved by imitating V1 and V4 of the human visual system. Cognitive Computation. 2013;5(4):610–28.
Li Z. Theoretical understanding of the early visual processes by data compression and data selection. Network: Computation in Neural Systems. 2006;17(4):301–34.
Hunt J, Dayan P, Goodhill G. Sparse coding can predict primary visual cortex receptive field changes induced by abnormal visual input. PLoS Comput Biol. 2013;9(5). Article number: e1003005.
Schwartz O, Hsu A, Dayan P. Space and time in visual context. Nat Rev Neurosci. 2007;8:522–35.
Orsdemir A, Altun HO, Sharma G, Bocko MF. On the security and robustness of encryption via compressed sensing. In: IEEE Military Communicaiton Conference. 2008. pp. 1040–1046.
Davenport M, Boufounos P, Wakin M, Baraniuk R. Signal processing with compressive measurements. IEEE Journal of Selected Topics in Signal Processing. 2010;4(2):445–60.
Lu W, Varna AL, Wu M. Security analysis for privacy preserving search for multimedia. In: Proceedings of IEEE 17th international conference on image processing. 2010.
Calderbank R, Jafarpour S, Schapire R. Compressed learning: universal sparse dimensionality deduction and learning in the measurement domain. http://dsp.rice.edu/sites/dsp.rice.edu/files/cs/. 2009.
Hsu D, Kakade SM, Langford J, Zhang T. Multi-label prediction via compressed sensing. In: Neural information processing systems (NIPS). 2009.
Zhao CH, Liu W. Block compressive sensing based image semi-fragile zero-watermarking algorithm. Acta Autom Sin. 2012;38(4):609–17.
Zhang X, Qian Z, Ren Y, Feng G. Watermarking with flexible self-recovery quality based on compressive sensing and compositive reconstruction. IEEE Transaction on Information Forensics and Security. 2011;6(4):1223–32.
Wang Q, Zeng W, Tian J. “Integrated secure watermark detection and privacy preserving storage in the compressive sensing domain”, IEEE International Workshop on Information Forensics and Security. China: Guangzhou; 2013. p. 67–72.
Zhao HM, Lai JH, Cai J, Chen XL. A Video Watermarking Algorithm for Intraframe Tampering Detection Based Compressed Sensing. Acta Electronica Sinica. 2013;41(6):1153–8.
Donoho D. Compressed sensing. IEEE Transaction on Information Theory. 2006;52(4):1289–306.
Donoho DL, Tsaig Y. Extensions of compressed sensing. Sig Process. 2006;86(3):533–48.
Candes E, Wakin M. An introduction to compressive sampling. IEEE Signal Process Mag. 2008;25(2):21–30.
Fowler JE, Mun SW, Tramel EW. Multiscale block compressed sensing with smoothed projected landweber reconstruction. In: 19th European signal processing conference (EUSIPCO 2011), Barcelona, Aug 29–Sep 2. 2011, pp. 564–568.
Ni K, Datta S, Mahanti P, Roudenko S, Cochran D. Efficient Deterministic Compressed Sensing for Images with Chirps and Reed-Muller Codes. SIAM Journal on Imaging Sciences. 2011;4(3):931–53.
Rachlin Y, Baron D. The secrecy of compressed sensing measurements. In: Proceedings of the 46th annual allerton conference in communication, control and computing, Illinois, USA. 2008, pp. 813–817.
Huang HY, Yang CH, Hsu WH. A video watermarking technique based on Pseudo-3-D DCT and quantization index modulation. IEEE Trans Inf Forensics Secur. 2010;5(4):625–7.
Seo YS, Kim WG, Huh YH, Oh WG, Hwang CJ. QIM watermarking for image with tow adaptive quantization step-sizes. In: Proceedings of 9th international conference on advanced communication technology. 2007, pp. 997–800.
Fingerprint verification competition. http://bias.csr.unibo.it/fvc2004/.
Kong W, Yang B, Wu D, Niu X. SVD based blind video watermarking algorithm. In: Proceedings of first international conference on innovative computing, information and control. 2006, pp. 265–268.
Sachnev V, Ramasamy S, Sundaram S, et al. A cognitive ensemble of extreme learning machine for steganalysis based on risk-sensitive hinge loss function. Cognitive Computation. 2015;7(1):103–10.
Xu J, Yang G, Yin Y, Man H, He H. Sparse-representation-based classification with structure-preserving dimension reduction. Cognitive Computation. 2014;6(3):608–21.
Acknowledgments
The authors would like to thank the editors and the anonymous reviewers for their constructive comments to further improve the quality of this paper. We’d also great thank the support from the National Natural Science Foundation of China under Grant 61272381, Key Reserach and Development Project of Guangdong Province (grant 2014KZDXM060) and Natural Science Foundation of Guangdong, China (grant 2015A030313672).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Zhao, H., Ren, J. Cognitive Computation of Compressed Sensing for Watermark Signal Measurement. Cogn Comput 8, 246–260 (2016). https://doi.org/10.1007/s12559-015-9357-5
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12559-015-9357-5